Summary Report - the-binary, A Denial of Service Agent
May 27, 2002
Background
Recently, an unauthorized piece of software was recently discovered on
one of the computers in the Honeynet project's experimental network.
The program was found only in its compiled, binary form, and no source
code was found to aid in determining the purpose of the program.
A reverse engineering effort was conducted in an attempt to determine the
purpose of the binary and detail its capabilities. The results and
effective countermeasures would be shared with the computer security community
at large.
This summary will briefly explain:
-
Motive for installing this program on the Honeynet system
-
The means by which this program may have been installed on the system
-
The capabilities of the program
-
How to detect and how to remove this program from infected systems
Denial of Service Attack Tools
Reverse engineering efforts identified this program as an "agent"
component of a Distributed Denial of Service (DDoS) network. A DDoS
network is a collection of compromised computers on which components of
a DDoS system have been placed. These components, when activated
by a malicious user, act in concert to deny a victim access to some resource
or service. A simple example of a denial of service attack would
be overwhelming a web based business, Amazon.com for instance, with bogus
connection requests. While the servers are busy handling the malicious
requests, legitimate customers might find it difficult to connect, possibly
resulting in lost revenue. Another example of a denial of service
might be flooding a corporate mail server with connection requests in order
to slow and perhaps even stop its performance. The resulting slowdown
in corporate communications could possibly wreak havoc on the company's
ability to perform its mission.
Denial of Service Networks
In order for an attacker to launch an attack of sufficient magnitude to
bring high-powered servers to their knees, an attacker will generally attempt
to create an army of computers that will, upon command, generate volumes
of traffic directed at a target system potentially disrupting normal functions
of the target system. An attacker will typically seek to compromise
as many accessible systems as possible in order to install DDoS tools and
to construct a DDoS army. Using compromised systems has several advantages
to the attacker:
-
When the attack is launched, it will be conducted from machines other than
the attacker's and will not tie up the attacker's resources
-
The target system will fall under attack from many directions, making it
difficult, if not impossible, to trace the
 attack back to its single point of origin.
attack back to its single point of origin.
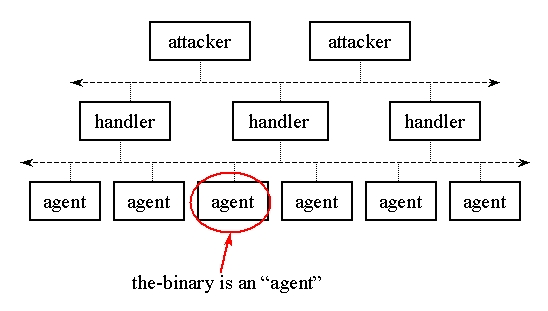
A small snapshot of a typical DDoS network is shown to the right. A small
number of attaskers control a pyramid structure of handlers, which in turn
control an even larger layer of agents. The agents act as a force
multiplier for the attacker. On command from the attacker and via
the handlers, the agents launch a coordinated attack against a single target.
The attack generally attempts to consume some resource on the target machine,
making it unavailable for its intended purpose.
Construction of The DDoS Network
An attacker constructs a DDoS network by taking control of as many computers
as possible. This usually takes place by exploiting known vulnerabilities
in operating systems or applications. With each newly exploited system,
the attacker extends the attack network. In many cases, gaining control
of one computer can lead to the exploitation of additional systems.
In highly automated attacks, an attacker's initial exploit may be self-propagating,
and preprogrammed to launch a DoS attack at a specific time and against
a specific target. The Code Red worm, which propagated via a vulnerability
in the Microsoft IIS web server, is an example of such an automated tool
whose eventual goal was to launch a denial of service attack against www.whitehouse.gov.
"the-binary", the topic of this summary, has no self-propagating properties.
It does, however require root privileges in order to execute properly,
and one can assume that if this program is found running on a system, the
computer has been fully compromised.
Capabilities of the-binary
This particular program offers its owner (handler) several capabilities.
The main functions are highlighted below
-
Control commands utilize "Network Voice Protocol II" IP headers
-
A status reporting capability that allows the handler to remotely determine
the current state of the program
-
Result reporting to as many as 10 handlers
-
Execution of any command on the infected system with output of the command
optionally sent to designated handlers
-
Initiation and termination of any of 5 different styles of packet flooding
DoS attacks. Floods, once initiated continue indefinitely until terminated
by the handler. Packet floosing options include:
-
Flood a target with DNS responses, which are generally allowed through
a firewall unless the firewall is "stateful" and has failed to see the
originating DNS query.
-
Flood a target with TCP connection requests without following up and completing
the connection, causing the target to go through a lengthy time-out process
before resetting to await a new connection. (TCP SYN Flood)
-
Flood a target DNS server with DNS queries.
-
Flood a target with ICMP Echo requests (Ping Flood)
-
Flood a target with UDP packets directed at a specific port.
-
Attempts to hide itself in ps listings by renaming itself after
it starts ("[mingetty]")
Detection and Removal
A significant sustained increase in network traffic is a strong indication
that a DoS tool is active within your network. With this particular
tool, a simple network sniffer, such as ethereal or tcpdump, will be able
to provide the MAC address from which the DDoS attack is originating.
"the-binary" makes no attempt to disguise itself at the ethernet address
level MAC spoofing), though it does do IP address spoofing. A simple
scanning
tool is available to scan class C subnets for the presence of active
the-binary
agents. Once a machine is determined to contain the tool, the binary
file can be located on that machine by grep'ing for the string "TfOjG",
which is the encoded version of the backdoor password. It should
be assumed that any machine found to contain this program has been fully
compromised, and appropriate incident response measures should be instituted
for each infected machine.
Defense
Defense against "the-binary" takes on three forms
-
Keep system security patches up-to-date on all systems so that no system
in your network becomes an agent system.
-
Perform egress filtering on border routers so that packets containing spoofed
IP addresses are dropped. This will keep your network from contributing
substantially to a DoS should one of your machines become compromised.
-
At your firewall, deny all protocols that are not in use on your network.
Once you have configured any rules for allowed protocols, make sure you
deny any other protocols by default.
-
Perform rate limiting on incoming connections from the same IP address
Useful Sites for Additional DDoS Information
Denial of Service Attack
- The SANS Institute
Distributed
Denial of Service (DDoS) Attacks/Tools - David Dittrich, University
of Washington
 attack back to its single point of origin.
attack back to its single point of origin. attack back to its single point of origin.
attack back to its single point of origin.