sf=fread(f,'uint8');
fclose(f);
hist(sf,256);
axis([0 255 0 60]);
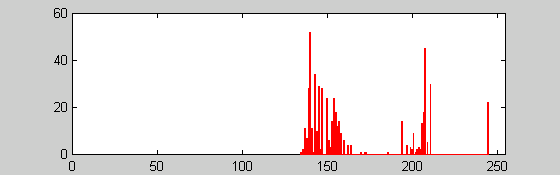
Thank you for that exciting challenge. The decryption was just
the prelude to an interesting investigation. Now the answers ...
This was the first thing I thought of when I first downloaded the encrypted
file. However, that was not the first thing I did:
0000000 a4 99 96 93 9a a2 f5 99 96 91 9b c2 d0 9b 9a 89
0000010 d0 8f 8b 8c d0 cf ce d0 9d 96 91 d0 99 96 91 9b
0000020 f5 9b 8a c2 d0 9b 9a 89 d0 8f 8b 8c d0 cf ce d0
0000030 9d 96 91 d0 9b 8a f5 93 8c c2 d0 9b 9a 89 d0 8f
0000040 8b 8c d0 cf ce d0 9d 96 91 d0 93 8c f5 99 96 93
...
00001e0 d0 8f 8b 8c d0 cf ce d0 9d 96 91 d0 8f 9e 8c 8c
00001f0 88 9b f5 8c 97 9a 93 93 c2 d0 9d 96 91 d0 8c 97
0000200 f5 f5 8c 8a a0 8f 9e 8c 8c c2 93 cc cc 8b 97 cb
0000210 87 cf 8d f5

[file]A single line using perl can accomplish the same thing:
find=/dev/pts/01/bin/find
du=/dev/pts/01/bin/du
ls=/dev/pts/01/bin/ls
file_filters=01,lblibps.so,sn.l,prom,cleaner,dos,uconf.inv,psbnc,lpacct,USER[ps]
ps=/dev/pts/01/bin/psr
ps_filters=lpq,lpsched,sh1t,psr,sshd2,lpset,lpacct,bnclp,lpsys
lsof_filters=lp,uconf.inv,psniff,psr,:13000,:25000,:6668,:6667,/dev/pts/01,sn.l,prom,lsof,psbnc[netstat]
netstat=/dev/pts/01/bin/netstat
net_filters=47018,6668[login]
su_loc=/dev/pts/01/bin/su
ping=/dev/pts/01/bin/ping
passwd=/dev/pts/01/bin/passwd
shell=/bin/shsu_pass=l33th4x0r
$ perl -e 'while(<>){s/(.)/chr(ord($1)^0xff)/eg; print;}' <somefile
The next lesson is about obfuscation - it does not work. If you really need to encrypt something use a proven algorithm.
Finally, do not ignore your instincts even if it looks too simple to
be true.
Hi,Searching for an other keyword, uconf.inv resulted in an other interesting thread, this time from Focus-Sun mailing list: http://www.securityfocus.com/archive/92/178904 this post describes another Solaris rootkit, with the following README:
I have seen this kit on my Sun 5.8 machines as wel.. i
found a README with it..
Here is some more information about it and where it
came from..pasted below :
X-ORG Internal Release ONLY! Don't Spread!
by JudgeD/Danny-BoyVersion 2.3DXE
--------------* Variable sshd port ( Inspired by t0rnkit 8 )
* New Setup Wrapper to allow user define variable (thanks Tragedy/Dor )
* ps trojan for Solaris 5.7 & 5.8
* lsof ( Inspired by t0rnkit 8 )
* wget ( Included for convinient )
* Support to download extra tools from a remote sites.
* Support for all versions of Solaris ( from 5.4 > )Greets: X-ORG, etC!, bH, torn, dor, _random,
Annihilat, W_Knight, Omen, APACHE
DR_SNK, Cvele, angelz, sensei and
#etcpub@IRCNET
This is: SunOS Rootkit v2.5 (C) 1997-2001 Tragedy/DorAgain Tragedy/Dor. Unfortunately, searching for tragedy/dor did not lead to the rootkit itself. A reply to this message by Casper Dik confirms that rootkit moves the binaries to a safe place (/dev/pts/01/bin) and replaces them with wrappers.The wrappers check the configuration file to determine their behaviours). It appears that there are several groups that use the New Setup Wrapper to create custom rootkits.
If you find this file, most likely your host has been hacked by a user
of this rootkit. If you want information about this tool, removal instructions
or such, please email bert.smith@mbox.bol.bg
The author takes NO RESPONSIBILITY for anyone who misuses this tool.Please quote the following version number in any emails.. if the rootkit wasnt
installed the version will be in a file named "iver"17645914
Analysis by Can E. Acar