Scan of the Month 27 Analysis
The Honeynet Project Scan of the Month
Analysis performed by Anders Amandusson
<anders dot amandusson at sca dot com >
April 24th 2003
Mission
The Challenge:
In early March 2003, the Azusa Pacific University Honeynet Project deployed an unpatched Windows 2000 honeypot
having a null (blank) administrative password.
During its first week of operation, the honeypot was repeatedly compromised by attackers and worms exploiting
several distinct vulnerabilities. Subsequent to a succesful attack, the honeypot was joined to a large botnet.
During operation of the honeypot, a total of 15,164 distinct hosts were seen entering the botnet.
The challenge is based on logs from five days of honeypot operation, collected using Snort.
The logs have been edited to remove irrelevant traffic and combined into a single file.
Also, IP addresses and certain other information have been obfuscated so that the identity of the honeynet is
not readily apparent. Your mission is to analyze the log file in order to answer the questions below.
Summery
The server was among other thing targetet by the W32/Deloder worm that also dropped the ircbot on the server. The ircbot tried to connect to 5 different IRC servers until it was accepted by the 5th.
One attack used the same flaw as the Deloder worm uses (testing Administrator passwords on TCP 445 (Windows 2000 SMB over TCP instead of NetBIOS)) and uploaded a remote admin tool (remote Administrator Server v2.1).
Frequent but not successful attempts were made by the SQLsnake and W32.SQLExp worms.
A massive web vulnerability scan was performed after a port scan.
There were a couple of other tools (forensic acquisition utilities-1.0.0.1030(beta1), ZipCentral and fport) downloaded via http but since there were no other communication to the server the previous 2 ½ hours before the download I assumed they were fetched by an administrator.
Tools used
Ethereal 0.8.20
Snort 1.9.0
Answers
Even though I consider myself a beginner in the forensics area I will try to answer the intermediate questions as well.
File downloaded from http://www.honeynet.org/misc/files/sotm27.gz
C:\PROGRA~1\md5>md5 c:\download\sotm\sotm27.gz
MD5 (c:\download\sotm\sotm27.gz) = b4bfc10fa8346d89058a2e9507cfd9b9
C:\PROGRA~1\md5>
Beginning Questions
What is IRC?
Internet Relay Chat - It's a worldwide multi-user chat system. A user can connect to a specific channel and "talk" to the other participants. Either in groups or in private conversations.
What message is sent by an IRC client when it asks to join an IRC network?
To connect to an IRC server the following messages are send:
Command: PASS
Parameters: <password>
Command: NICK
Parameters: <nickname> [ <hopcount> ]
Command: USER
Parameters: <username> <hostname> <servername> <realname>
Example:
NICK rgdiuggac.
USER rgdiuggac localhost localhost :rgdiuggac.
To join a specific channel:
Command: JOIN
Parameters: {,} [{,}]
Example:
JOIN #x
What is a botnet?
A bot is a scripted IRC "user". It is used to manage access lists, run quizzes or serve files in the channels.
They are automated and controlled by events (usually commands given in a channel).
A botnet on the other hand is something different.
It could be described as a channel full of bots, most of them unaware of their presence because of an infection by a Trojan horse.
It could have been distributed to the client PC wrapped in another file and run whenever that file is executed, send as an attachment, downloaded from a website or like in this case, delivered by a worm. A botmaster (could be called a botnet administrator) is handling the channels giving commands to the infected clients.
What are botnets commonly used for?
It can be used (and are used) for launching Denial of Service attacks. As a botnet can consist of 1000-nds of infected bots, this will be a very effective DDoS Attack.
The botmaster can use channel commands to make the bots spam other channels with a website that has the Trojan on it to make even more bots.
He/she could also be able to launch attacks against other channels, or get the bots to send him the nickname passwords.
What TCP ports does IRC generally use?
6667
What is a binary log file and how is one created?
The binary log file is generated by a packet logger, for example snort or tcpdump (or windump).
Digital data communication is a stream of binary digits, it would be best to keep the logged
communication in the same format.
That is, the log file is just an exact copy of what the communication looked like when it passed. This way nothing is lost.
To analyze the binary log file a tool is used to translate the binary data to something readable for humans (for example Ethereal or snort).
What IRC servers did the honeypot, which has the IP address 172.16.134.191, communicate with?
| 209.126.161.29 | Owned by California Regional Internet, Inc |
| 66.33.65.58 | ns.espaciosweb.net |
| 63.241.174.144 | irc4.aol.com |
| 217.199.175.10 | ns2.caralarmuk.com |
| 209.196.44.172 | ipdwbc0271atl2.public.registredsite.com |
Here’s a screenshot showing the connections in the logfile.
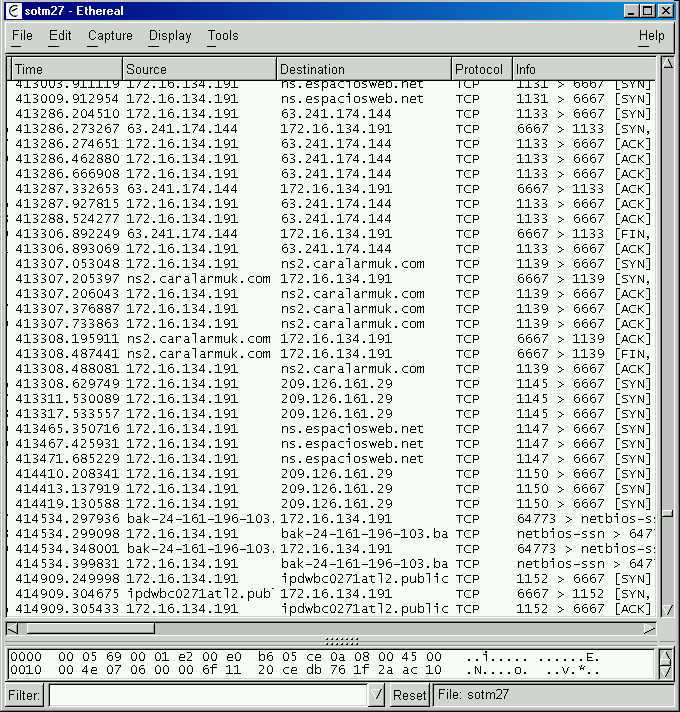
During the observation period, how many distinct hosts accessed the botnet associated with the server having IP address 209.196.44.172?
When the honeynet server connected, the IRC server claimed there were 4752 Global users (max 4765). But it also said there were 346 connected local users (of 348 possible slots).
But the Challenge stated:
"During operation of the honeypot, a total of 15,164 distinct hosts were seen entering the botnet"
I'm using snort to extract a readable part of the logfile to see the IRC parts.
C:\download\sotm>c:\snort\snort.exe -dvr sotm27 port 6667 > logfil.txt
The client also does a WHO command, which lists the names of all connected users.
An extract of the logfile.txt can be found here.
There are 4752 distinct hosts.
Assuming that each botnet host has a 56 kbps network link, what is the aggregate bandwidth of the botnet?
4752 * 56 kbps = 259,875 Mbps ~ 260 Mbps
Intermediate Questions
What IP source addresses were used in attacking the honeypot?
I separated all sources to different logs for easier analysis.
C:\download\sotm>c:\snort\snort.exe -dvr sotm27 -l c:\snort\log -h 172.16.134.191/1
Source | Attack |
24.197.194.106 | - Port scan
- All kinds of web attacks (frontpage extensions, default scripts, known web related vulnerabilities such as web folder traversal and others).
|
210.22.204.101 | - Attacked TCP 445 and uploaded Remote Administrator Server v2.1 (view log extract).
Date: 03/05 Time: 04:39:02 - 04:40:14 - Tried to use Microsoft Indexing server vulnerability. (MS01-033)
- Lots of traffic is flowing from 172.16.134.191:4899 to this machine. This should be the radmin communication. Radmin may use 128-bit encryption. (http://www.radmin.com)
- TCP 99 access a lot
|
61.111.101.78 | - W32/Deloder-A worm attacked and infected server.
Date: 03/06 Time: 05:35:34 - 05:38:29 - Commands used by infection: (those I could find)
- Copy inst.exe to \winnt\system32\inst.exe
- Attrib.exe –r inst.exe
- Inst.exe
- Attrib.exe –r Devlr32.exe
- Devlr32.exe
- Net share /delete C$ /y
- Net share /delete D$ /y
- Net share /delete E$ /y
- Net share /delete ADMIN$ /y
|
12.252.61.161
12.253.142.87
12.83.147.97
200.135.228.10
200.50.124.2
205.180.159.35
213.122.77.74
216.229.73.11
217.35.65.9
218.244.66.32
218.4.48.74
218.4.65.115
218.92.13.142
219.145.211.132
24.167.221.106
24.74.199.10
44.33.244.44
61.132.88.50
61.132.88.90
61.134.45.19
61.150.120.72
61.150.72.7
61.177.56.98
61.177.62.66
61.185.212.166
61.185.215.42
61.185.242.190
61.185.29.9
61.203.104.148
61.8.1.64
66.233.4.225
66.81.131.17
67.201.75.38
67.81.161.166
68.37.54.69
68.45.123.130
68.84.210.227
81.57.217.208 | - SQL scan (UDP 1434) Probably W32.SQLExp.Worm
|
129.116.182.239 | - Attacked TCP 445 and tried to access the sam file and the attacker received a list of local users.
- DNS probe
- TCP 1433 scan, SQLsnake Worm check?
- TCP 139 probe
|
141.149.155.249
144.134.109.25
162.33.189.252
164.125.76.48
168.226.98.61
195.67.251.197
200.60.202.74
200.66.98.107
200.78.103.67
202.63.162.34
203.115.96.146
207.6.77.235
208.186.61.2
210.12.211.121
210.203.189.77
210.214.49.227
210.58.0.25
212.110.30.110
213.107.105.72
213.116.166.126
213.217.55.243
213.44.104.92
213.7.60.57
213.84.75.42
216.170.214.226
217.1.35.169
217.222.201.82
217.227.245.101
217.227.98.82
218.163.9.89
218.237.70.119
218.87.178.167
219.118.31.42
219.94.46.57
24.161.196.103
4.64.221.42
61.14.66.92
61.140.149.137
61.155.126.150
61.177.154.228
61.55.71.169
62.194.4.114
62.201.96.159
62.251.129.118
64.17.250.240
64.254.203.68
66.190.67.122
66.73.160.240
68.115.33.110
68.152.53.138
68.154.11.82
81.202.125.5
81.50.177.167 | - TCP 139 probe (tried to map \\PC0191\C)
- UDP 137 probe
|
141.85.37.78
203.170.177.8 | |
148.235.82.146
203.106.55.12
211.149.57.197
216.228.8.158
219.65.37.37
24.107.117.237
61.11.11.54
62.127.38.198
66.92.135.108
81.114.77.37 | |
169.254.205.177
172.168.0.154
209.45.125.110 | |
192.130.71.66
213.23.49.158 | |
192.215.160.106
210.111.56.66 | - TCP 1433 scan , SQLsnake Worm check?
|
195.36.247.77 | - TCP 139 probe
- Attacked TCP 445 and tried to access the sam file and the attacker received a list of local users.
|
199.107.7.2 | - 172.16.134.191 probe from port 4828 to 31337 (Back Orifice)
|
200.74.26.73 | |
204.50.186.37
212.243.23.179 | - TCP 111 (Sun RPC Portmapper)
|
209.126.161.29
209.196.44.172
217.199.175.10
63.241.174.144
66.33.65.58 | - From 172.16.134.191 to TCP 6667 (IRC)
|
209.45.125.69
66.139.10.15
80.181.116.202 | - TCP 139 probe
- TCP 445 probes
|
218.25.147.83 | - .ida Microsoft Indexing Server attack
|
62.150.170.134
62.150.170.232 | - UDP 28431 Hack’A’Tack probe
|
64.0.96.9
65.57.83.13
68.169.174.108 | - Accessed while downloading Flash
|
66.8.163.125 | - TCP 139 probe
- TCP 445 probes
- Http OPTIONS method probe
|
Other more or less interesting events (logfile extract):
Access from 210.22.204.101 to 172.16.134.191 on port 4899 (radmin) was conducted until 03/05-04:48:22.370000 210.22.204.101:3313 -> 172.16.134.191:4899.
Between this event and the software downloads above there were only one sunrpc probe and 3 W32.SQLExp.Worm probes.
As there are no other communication to 172.16.134.191 for 2 ½ hours before the downloads, my guess would be that it was a valid administrator who downloaded these tools.
- 03/06-05:38:29.840686 61.111.101.78:1697 -> 172.16.134.191:445.
The last packet of the W32/Deloder-A worm has arrived.
The first try to connect to an IRC server was made 6min and 50sec later.
03/06-05:45:19.604225 172.16.134.191:1129 -> 66.33.65.58:6667.
This is not so surprising as the W32/Deloder-A worm is supposed to drop an ircbot (Worm description).
It's just another proof that it is the Deloder worm.
What vulnerabilities did attackers attempt to exploit?
- There were a lot of attempt on the web server from 24.197.194.106. It was trying to use installed scripts, dll's and executables (default IIS scripts, frontpage extensions ...) to reach \winnt\system32\cmd.exe and \winnt\repair\sam. A not identified tool was used for this attack.
- Single specific attack on “Unchecked Buffer in Index Server ISAPI Extension Could Enable Web Server Compromise” (MS01-033)
- Attack on tcp 445 trying administrator passwords (both W32/Deloder-A worm and manual attacks)
- W32.SQLExp.Worm using the vulnerabilities “Elevation of Privilege in SQL Server Web Tasks” (MS02-061) and “Buffer Overruns in SQL Server 2000 Resolution Service Could Enable Code Execution” (MS02-039)
- SQLsnake Worm is attacking checking for systems where:
- “sa” SQL server account has no password
- SQL is running with Administrative access
- NetBIOS probes for shares
- FTP probes
- Proxy probe
- Back Orifice probe
Which attacks were successful?
- Some attacks on TCP 445 were successful resulting in:
- The W32/Deloder-A worm from 61.111.101.78 was successfully executed and server connected to botnet.
- Remote Administrator Server v2.1 was successfully uploaded by 210.22.204.101.
General Questions (not judged)
What did you learn about analysis as a result of studying this scan?
I think that I have leared something more about network comminications but also a better knowledge of how to read the log files.
I can handle the tools (ethereal and snort) better, even though I still have very much to learn.
I would like to think that I have increased my ability in putting things together to drawing conclusions (but I still need much more experience in this area and hopefully I’m not completely wrong).
How do you anticipate being able to apply your new knowledge and skills?
The most obvious situation would be to apply this knowledge whenever investigating incidents of our own. I also think that I would be able to use this skill and knowledge in my day-to-day work, as I don’t think that there is such a thing as unnecessary knowledge (There might be things you don’t want to know, but that’s a different thing).
How can we improve the SotM challenge? What would you like to see added? What would you like to see done differently?
I like the mix between beginners and advanced level of the challenges. That way experienced people might find some challenges interesting and beginners like me can also increase our experience both by solving easier challenges as well as reading the reports of the more advanced challenges.
I haven't been participating long enough to name anything I would like to see different yet.
Thanks for this possibility to learn.
Anders Amandusson
