Examination Report
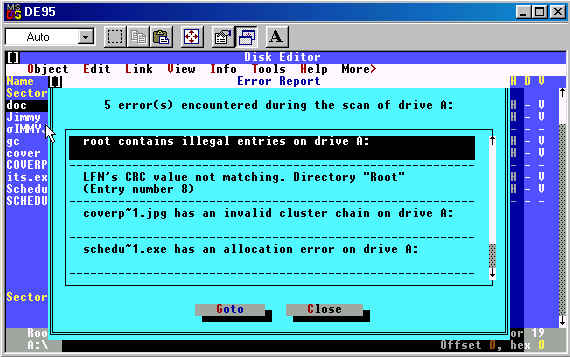
The MD5 hash value of the original file was checked and verified, and the image was restored to a wiped and formatted 3 ˝ inch floppy disk. The disk is write-protected and then examined using Norton’s Diskedit for DOS. Upon opening the disk for examination in Diskedit, the following errors on the disk are noted:
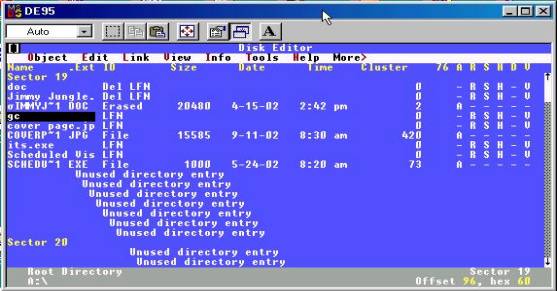
The directory structure as viewed in Diskedit shows the file entries as follows
The deleted file Jimmy Jungle.doc can be recovered using Norton Unerase for DOS. When recovered the document contains the following:
________________________________________________________________________
Jimmy
Jungle
626
Jungle Ave Apt 2
Jungle,
NY 11111
Jimmy:
Dude,
your pot must be the best – it made the cover of High Times Magazine! Thanks
for sending me the Cover Page. What do you put in your soil when you plant the
marijuana seeds? At least I know your growing it and not some guy in Columbia.
These
kids, they tell me marijuana isn’t addictive, but they don’t stop buying from
me. Man, I’m sure glad you told me about targeting the high school students.
You must have some experience. It’s like a guaranteed paycheck. Their parents
give them money for lunch and they spend it on my stuff. I’m an entrepreneur.
Am I only one you sell to? Maybe I can become distributor of the year!
I
emailed you the schedule that I am using. I think it helps me cover myself and
not be predictive. Tell me what you
think. To open it, use the same password that you sent me before with that
file. Talk to you later.
Thanks,
Joe
Cover Page.jpg
This file contains the cover photo referred to in the Jimmy.doc. The significance of this file, however lies in the file slack.

The file slack contains the following data, which could only have been placed there deliberately:
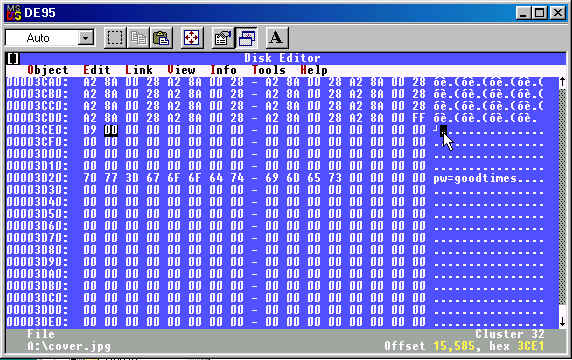
The arrow in this slide indicates the point at which the cover.jpg file ends and the file slack begins. This data was located by running the utility “strings” against the image file. The data pw=goodtimes was located in the output of the linux utility, “strings” It was then located on the disk by searching for the string under Diskedit.
The last file on the disk is the file “Scheduled Visits.exe” This file showed an allocation error when the disk was scanned in Diskedit. Moving to the start of the file data, it is first observed that the header contains “PK” indicating that the file is a zip file. If the file is copied from the disk as is, and renamed to Scheduled Visits.zip, it cannot be opened, and returns an error. It is known that he format of PKZip files includes a directory in plain text near the end of the file, which is not present in the first 1000 bytes of this file, the size indicated in the directory entry. Examining the contiguous sectors after the apparent end of file, the zip file contents entry is located at offset 2,378 from the start of the file.
Checking the FAT table entry for this file, we find that the file actually occupies 5 sectors, while the original filesize of 1000 bytes as indicated in the directory would have included only 2 sectors. Moving to cluster 77, we find the directory data for the zip file.
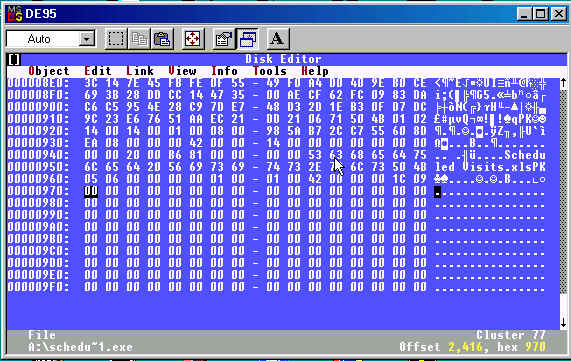
This slide shows the end of file for the “Scheduled Visits.exe” file. The end of file is located by comparing other .ZIP files. It is found that the end of file occurs 20 bytes after the the last “PK” string in the zip file. When this data is recovered using the end of file at offset 2387, and renamed to “Scheduled Visits.zip”, it can be opened using WinZip or Powerarc. Using the password “goodtimes” will unlock the zip file and reveal the “Scheduled Visits.xls” spreadsheet as below.
|
Month |
DAY |
HIGH
SCHOOLS |
|
2002 |
|
|
|
April |
Monday (1) |
Smith Hill High School
(A) |
|
|
Tuesday (2) |
Key High School (B) |
|
|
Wednesday (3) |
Leetch High School (C)
|
|
|
Thursday (4) |
Birard High School (D) |
|
|
Friday (5) |
Richter High School
(E) |
|
|
Monday (1) |
Hull High School (F) |
|
|
Tuesday (2) |
Smith Hill High School
(A) |
|
|
Wednesday (3) |
Key High School (B) |
|
|
Thursday (4) |
Leetch High School (C)
|
|
|
Friday (5) |
Birard High School (D) |
|
|
Monday (1) |
Richter High School
(E) |
|
|
Tuesday (2) |
Hull High School (F) |
|
|
Wednesday (3) |
Smith Hill High School
(A) |
|
|
Thursday (4) |
Key High School (B) |
|
|
Friday (5) |
Leetch High School (C)
|
|
|
Monday (1) |
Birard High School (D) |
|
|
Tuesday (2) |
Richter High School
(E) |
|
|
Wednesday (3) |
Hull High School (F) |
|
|
Thursday (4) |
Smith Hill High School
(A) |
|
|
Friday (5) |
Key High School (B) |
|
|
Monday (1) |
Leetch High School (C)
|
|
|
Tuesday (2) |
Birard High School (D) |
|
May |
|
|
|
|
Wednesday (3) |
Richter High School
(E) |
|
|
Thursday (4) |
Hull High School (F) |
|
|
Friday (5) |
Smith Hill High School
(A) |
|
|
Monday (1) |
Key High School (B) |
|
|
Tuesday (2) |
Leetch High School (C)
|
|
|
Wednesday (3) |
Birard High School (D) |
|
|
Thursday (4) |
Richter High School
(E) |
|
|
Friday (5) |
Hull High School (F) |
|
|
Monday (1) |
Smith Hill High School
(A) |
|
|
Tuesday (2) |
Key High School (B) |
|
|
Wednesday (3) |
Leetch High School (C)
|
|
|
Thursday (4) |
Birard High School (D) |
|
|
Friday (5) |
Richter High School
(E) |
|
|
Monday (1) |
Hull High School (F) |
|
|
|
|
|
|
Tuesday (2) |
Smith Hill High School
(A) |
|
|
Wednesday (3) |
Key High School (B) |
|
|
Thursday (4) |
Leetch High School (C)
|
|
|
Friday (5) |
Birard High School (D) |
|
|
Monday (1) |
Richter High School
(E) |
|
|
Tuesday (2) |
Hull High School (F) |
|
|
Wednesday (3) |
Smith Hill High School
(A) |
|
|
Thursday (4) |
Key High School (B) |
|
|
Friday (5) |
Leetch High School (C)
|
|
June |
|
|
|
|
Monday (1) |
Birard High School (D) |
|
|
Tuesday (2) |
Richter High School
(E) |
|
|
Wednesday (3) |
Hull High School (F) |
|
|
Thursday (4) |
Smith Hill High School
(A) |
|
|
Friday (5) |
Key High School (B) |
|
|
Monday (1) |
Leetch High School (C)
|
|
|
Tuesday (2) |
Birard High School (D) |
|
|
Wednesday (3) |
Richter High School
(E) |
|
|
Thursday (4) |
Hull High School (F) |
|
|
Friday (5) |
Smith Hill High School
(A) |
|
|
Monday (1) |
Key High School (B) |
|
|
Tuesday (2) |
Leetch High School (C)
|
|
|
Wednesday (3) |
Birard High School (D) |
|
|
Thursday (4) |
Richter High School
(E) |
|
|
Friday (5) |
Hull High School (F) |
|
|
Monday (1) |
Smith Hill High School
(A) |
|
|
Tuesday (2) |
Key High School (B) |
|
|
Wednesday (3) |
Leetch High School (C)
|
|
|
Thursday (4) |
Birard High School (D) |
|
|
Friday (5) |
Richter High School
(E) |
The Diskedit program revealed 5 errors on the disk when first opened. Once again, here is the list:

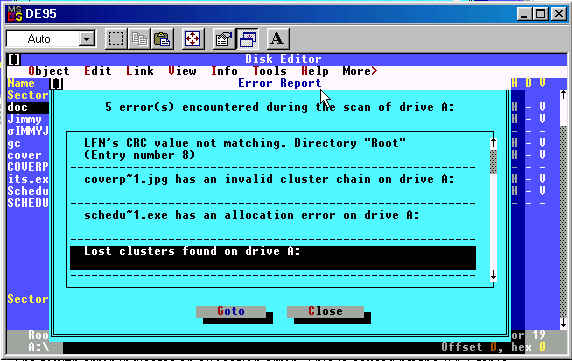
- The first error indicates that there are illegal entries in this directory. The long fileneame entry “cover page.jpgc” violates the 3 character extension convention for windows filenames, and is the likely cause of the error.
- The second error indicates that the CRC value of directory entry number 8 “Scheduled Visits.exe” does not match the CRC generated at the time the file was saved. This is caused by the altered filename in the directory. The filename was changed from the original .ZIP file entry to the .EXE entry, thereby causing the system to generate the CRC error. The CRC value is calculated on the “short” filename, the 8-dot-3 DOS convention filename. This is verified by the fact that the long filename “cover page.jpg” has been altered to “cover page.jpgc” while the 8.3 filename remained unaltered, and no directory entry CRC error was generated for the long filename entry.
- The third error shows that “cover page.jpg” has an invalid cluster chain, because the starting cluster has been changed to 420, from the true starting cluster of 42. The starting cluster 420 is shown as unallocated, but the directory entry does not indicate an erased file, and thereby causes this error.
- The fourth error indicates an allocation error. This is caused by the FAT table having 5 clusters allocated for the file, but the filesize indicating 1000 bytes, or 2 clusters.
- The fifth and last error indicates allocation errors on the disk, due to the fact that the FAT allocates cluster 42-73 without a corresponding directory entry. This entry, for “Scheduled Visits.exe” has actually been altered to make the starting cluster 420, thereby creating the “orphaned” allocated sectors, noted as “Lost Clusters” by Diskedit
Conclusions:
The deleted/recovered file Jimmy Jungle.doc provides us with the name and address of Joe’s supplier. The slack space of the Cover Page.jpg file contains the password “goodtimes”, and is the password for the “Scheduled Visits.zip” file described below. This information can be found by running “strings” against the entire image, or by extracting and textifying all file slack, or by search for the string “pw=”. This data was placed in the file slack deliberately, as RAM slack would have surely contained other text or binary data along with this string.
The file “Scheduled Visits.exe” is a password protected zip file that has been renamed to indicate that it is an executable in an effort to hide the data in the file. In addition, the directory entry for this file has been altered to indicate a filesize less than half of the actual filesize. The FAT table, however, contains proper entries for the allocated sectors of this file. By comparing the end of file offset of a zip file relative to the “PK” data near the end of file, we find that the file ends at an offset of 20 bytes after the last “PK” in the file. Recovering the data from the first “PK” to that offset, the entire file is recovered, and can be unzipped using the password “goodtimes”, revealing the spreadsheet that proves that the suspect was active at many schools.
The Jimmy Jungle.doc document was examined using the meta-data examination program “Catalogue”, and was found to be a Microsoft Word version 9, which is Word 2000, or Microsoft Office 2000.
Answers:
Question 1: The name and address of Joe Jacobs Supplier
Jimmy
Jungle
626
Jungle Ave Apt 2
Jungle, NY 11111
Question 2: Crucial Data from with the coverpage.jpg file
The password for the protected zip file “Scheduled Visits.zip” “goodtimes” This is not really contained in the file, but is rather in the file slack area after the end of the file.
Question 3: Other highschools frequented
See output of Scheduled Visits.zip
Question 4: For each file, methods taken to mask them
1. Jimmy Jungle.doc was simply erased, so that it would not show up in a directory listing for this disk
2. Cover Page.jpg had the directory entry deliberately changed, adding a “c” to the end of the long filename so that it would be unrecognizable as an image file. In addition, the starting cluster in the directory entry was changed to 420 from 42 so that the system would be unable to locate the file data.
3. “Scheduled Visits.zip” is a password-protected zip file of an Excel Spreadsheet. The file was password protected, zipped and saved to disk. The the directory entry was altered to indicate that the file was an executable, rather than a zip file
Question 5: What processes did I undertake to examine the contents of each file:
This question is answered in the preceding report
Question 6: What MS program created the Cover Page file
Microsoft Word version 9, Microsoft Office 2000, Microsoft Word 2000 (all the same program)
Editorial Comment: (feel free to edit out of report)
I used a number of different automated tools to view this disk initially. (I won’t name them, but they are known to all of you). None of those tools gave the clear picture of the directory entry structure that was required to work this problem. I don’t know where we lost it, but this visualization as provided by DiskEdit should be incorporated into all of our forensic tools. The ability to view the interpreted logical structures of the directory, FAT tables, boot sectors, physical and logical sectors, clusters, partition tables, et al. is essential to really understanding the structure of the disk, as opposed to the “Nintendo Forensics” of point and click examination tools.
Submitted 10/19/02 by
Bill Moylan
billyfm@optonline.net